It hasn’t been long since we heard of the Wawa card breach following a malware attack. Now, the attackers have
Wawa Card Breach Becomes Huge Problem Since 30M Stolen Cards Are Put Online For Sale on Latest Hacking News.
It hasn’t been long since we heard of the Wawa card breach following a malware attack. Now, the attackers have
Wawa Card Breach Becomes Huge Problem Since 30M Stolen Cards Are Put Online For Sale on Latest Hacking News.
ESET research into a campaign of the Winnti Group – The FBI warns of a job scam – What IoT legislation means for device makers and users
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
As the teams prepare to battle it out on the gridiron, fraudsters are waiting to intercept your funds
The post Don’t get sacked! Scams to look out for this Super Bowl appeared first on WeLiveSecurity
Streaming is probably not a new phenomenon to you, as streaming services provided by companies such as YouTube and Spotify
6 Best Websites for Streaming on Latest Hacking News.
ESET researchers uncover a new campaign of the Winnti Group targeting universities and using ShadowPad and Winnti malware
The post Winnti Group targeting universities in Hong Kong appeared first on WeLiveSecurity
A serious vulnerability existed in the Zoom video conferencing app that the vendor has recently patched. The flaw in the
Critical Flaw in Zoom Could Allow Attackers to Mess With Meetings on Latest Hacking News.

Have you cleared the first round of calls with the HR? Are you going for a Python interview in person? If you’re wondering what Python-related questions may be asked, this guide should be of help.
In the first section, we’ll discuss a few questions about Python's philosophy — those that help you make decisions about the architecture of a project. In the next section, we cover questions related to the Pythonic way of programming — which may manifest in the form of review or finding the output of a code snippet.
A word of caution before we start. This guide talks primarily about Python's built-in capabilities. The aim of this guide is to help you get up to speed with the inherent Python functionalities that enable quick development. So we won't be able to cover every question you may face from the various types of companies out there.
If you’re interviewing for a Python role, you should have a clear idea of what Python is and how it’s different from other programming languages. Here are a few key points regarding Python that you should be aware of.
First, you should not be wrong about the etymology. A large section of Python programmers wrongly think that Guido van Rossum named it after the snake! On the contrary, Python is named after British sketch comedy Monty Python's Flying Circus. The next time you see a Python book with a snake on the cover, you may perhaps wish to stay away from it.
Next, Python is a high level, object-oriented, interpreted programming language. This means that Python code is executed line by line. Python is also dynamically typed, as it doesn’t require you to specify the type of variables when declaring them.
Given Python's ease of use, it has found uses for common automation tasks. Python is often the go-to scripting choice for programmers who know multiple languages. With the increasing popularity of Python-based web frameworks like Django and Flask, Python's share of the pie has increased significantly in recent years.
While it’s good to know about the capabilities of a programming language, it's also good to be aware of its limitations to truly comprehend the situations you need to be wary of.
The first limitation of Python is execution speed. Though development in Python is quick, executing a similar block of Python code is often slower compared to compiled languages such as C++. For this reason, hackathons often give Python programs some extra time for execution. There are ways to circumvent this issue, though. For instance, you can integrate Python with a compiled language like C to perform the core processing through the other language.
In a world which is going mobile first, Python is not native to mobile development. You will rarely find mobile applications developed in Python. The two major mobile operating systems, Android and iOS, don’t support Python as an official programming language.
In addition to Python's capabilities and limitations, a category of questions that are popular in interviews focuses around choosing between packages based on your requirements. Let’s look at one approach that you may take when tackling such questions.
Let's say you’re given a choice between Django and Flask to start a web application. The answer to this question should lie within an amalgamation of the requirements of the project and the culture of the organization.
At the outset, you should know that with the use of plugins, there’s no right answer here: you can create the similar applications using either framework. However, there’s a stark difference between the design philosophies of each framework. Flask provides you the bare minimum features for you to create a web application like URL routing, templating, unit testing and a development server, thereby giving you a lot of freedom to design your application. On the other hand, Django provides you a large array of built in features from the beginning — database support, extensive admin functionality, and security features.
If you’re building an application that will use relational databases, with a lot of dynamic content, you should probably choose Django. However, if you’re looking for a lot of freedom in your project, you should opt for Flask.
