Georgia Department of Public Safety Falls Victim to Ransomware, OXID E-Shop Exploit, Cybercriminals Now Using Comobolists-As-Service Model to Sell Credentials,
Latest Hacking News Podcast #336 on Latest Hacking News.
Georgia Department of Public Safety Falls Victim to Ransomware, OXID E-Shop Exploit, Cybercriminals Now Using Comobolists-As-Service Model to Sell Credentials,
Latest Hacking News Podcast #336 on Latest Hacking News.

Are you daunted by the complexity of the JavaScript ecosystem? Are you still writing ES5, but looking for an opportunity to embrace modern standards? Or, are you confused by the explosion of frameworks and build tools, and unsure what to learn first? Fear not, here are my handpicked selection of books from SitePoint Premium, intended to help you well on your way to mastering modern JavaScript.
I've placed this book at the top of my list, as it has something for almost everybody. It starts by covering the fundamentals (and thus serves well as a desk reference), then moves on to tackle more advanced topics, such as testing and functional programming.
The second edition has been updated to cover ECMAScript 6 and does a great job of introducing you to its more common features. You also get to put your newly acquired knowledge into practice at the end of each chapter, as you build out a quiz app, adding features as you move through the book. I really like this project-based approach to learning and think it is one of the better ways to advance your programming skills.
For those who just want to dip, I'd recommend reading the Modern JavaScript Development chapter. This will bring you up-to-date with many of the recent developments, such as working with modules, and the hows and the whys of transpiling your code.
This anthology picks up where Novice to Ninja left off and allows you to dive deeper into many of the newer additions to the JavaScript language. It covers much of the basic syntax (e.g. const, let, arrow functions, etc...), and offers a great way to get up to speed in a particular area.
There are also more in-depth articles on topics such as ES6 classes and ES6 modules, as well as a look at what came down the pipeline in ES2017 and ES2018. And if you're starting to get confused about what all these version numbers mean, we've got you covered. The anthology packs a chapter on JavaScript versioning and the process of deciding what gets added to the language.
npm is a package manager for JavaScript, similar to PHP's composer, or Perl's CPAN. It allows you to search an online database of packages (a.k.a. the registry) and install them on your machine. The npm registry is vast — containing over 600,000 packages — and I think it is fair to say that it has revolutionized the way JavaScript developers collaborate with each other.
This short book from our Developer Essentials series has made the list because npm is something you cannot ignore if you are serious about writing JavaScript in 2019. The guide walks you through getting npm installed and configured (which can sometimes be a tad tricky) and using it effectively in your day-to-day work. If you're going to learn just one JavaScript tool in 2019, make it npm. You'll encounter it in tutorials everywhere and it is the standard delivery mechanism for almost any modern JavaScript library out there.
Now that we've had a look at the basics, it's time to kick it up a notch with some JavaScript best practices. This anthology is full of tips and tricks to help you write modern JavaScript that is performant, maintainable, and reusable. It's hard to pick favorites from so many great titles, but there are two articles that stand out.
The Anatomy of a Modern JavaScript Application takes a good look at how to build a JavaScript application in 2019. It covers everything from application architecture to deployment and will help you to order many of the concepts and buzzwords you may have heard floating about.
Flow Control in Modern JavaScript introduces you to a variety of strategies for dealing with asynchronous JavaScript in a modern code base. It looks at one of my favorite additions to the language — async await — and dispels the myth that writing a JavaScript web app will automatically land you in callback hell.
No journey through modern JavaScript would be complete without a look at how to run it on the server. And this book gives you an excellent starting point, bringing you straight to the heart of developing web applications with Node.js.
As you follow along you'll build and iterate on a note taking app. This will form the basis for learning all about real-time applications, data storage, user authentication, deployment with Docker and much more. And even if server-side development isn't your thing, I'd still recommend reading the first couple of chapters. These will give you a good idea where Node fits in to today's JavaScript landscape.
To finish we have The Versioning Guide to Modern JavaScript, which is really a large collection of links taken from the much-missed Versioning newsletter. I've included this, as there's so much going on in the world of modern JavaScript development, that I've barely been able to scratch the surface here. I'm confident that this guide will offer you a wealth of ideas and inspiration on what to dig into next.
And that's a wrap. I hope this curated list goes some way to helping you navigate the choppy waters of modern JavaScript development.
The post Master Modern JavaScript with This Curated Reading List appeared first on SitePoint.
Once again, a huge data breach incident has impacted millions of customers. The US-based bank holding firm Capital One Financial
Capital One Data Breach Affected Millions Of US And Canada Citizens on Latest Hacking News.
Once again, a firm has breached users’ privacy by exposing customers data publicly via an unsecured cloud server. This time,
Indian Marketing Firm FormGet Publicly Exposed Users’ Documents Via Unsecured Server on Latest Hacking News.
Capital One Massive Data Breach – 106 Million Customer Records, VxWorks Critical Vulnerabilities, New Android Malware – Filecoder.C Today’s
Latest Hacking News Podcast #335 on Latest Hacking News.

Web applications are normally data-driven and oftentimes the need arises to visualize this data. That’s where charts and graphs come in. They make it easier to convey information, as well as demonstrate correlations or statistical relationships. Information presented in the form of a chart or a graph is also easier for a non-native speaker to understand.
In this tutorial, we’ll learn how to visualize data in a Vue project. For this, we’ll be using the popular D3.js library, which combines powerful visualization components and a data-driven approach to DOM manipulation.
Let’s get started.
Note: the code for this tutorial can be found on GitHub.
As you can read on the project’s home page, D3.js is a JavaScript library for manipulating documents based on data. D3 helps you bring data to life using HTML, SVG, and CSS. Its emphasis on web standards gives you the full capabilities of modern browsers without tying yourself to a proprietary framework.
Whereas most people will refer to D3.js as a data visualization library, it’s not. D3 is more of a framework comprising different parts — such as jQuery parts (which help us select and manipulate DOM elements), Lodash parts, animation parts, data analysis parts, and data visualization parts.
In this tutorial, we’ll be working with the visualization aspect of D3. The real meat of D3 when visualizing data is:
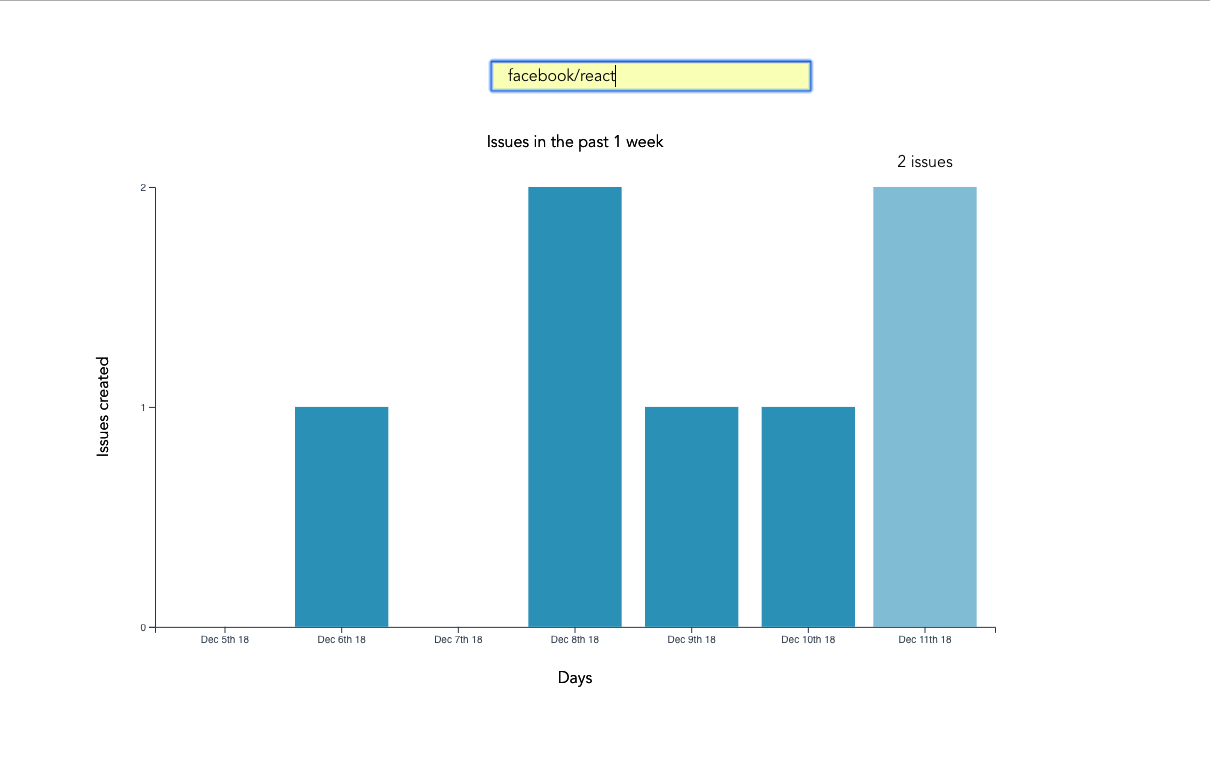
We want to create an app that lets users search for a repo on GitHub, then get a visual representation of issues opened in the past week that are still open. The end result will look like this:
This tutorial assumes you have a working knowledge of Vue. Previous knowledge of D3.js isn’t required, but if you’d like to get up to speed quickly, you might want to read our D3 by example tutorial.
