Web applications are both a valuable resource for organizations and one of the biggest threats to their cyber security. Web apps are designed to be exposed to users via the Internet, allowing them the convenience of interacting with their accounts via their browser. However, this same easy access also makes these web apps a prime target for attackers trying to breach the organization’s defenses.
When attempting to secure a web application (or any software), it is extremely useful to know what to look for. The wide variety of potential attacks against web applications makes it easy to overlook a certain vulnerability class when performing a search for vulnerabilities.
An extremely valuable resource for this is the OWASP Top 10 list, which lists the ten most common vulnerabilities based off of the analysis of the Open Web Application Security Project (OWASP). This list is updated every few years and is based upon a combination of data and the opinions of experts in the field.
However, there are also other useful sources of data regarding the vulnerability threat landscape in the real world. Penetration testers see the vulnerabilities that exist in the wild, so they’re worth listening to when they provide information regarding the threats that they are seeing most often.
Vulnerabilities in the Real World
When trying to figure out what the most common and important vulnerabilities are present in real-world software, it’s useful to go to the source. Penetration testers are the cybersecurity experts commonly tasked with testing an organization’s cyber defenses and reporting on the vulnerabilities that they find.
In the past, it has been difficult to acquire large-scale cyber vulnerability data since the results of assessments are typically kept confidential and few companies have the scale necessary to discover general trends. However, the rise of crowd-sourced vulnerability detection organizations, like HackerOne, have changed this.
Unlike traditional penetration testing companies, which have a team of pen testers on staff to perform assessments, HackerOne acts as a middleman between companies and groups of freelance testers. Access to the test environment is provided through HackerOne, allowing them to collect statistical data about the assessments performed and the types of vulnerabilities discovered.
According to the company, currently the most common type of vulnerability on web applications is cross-site scripting (XSS). This may come as a surprise since most attacks that make the headlines don’t involve XSS. This is because the headlines are usually focused on data breaches, and XSS vulnerabilities rarely lead to large-scale data breaches. However, $8 million of the $55 million paid out in bug bounties on HackerOne went to discoveries of XSS vulnerabilities in companies’ web applications. This underscores how common these vulnerabilities are since they carry lower rewards per detection that other “more damaging” vulnerabilities.
What is Cross-Site Scripting (XSS)
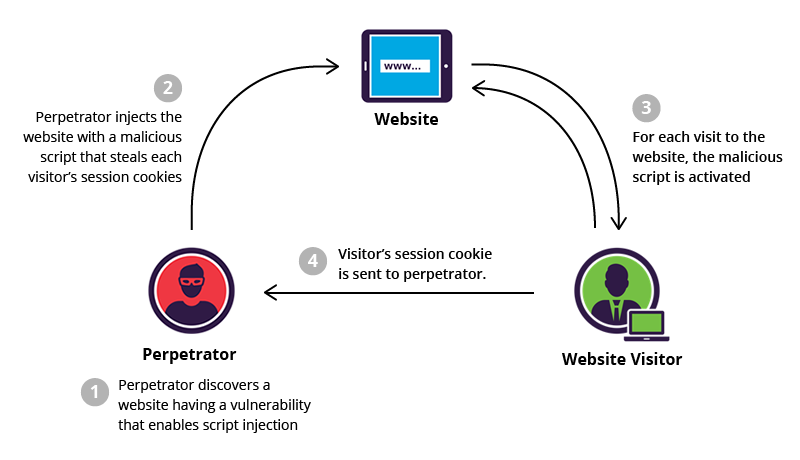
The Internet use many different methods to control access to sensitive of protected resources. One of these mechanisms is the same-origin policy. According to the same-origin policy, if content from a site is granted access to a protected resource, other content coming from the same place (same URI, domain, and port number) can take advantage of the same access without being granted specific permission. Cross-site scripting (XSS) attacks take advantage of this policy to gain unauthorized access to protected resources.
There are several different types of cross-site scripting, but they all involve injection of malicious code into a trusted website. This code injection is made possible by vulnerabilities in the web application itself, the web server where the code is hosted, or any plug-ins that the application uses.
When a user browses to an affected website, they receive both the legitimate code of the site as well as a malicious script injected by the attacker. Since all of this code comes from “the same place”, the single-origin policy means that the malicious code has access to the same data and resources as the legitimate website code. This gives the attacker access to any protected, sensitive data used by the legitimate page, which may be used to steal personal data (like credit card information) or data (like session cookies) that can allow the attacker to access the user’s account directly.
Protecting Your Web Apps
Cross-site scripting (XSS) and other web application vulnerabilities can be a severe threat to an organization’s network and data security. Web applications are designed to be publicly exposed on the Internet and act as a gatekeeper for protected data or functionality. If they are compromised by a hacker, they can act as a foothold for the attacker to expand their access onto the protected network and/or as a means of collecting sensitive user data.
Protecting against XSS vulnerabilities and other web application vulnerabilities listed on the OWASP Top Ten is one of the main features of a web application firewall (WAF). The attacks used to exploit these vulnerabilities are well-known and can be detected and prevented using a WAF.
However, the threat surface of a web application is not limited to the attacks included on OWASP’s Top Ten list. These other attack vectors are where the best WAFs stand out from the rest of the pack. Signature-based detection helps with known attacks, but a WAF also needs anomaly-based detection to identify and protect against unknown threats. Protecting a web application requires the ability to stop any attack, so choosing a strong WAF is a crucial aspect of any organization’s network security strategy.
The post Cross-Site Scripting (XSS): Web App Enemy Number One appeared first on The Crazy Programmer.
No comments:
Post a Comment