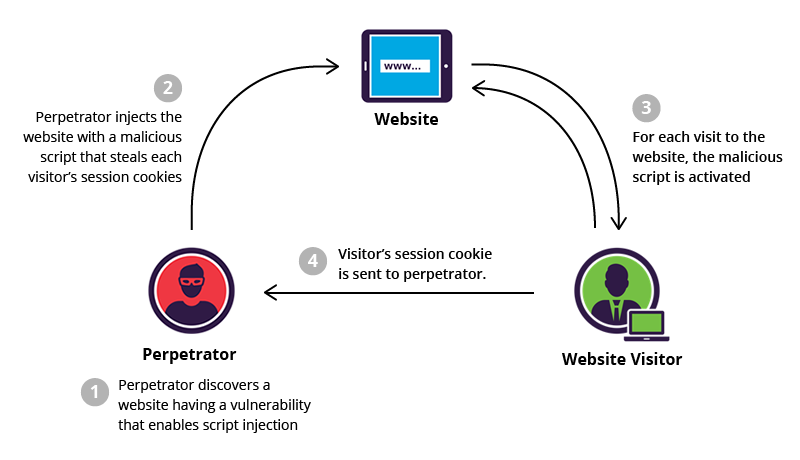
WordPress comes with an intuitive visual editor that covers all your basic needs for posting content. No coding is needed. However, when making custom pages or posts, you might need to add your own PHP code.
How to add PHP to a WordPress page or post properly? Read on, I’ll present the easiest way to do that just below.
What is PHP?
PHP is a recursive-acronym that stands for PHP: Hypertext Preprocessor, a server-side scripting language used for web development.
As a scripting language, PHP is used to handle routine tasks, which means using the same code for repetitive tasks, like displaying today’s time on a website, for example.
Being a server-side language, it requires a PHP module installed on the server for processing PHP scripts. The script can be embedded into an HTML file, and once interpreted, will be displayed in the browser.
Here’s a very basic example of a PHP script:
<?php echo 'Hi, Guys!'; ?>
And here’s the output as seen on a web browser:

Before moving on to the how’s, it is important to ensure your WordPress knowledge is up to snuff. Adding PHP code to WordPress requires you to have at least basic knowledge of how WordPress works. There are many websites like HostingWiki that can widen your horizons about WordPress and everything related to web development.
How to Add PHP to WordPress?
Now, let’s learn how to add PHP to WordPress in two different scenarios: using a plugin and modifying the functions.php file. I’ll start with the easiest one.
Using a Plugin
To add the code, using a plugin to your WordPress site can be a hassle-free option.
Here are the steps that you need to do:
- Login to your WordPress dashboard.
- Go to the plugin menu and click Add New.
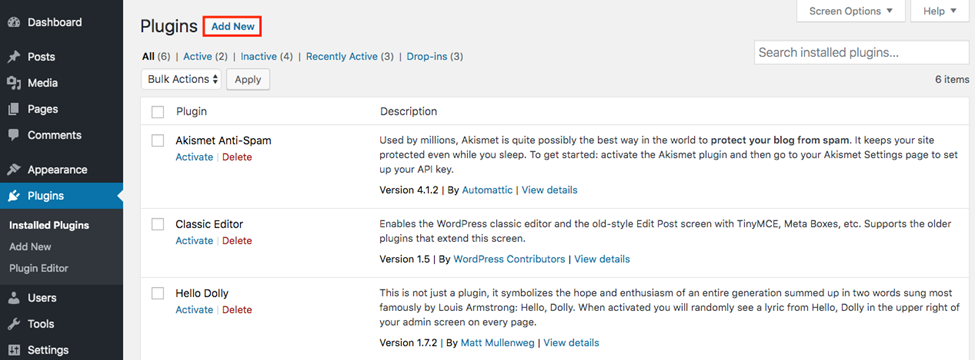
- Choose your favorite plugin. I recommend Insert PHP Code Snippet among others — It is easy to use and works well both on classic and Gutenberg editors.
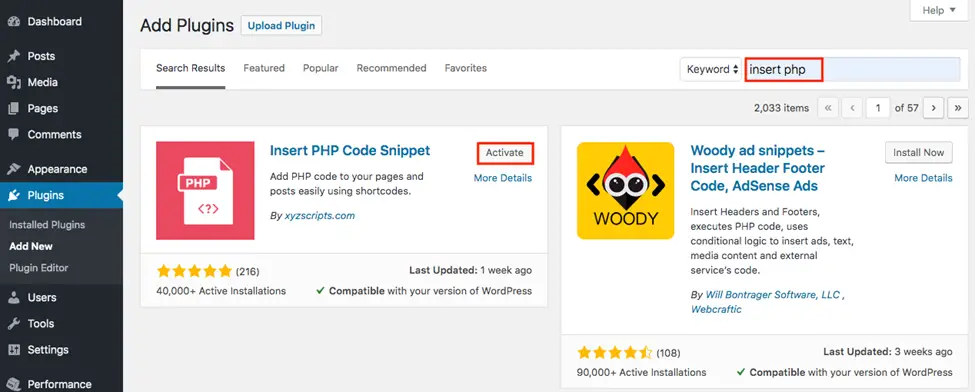
- Install, and activate the plugin.