You’ll also need to have Node installed on your system. You can do this by downloading the binaries for your system from the official website, or using a version manager.
Finally, we’ll be using the following packages to build our app:
I prefer creating new Vue projects using Vue CLI. (If you’re not familiar with Vue CLI, our beginner’s guide in this Vue series gives a full introduction.) Vue CLI provides a nice folder structure for placing different sections of the code, such as styles, components, and so on.
Make sure that the CLI is installed on your machine:
npm install -g @vue/cli
Then create a new project with the following command:
vue create issues-visualization
Note: while creating a new project using Vue CLI, you’ll be prompted to pick a preset. For this particular project, we’ll just stick with the default (Babel + ESLint).
Once our new Vue project has been created, we cd into the project folder and add the various node modules we’ll need:
npm install lodash d3 axios moment
Even though this is a simple app that doesn’t have many running parts, we’ll still take the components approach instead of dumping all the code inside the App.vue file. We’re going to have two components, the App component and a Chart component that we’re yet to create.
The App component will handle fetching data from GitHub, then pass this data to the Chart component as props. The actual drawing of the chart will happen inside the Chart component. Structuring things this way has the advantage that, if you want to use a library other than axios to fetch the data, it’ll be easier to swap it out. Also, if you want to swap D3 for a different charting library, that’ll be easier too.
We’ll start by building a search interface that lets users enter the name of the repo they want to see visualized.
In src/App.vue, get rid of everything inside the <template> tag and replace the content with this:
<template>
<div id="app">
<form action="#" @submit.prevent="getIssues">
<div class="form-group">
<input
type="text"
placeholder="owner/repo Name"
v-model="repository"
class="col-md-2 col-md-offset-5"
>
</div>
</form>
</div>
</template>
Here we have a form which, upon submission, prevents the browser’s default submission action, then calls a getIssues method that we’re yet to define. We’re also using a v-model directive to bind the input from the form to a repository property inside the data model of our Vue instance. Let’s declare that property repository as an empty string. We’ll also add a startDate property, which we’ll later use as the first date in our time range:
import moment from "moment";
import axios from "axios";
export default {
name: "app",
data() {
return {
issues: [],
repository: "",
startDate: null
};
},
methods: {
getIssues() {
// code goes in here
}
}
};
Now on to creating the getIssues method:
getIssues() {
this.startDate = moment()
.subtract(6, "days")
.format("YYYY-MM-DD");
axios
.get(
`https://api.github.com/search/issues?q=repo:${this.repository}+is:issue+is:open+created:>=${this.startDate}`,
{ params: { per_page: 100 } }
)
.then(response => {
const payload = this.getDateRange();
response.data.items.forEach(item => {
const key = moment(item.created_at).format("MMM Do YY");
const obj = payload.filter(o => o.day === key)[0];
obj.issues += 1;
});
this.issues = payload;
console.log(this.issues);
});
}
In the above block of code, we start by setting the startDate data property to six days ago and formatting it for use with the GitHub API.
We then use axios to make an API request to GitHub to get all issues for a particular repository that were opened in the past week and that are still open. You can refer to GitHub’s search API if you need more examples on how to come up with query string parameters.
When making the HTTP request, we set the results count to 100 per page (the max possible). There are hardly any repositories with over 100 new issues per week, so this should be fine for our purposes. By default, the per_page value is 30.
If the request completes successfully, we use a custom getDateRange method to initialize a payload variable that we will be able to pass to the Chart component. This payload is an array of objects that will like so:
[
{day: "Dec 7th 18", issues: 0},
{day: "Dec 8th 18", issues: 0},
{day: "Dec 9th 18", issues: 0},
{day: "Dec 10th 18", issues: 0},
{day: "Dec 11th 18", issues: 0},
{day: "Dec 12th 18", issues: 0},
{day: "Dec 13th 18", issues: 0}
]
After that, we iterate over the API’s response. The data we’re interested in is in an items key on a data property on the response object. From this, we take the created_at key (which is a timestamp) and format it as the day property in our objects above. From there, we then look up the corresponding date in the payload array and increment the issues count for that date by one.
Finally, we assign the payload array to our issues data property and log the response.
Next, let’s add in the getDateRange method:
methods: {
getDateRange() {
const startDate = moment().subtract(6, 'days');
const endDate = moment();
const dates = [];
while (startDate.isSameOrBefore(endDate)) {
dates.push({
day: startDate.format('MMM Do YY'),
issues: 0
});
startDate.add(1, 'days');
}
return dates;
},
getIssues() { ... }
}
Before we get to the visualization bit, let’s also log any errors we might encounter when making our request to the console (for debugging purposes):
axios
.get( ...)
.then(response => {
...
})
.catch(error => {
console.error(error);
});
We’ll add some UX for informing the user in the case that something went wrong later.
So far, we have an input field that lets the user enter the organization/repository name they wish to search issues for. Upon form submission, all issues opened in the past one week are logged to the console.
Below is an example of what was logged on the console for the facebook/react repo:
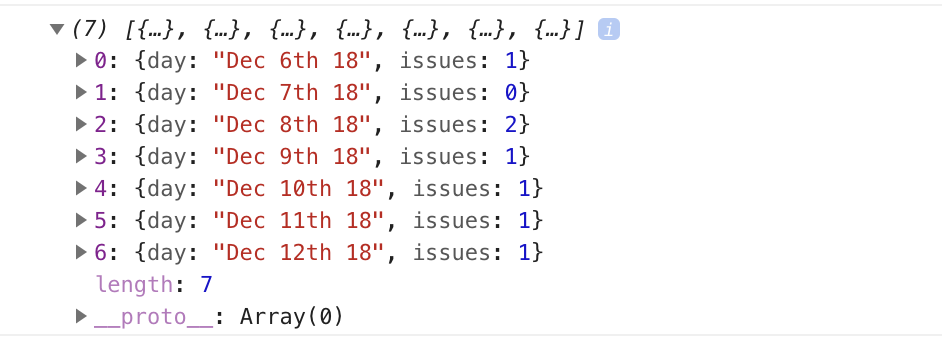
If you start up the Vue dev server using npm run serve and enter some different repos, you should see something similar. If you’re stuck for inspiration, check out GitHub’s Trending page.