The post How to Tackle a Python Interview appeared first on SitePoint.
Companies of all sizes use computers to store data and records. Some of the data may include information that is
This Software Called Otter; What it is and what it does on Latest Hacking News.
Here is another incident to reemphasize the need for patching the serious Citrix vulnerability (CVE-2019-19781). A new ransomware called Ragnarok
Ragnarok Ransomware Exploits Citrix Vulnerability To Target Vulnerable Servers on Latest Hacking News.
No more default logins on new IoT devices if UK legislators get their way
The post IoT laws are coming: What to expect appeared first on WeLiveSecurity
Ryuk has now emerged within a new guise. In brief, the new strain of Ryuk Stealer exhibits advanced properties that
New Ryuk Stealer Targets Government And Military Sectors on Latest Hacking News.
In this era of rising cybercrimesand never-ending cyber attacks, having proactive cybersecurity policies is a must for every organization. Many
Why Organizations Need Manual Penetration Testing on Latest Hacking News.

In this multi-part series, I'll walk you through how I set up an on-premise machine learning pipeline with open-source tools and frameworks.
When most people think about machine learning, they imagine engineers and data scientists tweaking network architectures, loss functions, and tuning hyper-parameters, coupled with the constant retraining until the results are satisfactory.
Indeed, training machine learning models takes a lot of hard work. A tremendous amount of time and resources are expended on research and experimentation.
However, there comes a point in time when you need to start to productionize the model that you've lovingly trained and tuned. And oh, by the way, the model is expected to perform as well on next weeks' batch of data.
It slowly dawns on you that Machine Learning is much bigger than models, hyper-parameters, and loss functions. It's also what happens before, during, and after training. And it doesn't end there, because you would also need to think about re-training, especially when you get new data, since there's no guarantee that the model is going to generalize as well.
There's a very well known diagram that succinctly illustrates the issue:

In short, you need to build a machine learning pipeline that can get you from raw data to the trained model in the shortest possible time. But here's the catch: because you're part of a scrappy startup and not flushed with VC money, you're going to have to make do with the servers you have, and not rely on the paid cloud offerings of Amazon, Microsoft or Google, at least for the time being.
This is because you need a safe environment to learn and experiment in — one that won't unexpectedly shock you with a nasty bill at the end of the month.
You could be a software engineer at a company that's starting to think about putting its machine learning models to production, or you could be running solo and curious about what "real-world" machine learning looks like. In both cases, you would need to know about machine learning pipelines.
You should be comfortable with Linux. The examples will assume Ubuntu Linux 18.04, though slightly dated or more recent versions shouldn't cause any major issues.
You should have some working knowledge of Docker. If you know how to build images in Docker, and how to execute containers, you should be good to go. If you don't, you shouldn't worry too much: I'll guide you with enough background information, and code examples will be explained.
While this is an article about Machine Learning pipelines, this article is not about the intricacies involved in training a model.
We're going to use Kubernetes. You don't need to be an expert in it. If you are completely new to Kubernetes, that's OK. By the end of the series, you'll have at least some hands-on experience. On the other hand, I'm not going to go very deep into Kubernetes specifics. Some commands I'll have to gloss over in the interests of brevity. Besides, the real objective here to help you deploy machine learning pipelines as efficiently as possible.
Here are some other assumptions that I'm making about you, the astute reader:
Machine learning pipelines only recently have gotten more love and attention, and people are just only beginning to figure everything out. Put in another way, there are multiple ways to build machine learning pipelines, because every organization has unique requirements, and every team has their favorite tool.
What this series aims to offer is one possible way to do it, and that's especially important when you're starting out, because the amount of information is often very overwhelming. Also, installing Kubernetes is a daunting affair, littered with many roadblocks. I hope this article helps with smoothening that path.
After you've learned a way to build a machine learning pipeline, you'll then be equipped with enough skills and knowledge to go build one to suit your organization's needs.
Here's a list of some of the tools I'll cover in this series:
As you'll realize soon as you follow through the series, many of these tools assume that you have storage on Amazon S3 or Google Cloud Storage, which, to put it mildly, not a very good assumption. Thus this series shows how to work around some of these limitations without losing any of the functionality.