- Once done, let’s move on to the insertion step.
Here are the steps to add the PHP code into WordPress once you have the plugin:
Creating the PHP code Snippet
- First off, you need to create the code snippet. On your WordPress dashboard go to XYZ PHP code, and click PHPcode Snippets.
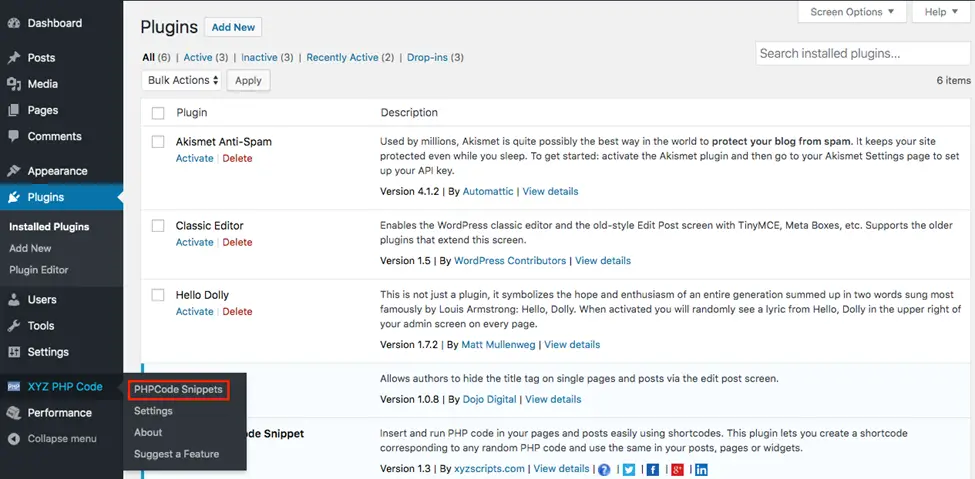
- On the PHPcode Snippet page, choose Add New PHP Code Snippet.
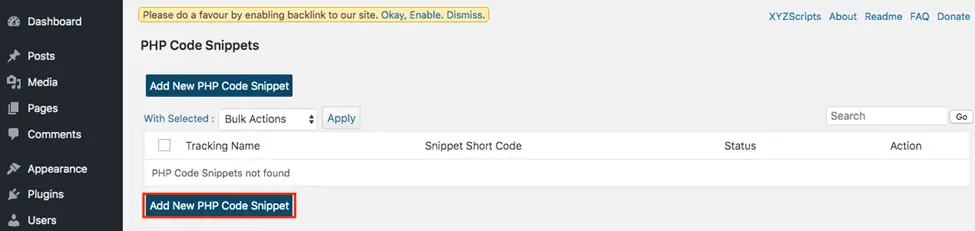
- Add the PHP code in the blank field as well as the Tracking name, then click Create.
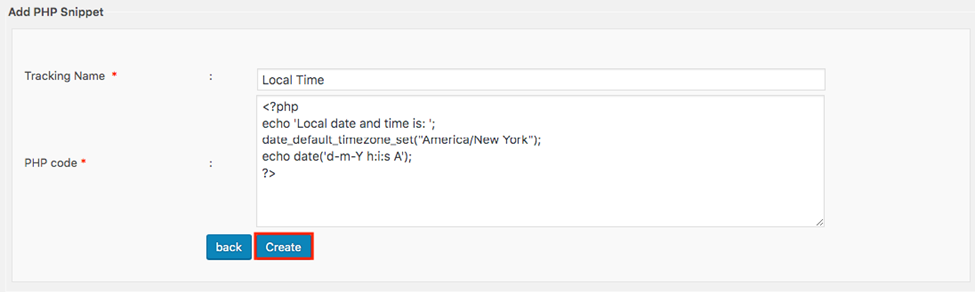
I use this code as an example:
<?php
echo 'Local date and time is: ';
date_default_timezone_set("America/New York");
echo date('d-m-Y h:i:s A');
?>
- Once created, you’ll see the snippet shortcode.