Next comes the fun bit — visualizing this data.
Earlier on, we mentioned that all the drawing will be handled inside a Chart component. Let’s create the component:
touch src/components/Chart.vue
D3 works on SVG elements, and for us to draw anything with D3, we need to have an SVG element on the page. In our newly created component (src/components/Chart.vue), let’s create an SVG tag:
<template>
<div>
<svg></svg>
</div>
</template>
For this particular tutorial, we’ll visualize our data using a bar chart. I picked a bar chart because it represents a low complexity visual element while it teaches the basic application of D3.js itself. The bar chart is also a good intro to the most important D3 concepts, while still having fun!
Before proceeding, let’s update our App component to include the newly created Chart component below the form:
<template>
<div id="app">
<form action="#" @submit.prevent="getIssues">
...
</form>
<chart :issues="issues"></chart>
</div>
</template>
Let’s also register it as a component:
import Chart from './components/Chart.vue';
export default {
name: "app",
components: {
Chart
},
...
}
Notice how we’re passing the value of the issues data property to the Chart component as a prop:
<chart :issues="issues"></chart>
Let’s now update our Chart component to make use of that data:
<script>
import * as d3 from "d3";
import _ from "lodash";
export default {
props: ["issues"],
data() {
return {
chart: null
};
},
watch: {
issues(val) {
if (this.chart != null) this.chart.remove();
this.renderChart(val);
}
},
methods: {
renderChart(issues_val) {
// Chart will be drawn here
}
}
};
</script>
In the above code block, we’re importing D3 and Lodash. We then instantiate a chart data property as null. We’ll assign a value to this when we start drawing later on.
Since we want to draw the chart every time the value of issues changes, we’ve created a watcher for issues. Each time this value changes, we’ll destroy the old chart and then draw a new chart.
Drawing will happen inside the renderChart method. Let’s start fleshing that out:
renderChart(issues_val) {
const margin = 60;
const svg_width = 1000;
const svg_height = 600;
const chart_width = 1000 - 2 * margin;
const chart_height = 600 - 2 * margin;
const svg = d3
.select("svg")
.attr("width", svg_width)
.attr("height", svg_height);
}
Here, we set the height and width of the SVG element we just created. The margin attribute is what we’ll use to give our chart some padding.
D3 comes with DOM selection and manipulation capabilities. Throughout the tutorial, you’ll see lot’s of d3.select and d3.selectAll statements. The difference is that select will return the first matching element while selectAll returns all matching elements.
The post An Introduction to Data Visualization with Vue and D3.js appeared first on SitePoint.
Cloakify Factory is a tool to transforms any file type into a list of harmless and even useless looking strings.
Cloakify – A Tool to Mask Your Data in Plain Sight on Latest Hacking News.
Another day, another breach. This time, the victim turns out to be the French beauty and personal care brand –
Sephora Suffered Data Breach Targeting Customers From Southeast Asia, Australia, and New Zealand on Latest Hacking News.
“Cryptography is the standard of encrypting all the data and information by converting Plain text into cipher text for secure communication.”
Encryption is the key to secure all our data and information while we communicate with others over any transmission channel. Now, you might be thinking why this encryption matters a lot?
Data is something that is important in each field. It may include your personal identity, your financial stats, your bank account details, or anything else. No one wants that their data should be accessed by any unauthorized user. But unfortunately, there are adversaries present in the market to snatch that information in a very smart way.
There are a lot of hackers and unauthorized users who want access to public data, so they can mislead that information for their benefits. For this purpose, Cryptography standards were introduced to protect our data from such threats.
In this topic, we will cover what actually Cryptography is, how does it work, and what are its algorithm types. But before moving on, let us discuss some related terms:
Now let’s start with the basics.
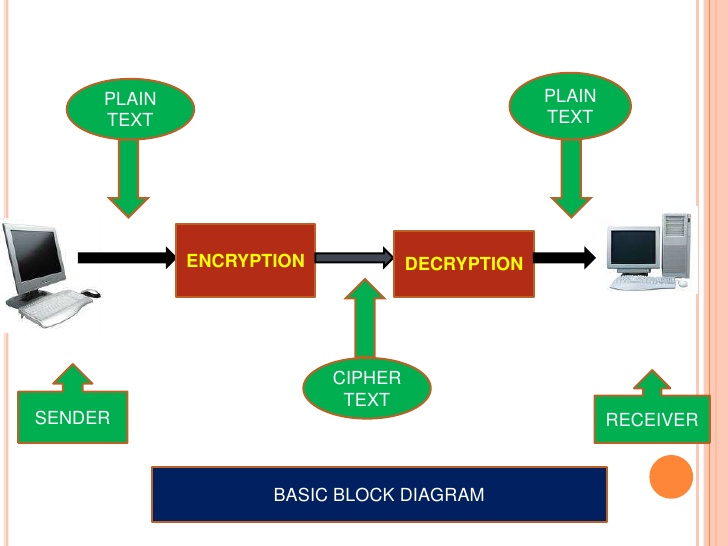
Now, suppose there is one sender A who wants to send a message to receiver B who is in the other part of the world. The sender obviously wants this message to be private and no one should access it except the receiver. Here, the only motive is to secure the communication.
The sender A will first convert its plain text message into cipher text (unreadable format) using a key. The message is then encrypted and now A sends this message to receiver B over any transmission media.
B now receives the message and will require a decryption key to decode the message into a readable format. He then uses the key and decrypts the message to find the original plain text.
This is how cryptography works and data is encrypted to secure them from external threats and attacks. There are several different types of cryptography algorithms with each different working methodologies to encrypt the data in the best possible way.
Cryptography is further classified into three different categories:
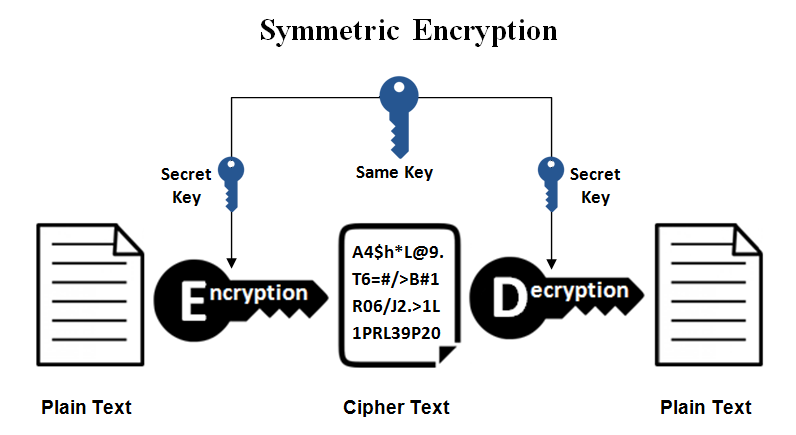
Symmetric key cryptography is a type of cryptography in which the single common key is used by both sender and receiver for the purpose of encryption and decryption of a message. This system is also called private or secret key cryptography and AES (Advanced Encryption System) is the most widely uses symmetric key cryptography.
The symmetric key system has one major drawback that the two parties must somehow exchange the key in a secure way as there is only one single key for encryption as well as decryption process.
Types: AES (Advanced Encryption Standard), DES, Triple DES, RC2, RC4, RC5, IDEA, Blowfish, Stream cipher, Block cipher, etc. are the types of symmetric key cryptography.