Of course, at some point in time, you'll outgrow and would need something more capable. However, especially when you're starting (that is, you happen to be the first Data Engineer on the team), then on-premise would seem a more cost-effective and ultimately the more educational choice.
Let's start immediately with one of the harder bits — Installing Kubernetes.
The main thing you need to know about Kubernetes is that it's a container-orchestration system for automating application deployment, scaling, and management.
There are many ways to install Kubernetes, and it’s not a trivial process. Fortunately, that's tools like Rancher make the installation process much more pleasant and less error-prone. In particular, we’re going to use the Rancher Kubernetes Engine (RKE) to help us install Kubernetes.
At the point of this writing, the latest stable release of rke is 1.0.0.
The following steps assume that you have access to two Linux machines that are connected to the same LAN.
We’re going to set up a minimal cluster consisting of two machines, one named master and the other worker. Of course, you can name your machines whatever you want, as long as you designate one machine to be master, and the rest to be workers.
If you only have access to one machine, you can get by with creating two virtual machines, and make sure to enable Bridged Adapter. In fact, in preparation for this article, I'm testing everything out of Oracle's VirtualBox. Here are my settings:
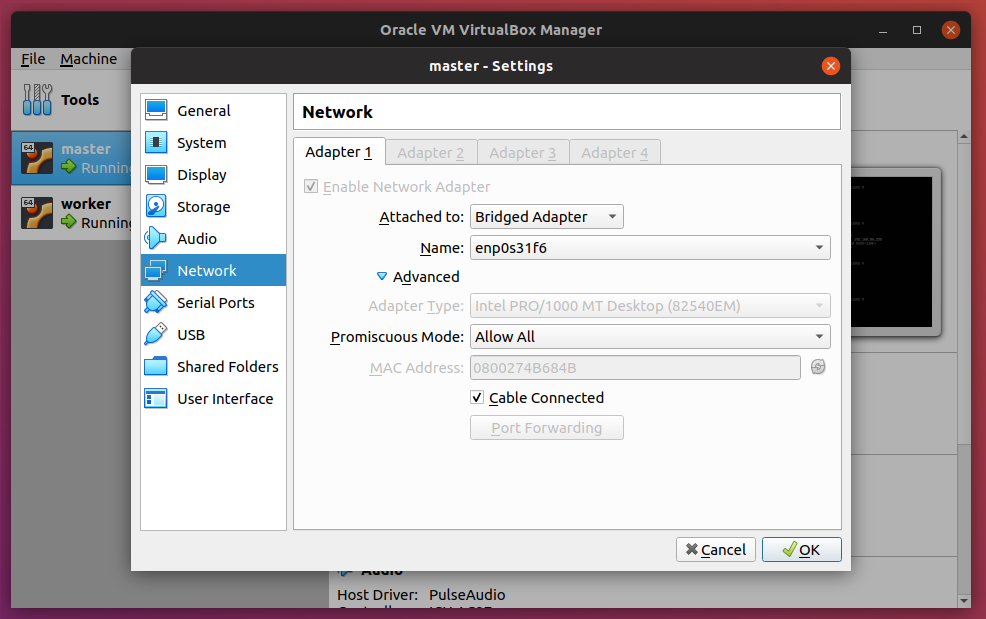
Notice here that I have two VMs: master and node. Enable the Bridged Adapter and also setting Promiscuous Mode to Allow All.
The downside to that is that you wouldn't be able to access the GPUs, and you would most likely notice that the performance won't be ideal because Kubernetes tends to be quite demanding in terms of resources. Again, that's OK if you’re trying this at home or have only access to a single machine at the moment.
Here are some important details about the machines (you should have them on hand too for the configuration steps that follow):
| Master | Worker | |
|---|---|---|
| IP | 192.168.86.36 | 192.168.86.35 |
| User | ubuntu | ubuntu |
| Hostname | master | worker |
| SSH Keys | ~/.ssh/id_rsa.pub |
~/.ssh/id_rsa.pub |
| Role | Control Plane, Etcd | Worker |
In a production environment, you would need a hostname to point to your Kubernetes cluster. However, in this article I'm assuming you don't have one readily available, so we're going to have to fake it.
Another thing I won't cover — to keep things simple — is load balancing when it comes to the Rancher installation.