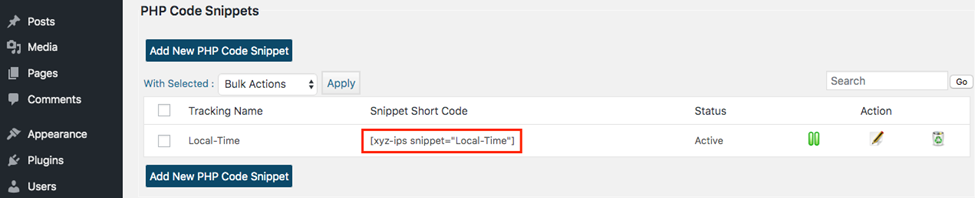
Adding the Snippet Short Code to a WordPress Post
The next thing is to insert the shortcode on your post. Here, I would like to show you how to do it using the Gutenberg editor.
- From the WordPress dashboard, under the Posts menu, click Add New.
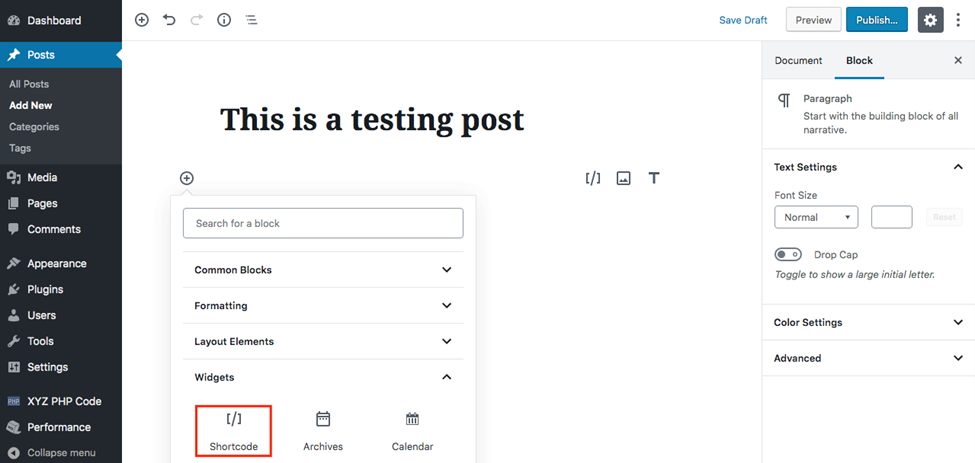
- Click the plus In the Widgets drop-down menu, choose Shortcode.
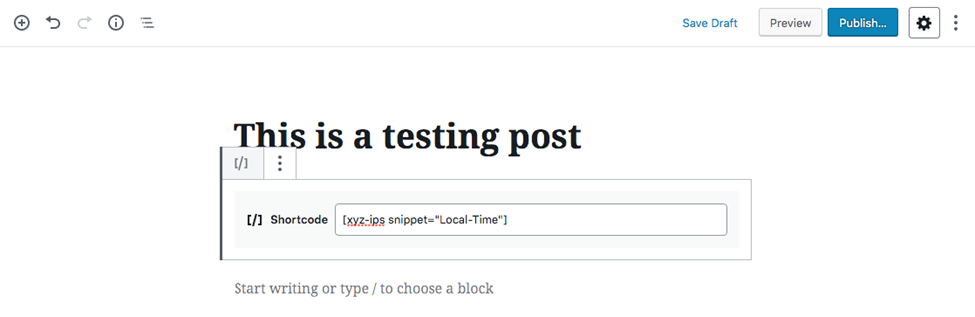
- Copy/paste the snippet shortcode you created using the plugin.
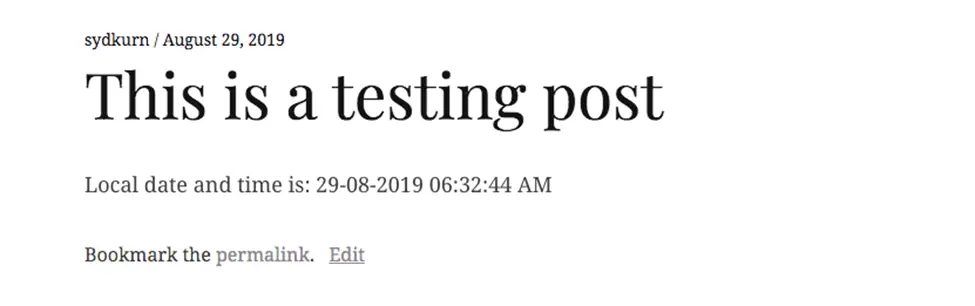
- And here is the post published:
Adding PHP to a WordPress Page
Adding PHP to a page is very similar to adding PHP to a post, nonetheless, there are a few differences as I will be using the classic editor this time around.