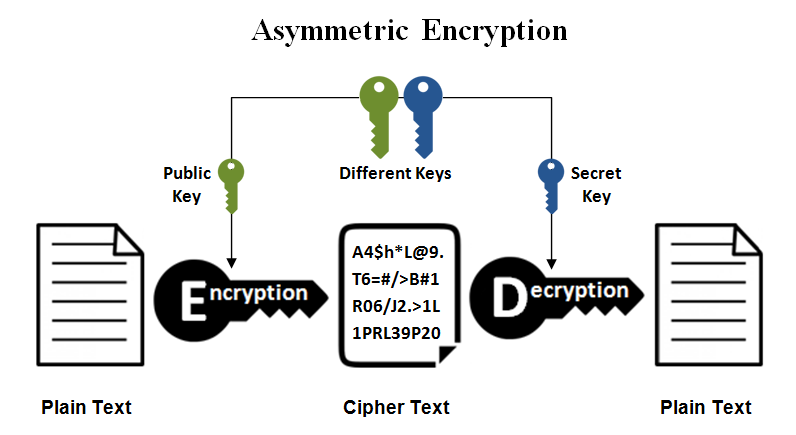
Asymmetric Key Cryptography is completely different and a more secure approach than symmetric key cryptography. In this system, every user uses two keys or a pair of keys (private key and public key) for encryption and decryption process. Private key is kept as a secret with every user and public key is distributed over the network so if anyone wants to send message to any user can use those public keys.
Either of the key can be used to encrypt the message and the one left is used for decryption purpose. Asymmetric key cryptography is also known as public key cryptography and is more secure than symmetric key. RSA is the most popular and widely used asymmetric algorithm.
Types: RSA, DSA, PKCs, Elliptic Curve techniques, etc. are the common types of asymmetric key cryptography.
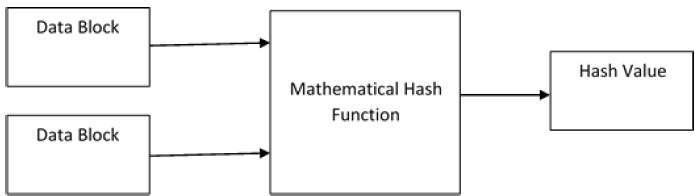
A Hash function is a cryptography algorithm that takes input of arbitrary length and gives the output in fixed length. The hash function is also considered as a mathematical equation that takes seed (numeric input) and produce the output that is called hash or message digest. This system operates in one-way manner and does not require any key. Also, it is considered as the building blocks of modern cryptography.
The hash function works in a way that it operates on two blocks of fixed length binary data and then generate a hash code. There are different rounds of hashing functions and each round takes an input of combination of most recent block and the output of the last round.
Types: Some popular hash functions are Message Digest 5 (MD5), SHA (Secure Hash Algorithm), RIPEMD, and Whirlpool. MD5 is the most commonly used hash function to encrypt and protect your passwords and private data.
Conclusion
Encryption of data is much needed in our modern time and the latest schemes may necessarily be the best fit. There are the latest algorithms and techniques being developed as hackers and eavesdroppers have made it tough to secure data to the best possible way. Cryptography is going to enhance more methods in the coming years to make personal data more secure and it’s standards more reliable.
The post Types of Cryptography appeared first on The Crazy Programmer.
Interview with Asaf Ashkenazi, Chief Strategy Officer of Verimatrix – Mobile Security Today’s Agenda is as follows Interview with
Latest Hacking News Podcast #334 on Latest Hacking News.
The innovativeness of hackers seems to have no end. Once again, they have worked out a means to evade security
Phishing Campaign Exploits WeTransfer Alerts To Bypass Email Gateways on Latest Hacking News.

This article was created in partnership with Duda. Thank you for supporting the partners who make SitePoint possible.
Kentico’s most recent State of the Headless CMS report claims that the concept of the headless content management system is “becoming the industry standard for future-proofing and streamlining content creation.” In fact, the report estimates that by this summer, headless CMS use will have doubled.
But what does that even mean?
If you’re currently using a traditional CMS such as WordPress, Drupal or Joomla for your web development needs, chances are you may have never heard of a headless CMS. But what you might know is that you want to build a one-of-a-kind website for your growing agency that can scale with ease, and that marketing your brand across multiple channels is a must if you want to beat the competition.
In this article, we’re going to share with you what the headless CMS trend is all about and how using this API-powered approach to design and deploy your company’s website can help you get ahead, no matter how competitive your industry is.
So, let’s get started.
To better understand what a headless CMS is, let’s compare a traditional CMS (or “monolithic”, as developer Bret Cameron likes to call it), a decoupled CMS, and a headless CMS.
Traditional CMS platforms like WordPress link the front end of your website, called the head, to the back end of your site, where all your content files and databases are stored. The head of the CMS is strictly responsible for presenting your website to site visitors when they click on your site. The back end, on the other hand, not only stores content, but is where website design and customization applications are stored, where content is created, and where management of site functionality occurs.
Paired together, as they traditionally are, the back-end portion of the website relies on the head of the CMS to display the stored content on devices to users.
With a decoupled CMS architecture, the head portion and the back end of the site are split into two separate systems. One system is responsible for content creation and storage, and the other is responsible for presenting the data to users on an interface, such as a website, mobile app, smartwatch, etc.
When content is created on your website using a headless CMS, a RESTful API helps connect the back end to the head, so that the content can be delivered to users on any device or channel with ease.
A RESTful API is a type of application interface using HTTP requests to GET, POST, PUT, and DELETE data that’s requested by users. It allows for multiple data formats such as JSON, HTML, XML, and plain text. It’s ultimately what links the client and server in a decoupled CMS, allowing your site to infinitely scale and deliver content to anyone on any device.
A truly headless CMS eliminates the head portion altogether, leaving just the back end. In other words, there’s no dedicated system for front-end presentation. And while you might initially wonder if this type of structure might be to your disadvantage, it’s actually the best way to display content to your site visitors on all devices and interfaces, putting your agency in the best possible position to scale.
Here’s a simple breakdown of how it works:
The way your content will display on the different channels and devices will depend on the frameworks and tools your front-end developers use to act as the “head” portion of your headless CMS.
So it’s more freedom to integrate with more front ends, more scalably and without the risk of breaking anything. How, exactly? Let’s dive a little deeper.
APIs work with a headless CMS to do the following:
Lastly, a headless CMS protects you, your company and your website’s content from future technological advances. After all, platforms and technology are always evolving, making it challenging to keep up.
For example, think about all the problems that those of us who didn’t build responsive websites had when mobile-friendliness became a necessity. People all over, regardless of how well-established and successful they were at the time, had to change everything to ensure a seamless mobile experience.

And there’s no end in sight to the trends — from artificial intelligence to augmented reality to voice assistants — that have the power to change the way you build and deliver digital content experiences. Traditional CMS platforms were designed with website publishing in mind. They were not built with social media product listings, smartwatch apps or talking speakers in mind.
So when the build is decoupled from the delivery, you’re in the best possible position to experiment with new channels and formats on an agile basis. And this is a key aspect to any agency’s value proposition.
If you take advantage of the headless CMS approach and use APIs to deliver your content to where it needs to surface, it won’t matter what changes. That’s because as long as an API-fed front end can be built, your client’s content can be configured to render properly.
Though it might seem as though a headless CMS is the answer to all your website problems, be aware that there are some downsides preventing traditional CMS users from making the switch:
While there is no CMS solution that satisfies all needs, it’s worth noting that the headless CMS approach can be beneficial when used in a hybrid situation.
In fact, if you use a solution such as Duda, a leading web design platform for companies providing web design services to others, and take advantage of APIs to deliver content and handle your site’s structure and layouts on multiple channels, you can get the best of both worlds.
The post The Strategic Advantages of Headless Web Design appeared first on SitePoint.