For our purposes, I'm going to use rancher-demo.domain.test as the hostname.
In both machines, open /etc/hosts file:
sudo vim /etc/hosts
Enter the following:
192.168.86.35 worker
192.168.86.35 rancher-demo.domain.test
192.168.86.36 master
127.0.0.1 localhost
Notice here that the worker node has the additional hostname of rancher-demo.domain.test. In a slightly more realistic environment, you'd have something like NGINX as a front-end to load balance between multiple worker nodes.
*Note: If you're using a Virtual Machine, then most likely you'd be using the Ubuntu Server image, which typically doesn't come with a desktop environment. Therefore, you should also have an entry in the host computer to include this:
192.168.86.35 rancher-demo.domain.test
That way, you'll be able to access Rancher from a browser on the host computer.*
rke BinaryImportant!: This step should only be performed on master.
Head over to the GitHub page to download the rke binary. Next, rename the binary to rke, followed by making it executable. Finally, move the binary to a location in the PATH, where /usr/local/bin is usually a good choice.
Important: make sure you select the right binary for your OS!
$ wget https://github.com/rancher/rke/releases/download/v1.0.0/rke_linux-amd64
$ mv rke_linux-amd64 rke
$ chmod +x rke
$ sudo mv rke /usr/local/bin
Now let's see if everything works:
$ rke
This should return:
NAME:
rke - Rancher Kubernetes Engine, an extremely simple, lightning fast Kubernetes installer that works everywhere
USAGE:
rke [global options] command [command options] [arguments...]
VERSION:
v1.0.0
AUTHOR(S):
Rancher Labs, Inc.
COMMANDS:
up Bring the cluster up
remove Teardown the cluster and clean cluster nodes
version Show cluster Kubernetes version
config Setup cluster configuration
etcd etcd snapshot save/restore operations in k8s cluster
cert Certificates management for RKE cluster
encrypt Manage cluster encryption provider keys
help, h Shows a list of commands or help for one command
GLOBAL OPTIONS:
--debug, -d Debug logging
--quiet, -q Quiet mode, disables logging and only critical output will be printed
--help, -h show help
--version, -v print the version
The post Machine Learning Pipelines: Setting Up On-premise Kubernetes appeared first on SitePoint.

This article was created in partnership with GoGetSSL. Thank you for supporting the partners who make SitePoint possible.
Over the last decade, the rate of cyber crime has risen sharply. Already, many reputable business organizations and government agencies that haven't implemented sufficient online security have been caught with their pants down. Google has started taking a strong stand against websites that don’t use HTTPS. Website visitors will be notified if they’re about to submit any information over an unsecured connection.
In this article, you’ll learn how to protect your customers and your business from privacy invasion and data theft. You’ll learn how to use SSL technology to secure your websites and your applications from leaking sensitive data to eavesdroppers.
I won't be able to show you how to install SSL, as that's an advanced topic. You can find more information on the installation process here.
Imagine you're in your hotel room, on your laptop, connected to the hotel's WIFI. You're about to log in to your bank's online portal. Meanwhile, a nefarious hacker has cleverly booked a room next to yours and has set up a simple workstation that listens to all network traffic in the hotel building. All traffic using the HTTP protocol can be seen by the hacker in plain text.
Assuming the bank's website is using only HTTP, form details such as user name and password will be seen by the hacker as soon you press submit. So how do we protect this data? The answer is obviously encryption. Encryption of data involves converting plain text data to something that looks garbled — aka encrypted data. To encrypt plain text data, you need what's called an encryption algorithm and a cipher key.
Let's say you were to encrypt the following data:
Come on over for hot dogs and soda!
It will look something like this in encrypted form:
wUwDPglyJu9LOnkBAf4vxSpQgQZltcz7LWwEquhdm5kSQIkQlZtfxtSTsmaw
q6gVH8SimlC3W6TDOhhL2FdgvdIC7sDv7G1Z7pCNzFLp0lgB9ACm8r5RZOBi
N5ske9cBVjlVfgmQ9VpFzSwzLLODhCU7/2THg2iDrW3NGQZfz3SSWviwCe7G
mNIvp5jEkGPCGcla4Fgdp/xuyewPk6NDlBewftLtHJVf
=PAb3
Decrypting the above message without the cipher key can take more than a lifetime using current computing power. No one can read it unless they have the cipher key that was used to encrypt it. This type of encryption is known as symmetric encryption. Now that we've figured out how to protect data, we need a safe way to transmit the cipher key to the recipient of the message safely. We can do this by using an asymmetric encryption system known as public key cryptography.