- From the WordPress dashboard go to the Pages menu, click Add New.
- From the formatting toolbar, you’ll see the PHP icon. Click that icon and choose the snippet code you want to use. No need to copy and paste here. From the options, I chose Local Time which is the snippet I’ve created earlier.
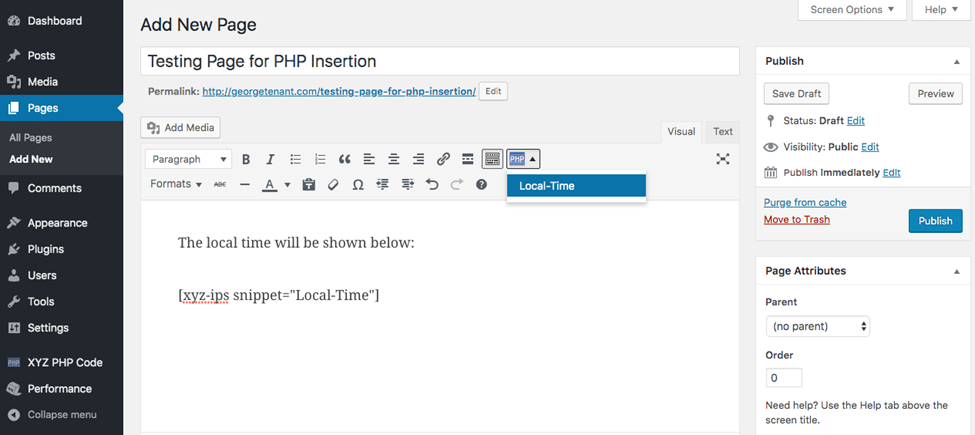
- The result when your page is published:

Add PHP to WordPress Manually Using the functions.php File
You can also add the PHP code directly to your WordPress theme. For that purpose, you need to modify the functions.php file of the current theme you’re using. Backup your data first, before doing anything else, just in case something goes wrong!
Also, I recommend you to create a child theme, a sub-theme that has the same code and appearance but it can be used as a “dummy” in case any issues occur.
Here are the steps:
- From the WordPress dashboard, go to the Appearance menu, and choose the Theme Editor.
- On the right side, you’ll see Theme Files. Choose Theme Function or functions.php.
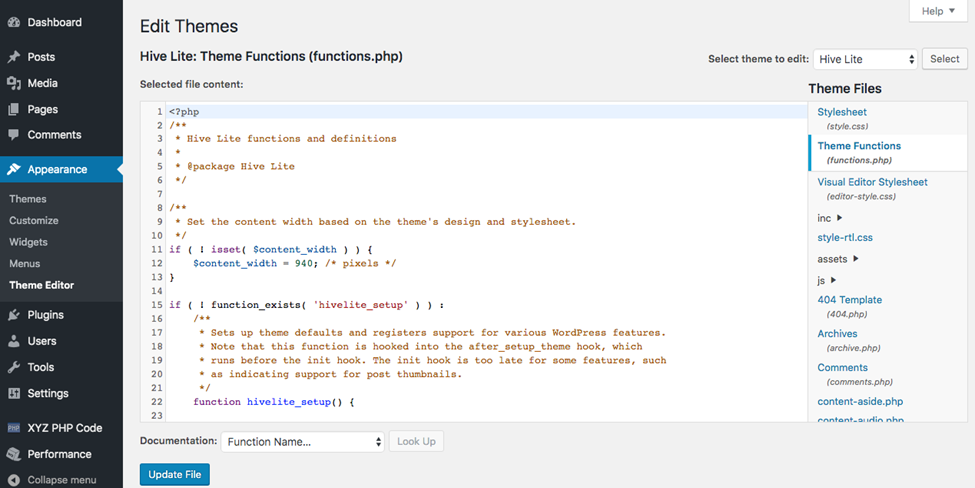
- Add or modify the PHP code for your content
- Once finished, click Update File.
Using this method will change all your posts under the same theme. That means for individual changes, using a plugin should be the preferred option. Also, when you update your theme, you might lose your modifications.
Wrap Up
Adding PHP to a WordPress page or post should not be taken lightly. Otherwise, you might make a mistake that will break your site (always use backups!).
There are two methods to insert PHP code in WordPress: using a plugin and manually adding it into the functions.php file.
The first option is ideal for individual posts or pages while doing it manually can apply your code throughout your entire WordPress theme.
Remember to always make a backup for your WordPress site before modifying it, and good luck coding!
The post How to add PHP to a WordPress Page or Post? appeared first on The Crazy Programmer.