ESET researchers discover a new Android ransomware family that attempts to spread to victims’ contacts and deploys some unusual tricks
The post Android ransomware is back appeared first on WeLiveSecurity
The fraudulent campaign is hosted by a domain that is home to yet more bogus offers pretending to come from other well-known brands
The post Scam impersonates WhatsApp, offers ‘free internet’ appeared first on WeLiveSecurity
For all Microsoft Office 365 users who regularly use its webmail, yet expect to remain veiled, here is an irony.
Microsoft Office 365 Webmail Shows Senders’ IP Addresses In Email Headers on Latest Hacking News.
Another Magento card skimming attack is active in the wild. In this case, the attackers target the websites with codes
Fake Google Domains Used To Target Magento Websites For Credit Card Skimming on Latest Hacking News.
Researchers from Tenable have discovered numerous security vulnerabilities in Comodo Antivirus. For now, the users of this antivirus need to
Multiple Vulnerabilities Discovered In Comodo Antivirus – Patch Pending! on Latest Hacking News.
Another huge data leak incident comes up this time affecting Brazilian customers. A Brazilian financial service exposed massive customer records
Brazilian Financial Service Exposed 250GB Of Local Banks’ Customers Data Via Unsecured Server on Latest Hacking News.
Most smartphone users love to watch innocent videos of babies, pets, and other cute moments. Interestingly, the hackers also like
Android Media Framework Flaw Could Get Phones Hacked By Playing Malicious Video on Latest Hacking News.
After Facebook and Google, another firm has confessed incidental storage of users’ passwords in plain text. This time, it is
Financial Service Robinhood Stored Customers Passwords In Plain Text on Latest Hacking News.
Selling a physical video game is easy. You can auction it on Craigslist or trade it to a friend for
How to Safely Sell your Steam Account on Latest Hacking News.
If you have a Deliveroo account, then keep an eye on it vigilantly. Sooner or later, you might receive a
Customers Wrongly Billed After Deliveroo Accounts Got Hacked on Latest Hacking News.

We're working hard to keep you on the cutting edge of your field with SitePoint Premium. We've got plenty of new books to check out in the library — let us introduce you to them.
For developers with a web background, frameworks such React Native allow you to create mobile apps with languages you’re already familiar with: HTML, XML, CSS, and JavaScript. This guide will help get you up and running with React Native.
➤ Read Get Started with React Native.
An introductory course to building your first universal React app. Starting with an introduction to React, and then getting familiar with the invaluable React toolkit - Create React App, we'll then walk you through the steps of creating a universal React blog app from scratch.
➤ Read Build Your Own React Universal Blog App.
We're releasing new content on SitePoint Premium almost every day, so we'll be back next week with the latest updates. And don't forget: if you haven't checked out our offering yet, take our library for a spin.
The post SitePoint Premium New Releases: React + React Native appeared first on SitePoint.
Interview with Karl Sigler, Threat Intelligence Manager at Trustwave SpiderLabs – Uniguest Vulneravbility Today’s Agenda is as follows Interview
Latest Hacking News Podcast #333 on Latest Hacking News.
A critical vulnerability that was thought to affect VLC media player was later downgraded to medium severity, and the player's maker slammed the bug disclosure process
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
The power utility appears to be well on track to a swift recovery following an attack that ultimately left some people without electricity
The post South African power company battles ransomware attack appeared first on WeLiveSecurity
ProFTPD Server Vulnerability, GlobalProtect SSL VPN Critical Vulnerability, Lancaster University Data Breach Today’s Agenda is as follows ProFTPD Server
Latest Hacking News Podcast #332 on Latest Hacking News.
Researchers have spotted active exploitation of WordPress plugin vulnerabilities. Reportedly, the known vulnerabilities in various plugins are facilitating the threat
WordPress Plugin Exploitation on The Rise For Malvertising Based Exploits on Latest Hacking News.
If you are one of those parents who think their kids are safe using Facebook Messenger Kids app, then here
Facebook Messenger Kids App Vulnerability Exposed Kids To Strangers on Latest Hacking News.
This week, Apple has rolled out security updates for different Apple products. These include numerous security fixes in watchOS and
Apple Patched Walkie-Talkie Bug With iOS 12.4, As Well As Other Fixes on Latest Hacking News.

In this article, you’ll learn how to build a RESTful API Server in Node.js using Feathers.
An API server, also known as an Application Server, is a program that provides data to front-end applications. It also handles business logic in the back end and provides restricted access to an organization's database. It doesn't just prevent unauthorized persons from accessing the data; it can also restrict logged-in users from accessing or altering data if they don't have permission to do so.
Every application you build will need to provide a service to its end users. For that, your application will need data to process. You can use remote APIs to create a new service. For most applications, though, you’ll need to manage your own data store. A popular option is to use online data storage services such as Firebase. This way, you don't have to deal with the nitty gritty details of running a distributed database server. However, your project needs may require the use of a full-fledged, in-house database management system such as MongoDB or Oracle. For your front-end application to access the data stored in the database, you’ll need a server application that sits between the database and the front-end application.
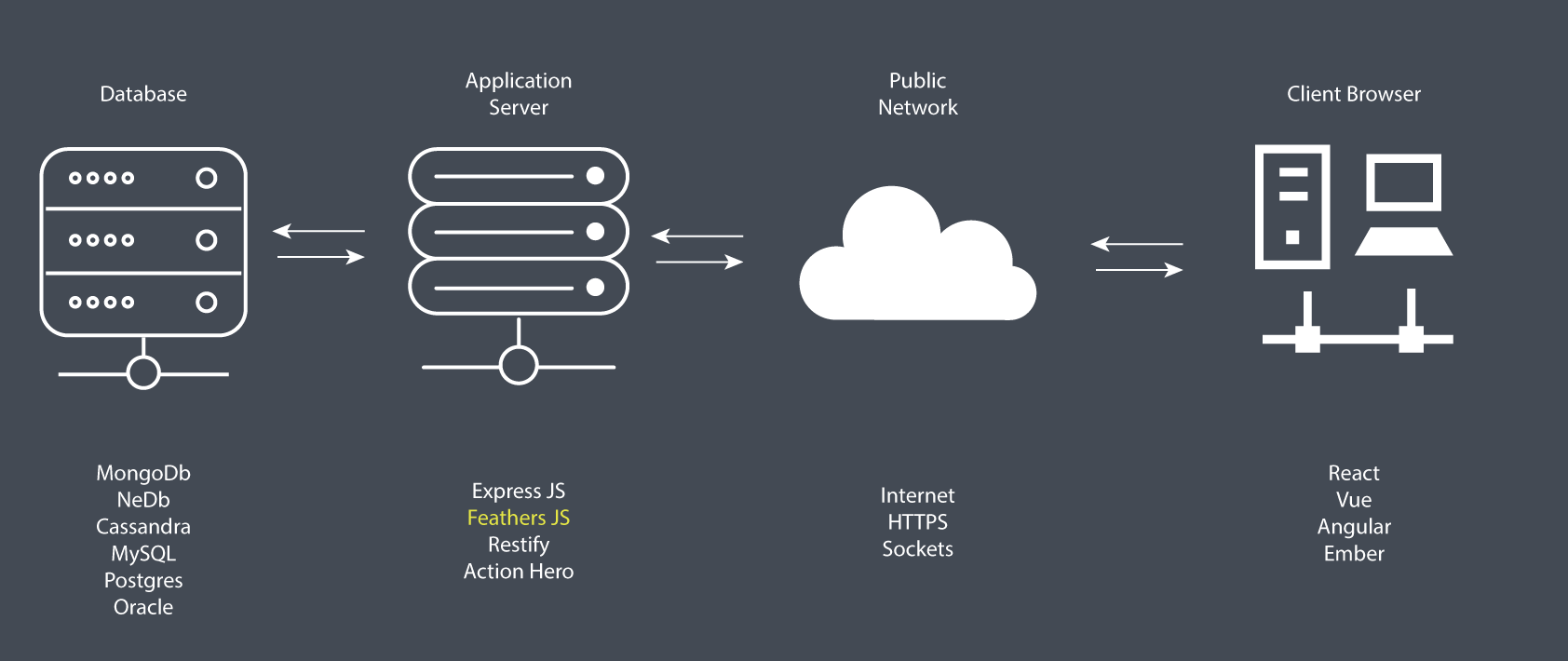
As illustrated in the diagram above, the work of an application server is to access data from a database using SQL or NoSQL commands and convert into a format that front-end applications (client browser) can understand — such as JSON. In addition, the application server can use various security protocols — such as HTTPS encryption and token authorization — to ensure that communication between the database and the client application is safe and secure. One main advantage of using such an architecture is that you can deploy applications that target different platforms — desktop, mobile, web, and so on — using the same application server. It’s also very easy to scale your application horizontally in order to serve more users efficiently with fast response times.
