“Cryptography is the standard of encrypting all the data and information by converting Plain text into cipher text for secure communication.”
Encryption is the key to secure all our data and information while we communicate with others over any transmission channel. Now, you might be thinking why this encryption matters a lot?
Data is something that is important in each field. It may include your personal identity, your financial stats, your bank account details, or anything else. No one wants that their data should be accessed by any unauthorized user. But unfortunately, there are adversaries present in the market to snatch that information in a very smart way.
There are a lot of hackers and unauthorized users who want access to public data, so they can mislead that information for their benefits. For this purpose, Cryptography standards were introduced to protect our data from such threats.
In this topic, we will cover what actually Cryptography is, how does it work, and what are its algorithm types. But before moving on, let us discuss some related terms:
- Plain Text: The message which we send to the receiver. For e.g.- “Hello”
- Cipher Text: Conversion of that plain text into a non-readable format. For e.g.- “H@#$5”
Now let’s start with the basics.
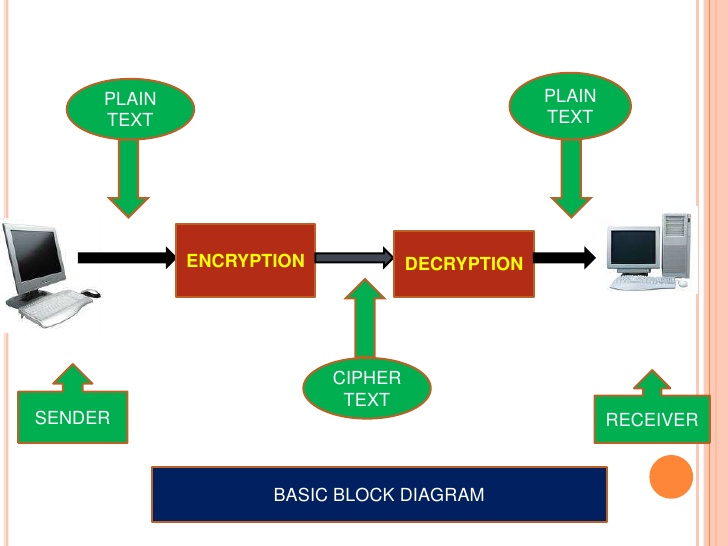
Now, suppose there is one sender A who wants to send a message to receiver B who is in the other part of the world. The sender obviously wants this message to be private and no one should access it except the receiver. Here, the only motive is to secure the communication.
The sender A will first convert its plain text message into cipher text (unreadable format) using a key. The message is then encrypted and now A sends this message to receiver B over any transmission media.
B now receives the message and will require a decryption key to decode the message into a readable format. He then uses the key and decrypts the message to find the original plain text.
This is how cryptography works and data is encrypted to secure them from external threats and attacks. There are several different types of cryptography algorithms with each different working methodologies to encrypt the data in the best possible way.
Types of Cryptography
Cryptography is further classified into three different categories:
- Symmetric Key Cryptography (Private/Secret Key Cryptography)
- Asymmetric Key Cryptography (Public Key Cryptography)
- Hash Function
Symmetric Key Cryptography
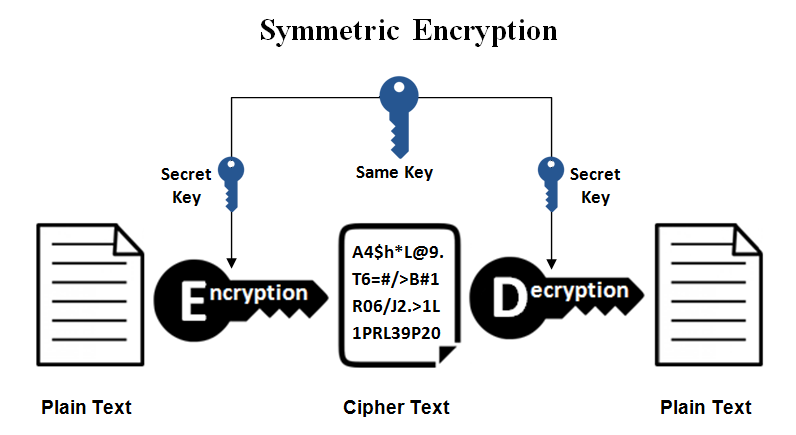
Symmetric key cryptography is a type of cryptography in which the single common key is used by both sender and receiver for the purpose of encryption and decryption of a message. This system is also called private or secret key cryptography and AES (Advanced Encryption System) is the most widely uses symmetric key cryptography.