We’re going to build a simple API server and demonstrate the various features that Feathers provides.
Before you begin following this tutorial, you’ll need to have a good foundation in the following topics:
Feathers is built on top of Express, a minimalist web framework for Node.js. If you’ve completed the tutorials demonstrated in the links, you’ll realize that it's quite tiring building RESTful APIs using just Express. With Feathers, most of the repetitive work is already done for you. You only need to focus on configuring and customizing code. Let's dive into the code and learn how this web framework works.
To get started with Feathers, you’ll need to install its command line application globally:
npm install -g @feathersjs/cli
Next, create a new API project using the commands below:
mkdir contacts-api
cd contacts-api
feathers generate app
Below are the options I chose. Feel free to choose any testing framework. Unfortunately, testing is beyond the focus of this article, so it won't be covered here. Personally, I like simplicity, and that’s why I went with Jest.
Once the installation is complete, you can open you favorite code editor to look at the project files.
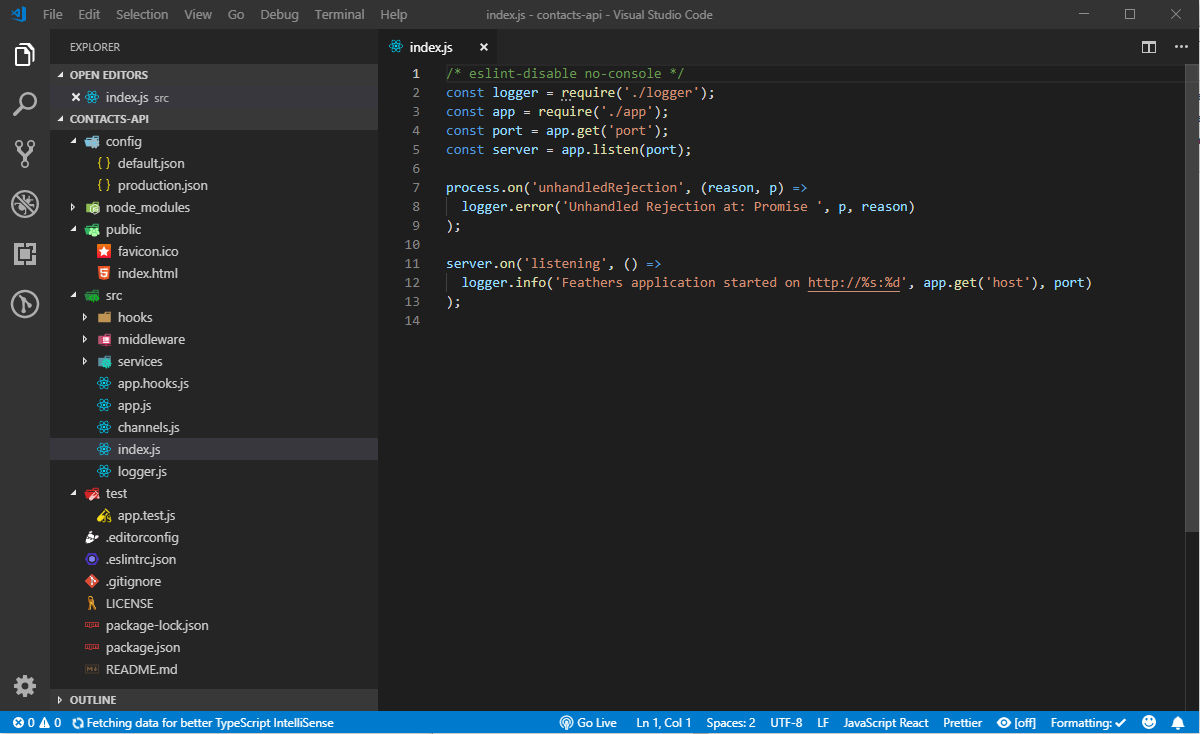
If you’ve completed the Express tutorials I listed in the prerequisites section, you shouldn't be intimidated by the generated code. Here's a brief summary that describes the folders and files.
Don't be too concerned with what each file does right now. You’ll come to understand how they work in the course in this tutorial. For now, let's confirm that the tests are working.
To ensure our project is compliant with the defined ESLint rules, just run the command npm test. If you’re on a Unix or Linux platform, this should run fine. If you’re on Windows, there are few things you need to adjust for the tests to run successfully.
First, go to package.json and look at the scripts section. Change the test line to this:
"scripts": {
"test": "npm run eslint && SET NODE_ENV= npm run jest",
},
Next, if you’ve installed Prettier in Visual Studio Code, you'll need to change the single quote setting to true in the Workspace settings tab:
{
"prettier.singleQuote": true
}
Finally, make sure that, when you create or edit any file, the line ending is LF. If you’re using Visual Studio Code or a similar editor, you can check the current line ending style at the status bar. If it says CRLF, change to LF. Making those changes will help you pass the lint tests. Unfortunately, to make the tests pass will require a bit more work, which won't be covered here.
Let's look at how we can generate a CRUD RESTful interface.
Building a Restful CRUD API interface in Express requires a bit of work. In Feathers, all you have to do is execute a single command, answer a few questions and have the code generated for you:
$ feathers generate service
? What kind of service is it? NeDB
? What is the name of the service? contacts
? Which path should the service be registered on? /contacts
? What is the database connection string? nedb://../data
force config\default.json
create src\services\contacts\contacts.service.js
force src\services\index.js
create src\models\contacts.model.js
create src\services\contacts\contacts.hooks.js
create test\services\contacts.test.js
We’ll be using NeDB database for this tutorial. Feathers does support both SQL databases such as MySQL and NoSQL databases such as MongoDB. However, installing a database system — whether on your machine or on a cloud server — requires a certain amount of time configuring it. NeDB, on the other hand, is an in-memory database that’s 100% JavaScript and supports a subset of MongoDB API. There’s no configuration needed; you just install it. It's a great database for prototyping and testing new applications. This is what we’ll use in this tutorial.
Let's briefly look at some of the files that have been generated using this command:
services/contacts/contact.service.js. This is a Feathers service that provides the CRUD API endpoints for /contacts. Pretty small, isn't it? This is because Feathers does the heavy lifting for us. It saves us from writing boilerplate CRUD code.
services/contacts/contact.hooks.js. This is where we customize how the CRUD logic behaves. We have the before section, where we can check or change data before Feathers reads or writes to the database. We also have an after section, where we can check or change the results from the database before it’s sent to the client application. We can do things like restricting access, data validation, performing join operations and calculating values for additional fields or columns.
models/contacts.model.js. This where we define a model and attach it to a database table. This is also where we define a schema which can be used to validate fields when a new record is inserted or updated. Unfortunately, NeDB doesn’t support schemas. However, I've provided an example of a model that’s connected to MongoDB, which supports the schema feature via the mongoose adapter:
"use strict";
const mongoose = require("mongoose");
const Schema = mongoose.Schema;
require("mongoose-type-email");
const contactsSchema = new Schema({
name: {
first: { type: String, required: [true, "First Name is required"] },
last: { type: String, required: false }
},
email: {
type: mongoose.SchemaTypes.Email,
required: [true, "Email is required"]
},
phone: {
type: String,
required: [true, "Phone is required"],
validate: {
validator: function(v) {
return /^\+(?:[0-9] ?){6,14}[0-9]$/.test(v);
},
message: "{VALUE} is not a valid international phone number!"
}
},
createdAt: { type: Date, default: Date.now },
updatedAt: { type: Date, default: Date.now }
});
const contactsModel = mongoose.model("contacts", contactsSchema);
module.exports = contactsModel;
Despite the limitations of using NeDB, it’s still a great database for prototyping. Most NoSQL databases will allow you to submit data using any structure without having to define a schema first. It’s wiser to implement a schema once the project requirements have been realized. With a schema in place, Feathers will perform field validation for you using the rules you’ve defined. You'll need a production-ready database such as MongoDB to be able to define a schema. Do note the configuration for the development database is defined at config/default.json:
"nedb": "../data"
This is where database credentials are provided. We also have another config file called config/production.json. This is the production database configuration that’s used when you deploy your Feathers app. It's important to use a separate database during development. Otherwise, you run the risk of deleting or corrupting business operational data on the production database.
Now that we have our CRUD service for contacts set up, it's time to take it for a spin. You can start the Feather server using the command npm start. Do note that this server doesn’t support hot reloading. So you'll need to restart it every time you make a change to the code. In order to interact with our Feathers app, we’ll need an API browser tool such as Postman or Insomnia. I'll be using Insomnia in this tutorial, but you can follow along easily with Postman or any other tool.
Create a new GET request (press Ctrl + N) and give it the title “List Contacts”. In the URL section, enter http://localhost:3030/contacts. When you hit the Send button, you should have the following view:
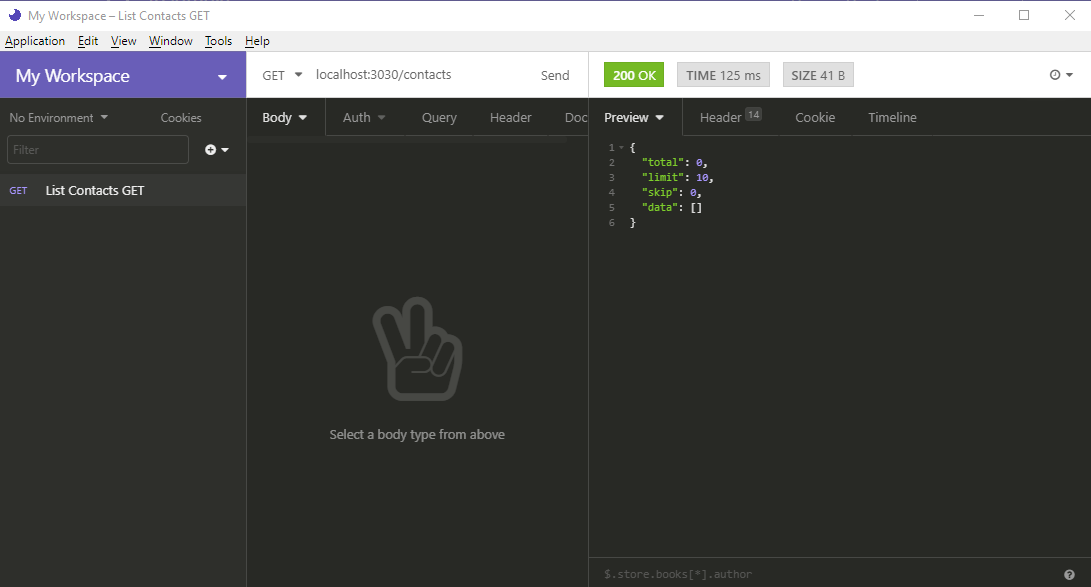
Nothing! Our database is currently empty, so we need to create some new contacts. Create a new request called Create Contact. Fill in the rest of the fields as shown below:
In case you forgot to change the METHOD to POST in the above form, you can do so later. Change the method to POST and change the Body tab to JSON. Copy the following data in the JSON tab:
{
"name": {
"first": "Jack",
"last": "Bauer"
},
"email": "jack@ctu.mail",
"phone": "+1234567"
}
When you hit the Send button, you should get the following response. Notice that an _id has been generated for your new contact.
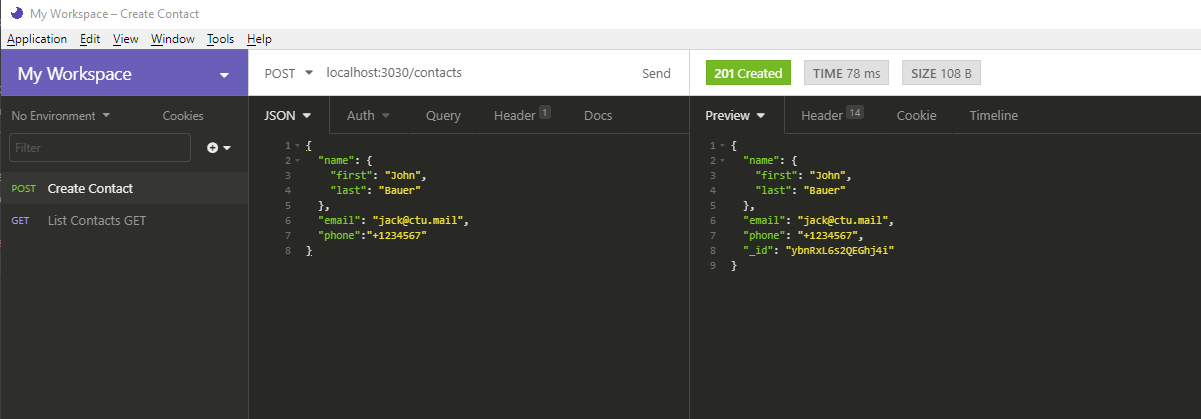
Go back to List Contacts and hit the Send button again. You should get the following result:
{
"total": 1,
"limit": 10,
"skip": 0,
"data": [
{
"name": {
"first": "Jack",
"last": "Bauer"
},
"email": "jack@ctu.mail",
"phone": "+1234567",
"_id": "ybnRxL6s2QEGhj4i"
}
]
}
Go back to Create Contact and post a couple of new records:
{
"name": {
"first": "Chloe",
"last": "O'Brian"
},
"email": "chloe@ctu.mail",
"phone": "+1987654"
}
{
"name": {
"first": "Renee",
"last": "Walker"
},
"email": "renee@fbi.mail",
"phone": "+150505050"
}
Let's now perform an update. For this, we won't use the UPDATE HTTP method. This method will completely overwrite a record. What we want to do is just overwrite a single field, not the the whole record. For that, we’ll use PATCH. Create a new request, Update Contact as illustrated below:
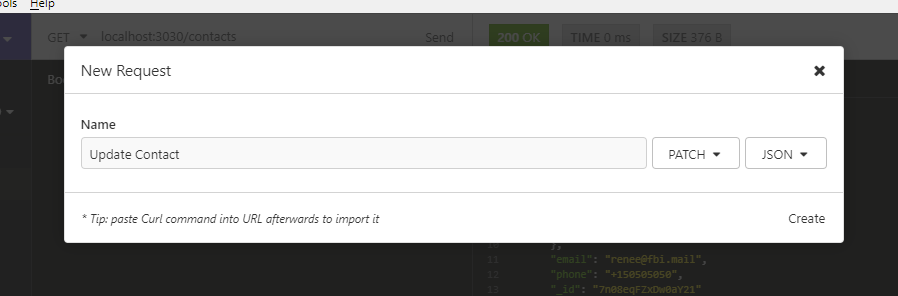
In the URL field, put http://localhost:3030/contacts/{_id}. Replace {_id} with the ID of the first record. Place the following data into the JSON tab:
{
"email": "jack.bauer@gmail.com"
}
Hit the Send button. You should get the following result:
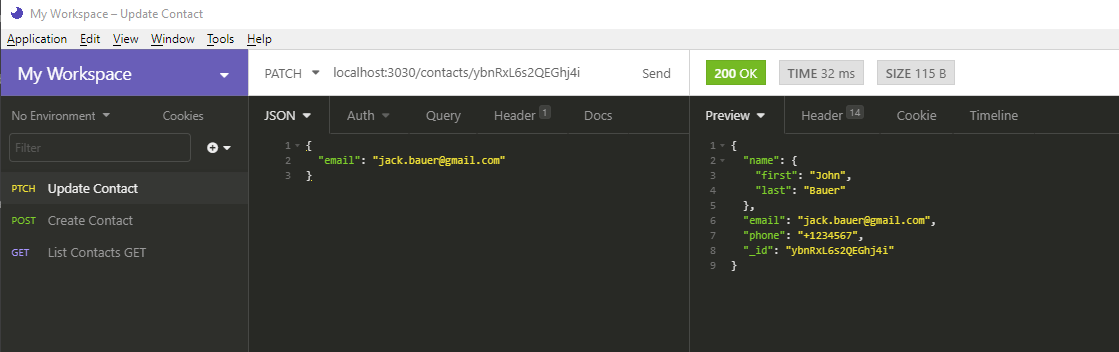
Notice how the the rest of the fields remain intact. Next, we’re going to delete a record. This one is easy. Just create a new DELETE request and name it Delete Contact. In the URL field, use the format http://localhost:3030/contacts/{_id}. Just like before, replace {_id} with the ID of the record you want to delete. Hitting Send will delete that record for you. You can confirm by running the List Contact request again.