The symmetric key system has one major drawback that the two parties must somehow exchange the key in a secure way as there is only one single key for encryption as well as decryption process.
Types: AES (Advanced Encryption Standard), DES, Triple DES, RC2, RC4, RC5, IDEA, Blowfish, Stream cipher, Block cipher, etc. are the types of symmetric key cryptography.
Asymmetric Key Cryptography
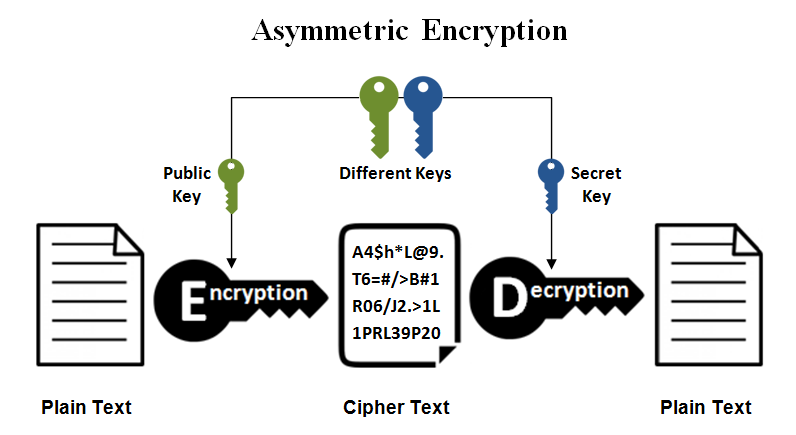
Asymmetric Key Cryptography is completely different and a more secure approach than symmetric key cryptography. In this system, every user uses two keys or a pair of keys (private key and public key) for encryption and decryption process. Private key is kept as a secret with every user and public key is distributed over the network so if anyone wants to send message to any user can use those public keys.
Either of the key can be used to encrypt the message and the one left is used for decryption purpose. Asymmetric key cryptography is also known as public key cryptography and is more secure than symmetric key. RSA is the most popular and widely used asymmetric algorithm.
Types: RSA, DSA, PKCs, Elliptic Curve techniques, etc. are the common types of asymmetric key cryptography.
Hash Function
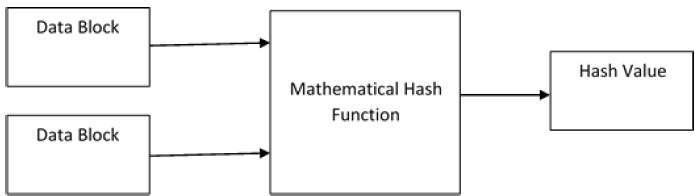
A Hash function is a cryptography algorithm that takes input of arbitrary length and gives the output in fixed length. The hash function is also considered as a mathematical equation that takes seed (numeric input) and produce the output that is called hash or message digest. This system operates in one-way manner and does not require any key. Also, it is considered as the building blocks of modern cryptography.
The hash function works in a way that it operates on two blocks of fixed length binary data and then generate a hash code. There are different rounds of hashing functions and each round takes an input of combination of most recent block and the output of the last round.
Types: Some popular hash functions are Message Digest 5 (MD5), SHA (Secure Hash Algorithm), RIPEMD, and Whirlpool. MD5 is the most commonly used hash function to encrypt and protect your passwords and private data.
Difference between Symmetric, Asymmetric and Hash Function Cryptography
- Symmetric Key uses single key to encrypt and decrypt the message while asymmetric key uses a pair of keys in which one key is used for encryption and other for decryption whereas hash function does not require any key for encryption as well as decryption.
- Symmetric key is relatively faster than asymmetric and hash function but less reliable in terms of security.
- Asymmetric key was introduced to overcome the problem of key exchange in symmetric key and hash functions were introduced to provide more security than ever.
- If the key is compromised over the network then there will loss of both sender and receiver in symmetric key, only loss of key owner in asymmetric key, and in hash function, there is no key to compromise.
- Asymmetric key has higher complexity than hash function and symmetric key has very less complexity.
Conclusion
Encryption of data is much needed in our modern time and the latest schemes may necessarily be the best fit. There are the latest algorithms and techniques being developed as hackers and eavesdroppers have made it tough to secure data to the best possible way. Cryptography is going to enhance more methods in the coming years to make personal data more secure and it’s standards more reliable.
The post Types of Cryptography appeared first on The Crazy Programmer.
No comments:
Post a Comment