We've just verified that all CRUD operations are running okay. In the next section, we’ll learn how to set up authentication.
The post A Beginner’s Guide to Feathers.js appeared first on SitePoint.
The attack, unleashed by a 400,000-strong Mirai-style botnet, may be the largest of its kind on record
The post Streaming service endures 13‑day DDoS raid appeared first on WeLiveSecurity

In this article, we're going to dive into the offerings of the most prominent players in the hosting industry, and wade through their plans, infrastructure, and reputation among users, to give you recommendations for the best hosting provider for your needs.
We divided hosting vendors into three categories:
This category covers the widest part of the hosting market — from the entry-level shared plans to prosumer and premium offerings with dedicated resources and different levels of support.
A2 Hosting was founded in 2003 in Michigan, USA. They offer entry-level shared hosting packages, managed VPS and dedicated servers and seller hosting.
Their shared packages are standard cPanel packages, with SSD-based storage and a promise of reserved CPU and RAM resources — even with the smallest of plans.
Their LITE plan begins at $2.96 per month, which allows for one website. Their SWIFT plan has unlimited websites, starting with $3.70 per month. And their TURBO plan starts at $7.03 per month. These prices are — as the A2 website claims — a 63% discount.
They offer free migration, 24/7 support, DDOS protection and “99.99% uptime commitment”, which is always nice to know.

The flagship plan that distinguishes A2 is the TURBO package, which uses LiteSpeed servers — an excellent replacement for Apache, which also brings with it a performance edge.
Underlying LiteSpeed allows A2 to offer QUIC as an experimental feature on the TURBO plan.
A2 offers four possible server locations — two data centers in the US, one in Singapore and one in Amsterdam, so they'll have you covered in most parts of the world.
For more details check out their website.
SiteGround is a “holding of companies registered in the USA, UK, Bulgaria, and Spain that manages four offices and several datacenter locations around the world”. Established in 2004, it has become somewhat of an institution in the hosting world that’s been recommended by WordPress itself.
SiteGround’s hosting range is similar to A2’s, and starts from the entry-level shared packages all the way to cloud products and dedicated servers. The company also offers bespoke enterprise solutions.
SiteGround offers packages similar to A2’s plans — although its GrowBig and GoGeek plans cost a bit more than a comparable A2 plans.
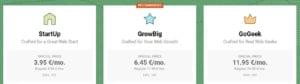
However, SiteGround does offer free daily backups across all the plans, free migration on GrowBig and GoGeek — as well as staging installation, which is handy for more professional setups.
Use of resources for each plan is limited in terms of server processes, simultaneous connections, CPU seconds, RAM, cronjob intervals — and they are specific and transparent about it, which is a plus.
One caveat to note is that the prices mentioned above are promotional prices for the first year of signup, and renews at a higher price after that.
SiteGround's server stack consists of NGINX as a caching solution in front of Apache — which means that even SiteGround's StartUp plan is not constrained by Apache limitations.
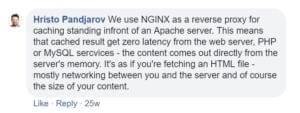
We use NGINX as a reverse proxy for caching, standing in front of an Apache server. This means that cached results get zero latency from the web server, PHP or MySQL services. The content comes our directly from the server's memory. It's as if you're fetching an HTML file — mostly networking between you and the server, and of course the size of your content. — Hristo Pandjarov
They offer server locations in the UK, USA, continental Europe and Asia (Singapore).
SiteGround has also recently announced support for the QUIC next-generation protocol, which will increase site loading speed even if there’s poor internet connectivity at your location.
For more details check out their website.
Bluehost was founded by Matt Heaton in 2003, and enjoyed immense popularity until 2011, when it was acquired by EIG. Since the acquisition, it has remained one of the most prominent players in the hosting scene, but it has been plagued by mixed reviews regarding its user experience.
Bluehost offers a similar range of products to the others — from entry-level shared plans to VPS, dedicated servers, ecommerce and WordPress packages. But it currently offers the lowest prices of the three mentioned in this category (for a 36-month term; prices go up as you'd expect for shorter terms).
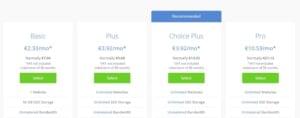
All but the smallest of these plans include unlimited resources (SSD Storage). However, do note that in the fine print of their Terms of Service notes:
While rare, we occasionally constrain accounts utilizing more resources than should be the case in the normal operation of a personal or small business website.
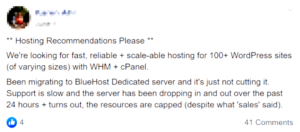
Hosting Recommendations Please
We're looking for fast, reliable + scalable hosting for 100+ WordPress sites (of varying sizes) with WHM + cPanel.
Been migrating to Bluehost Dedicated server and it's just not cutting it. Support is slow and the server has been dropping in and out over the past 24 hours + turns out the resources are capped (despit what “sales” said).
“No specified limits to resources” in this case may translate to “no guaranteed resources”. Even before the EIG acquisition, Bluehost had introduced a CPU-throttling strategy — so be warned. You can read more about Bluehost's restrictions regarding resources here.
On its bigger plans, Bluehost offers SSH access, cron jobs, daily backups etc. But it’s mostly oriented toward the entry-level market.
Bluehost has some perks and a custom management web UI for WordPress customers.
As for the server locations — Bluehost doesn’t offer straightforward information, but besides Utah, USA, they seem to have data centers in China and India (Mumbai).
The post The Best Web Hosting Providers For Your Needs appeared first on SitePoint.