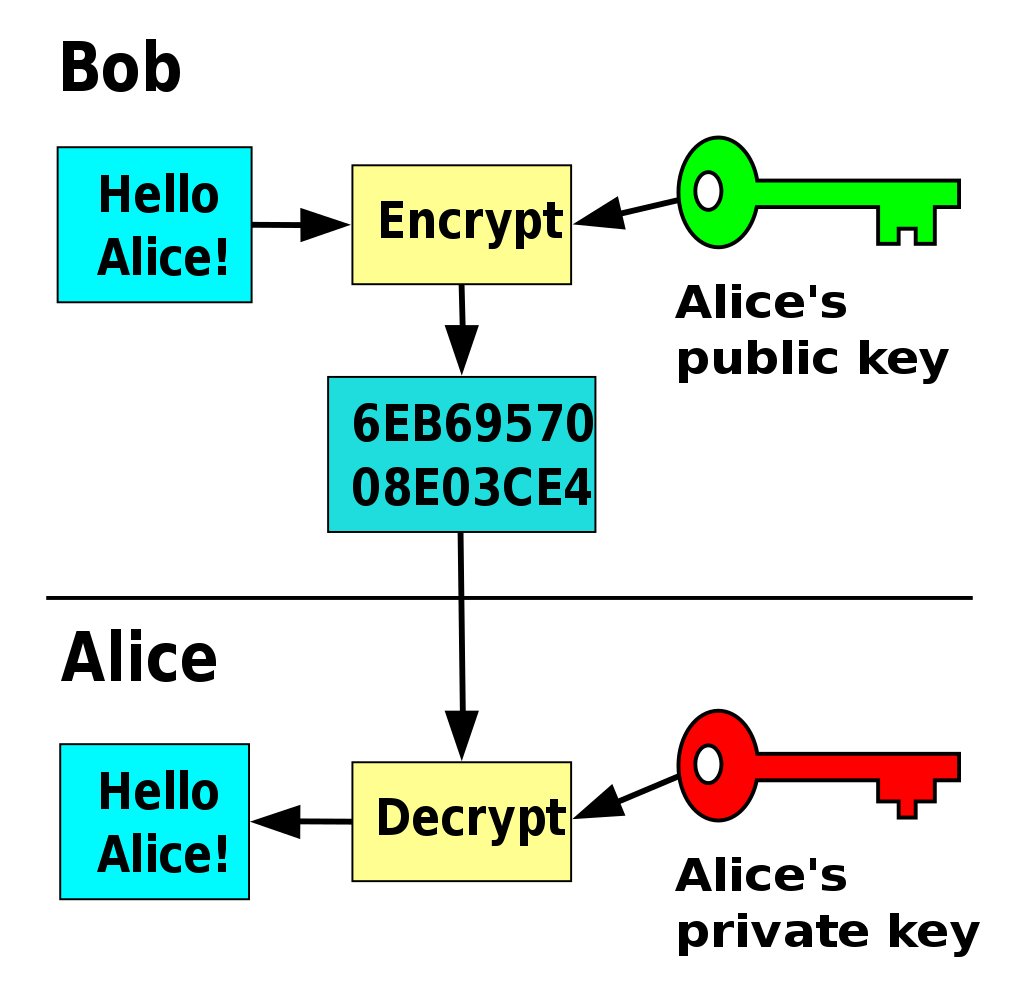
Public Key Cryptography uses a pair of mathematically related cipher keys:
When one key is used to encrypt, the other one is used to decrypt. The same key can't be used to decrypt what it encrypted. Below is a depiction of how it works:
However, we can't trust any public key issued to us since they can be generated by anyone. To ensure authenticity of public keys, they need to be packaged in what's called an SSL certificate. This is a signed digital file that contains the following information:
I've only listed the necessities. SSL certificates usually contain more information. Here's a real-world example:
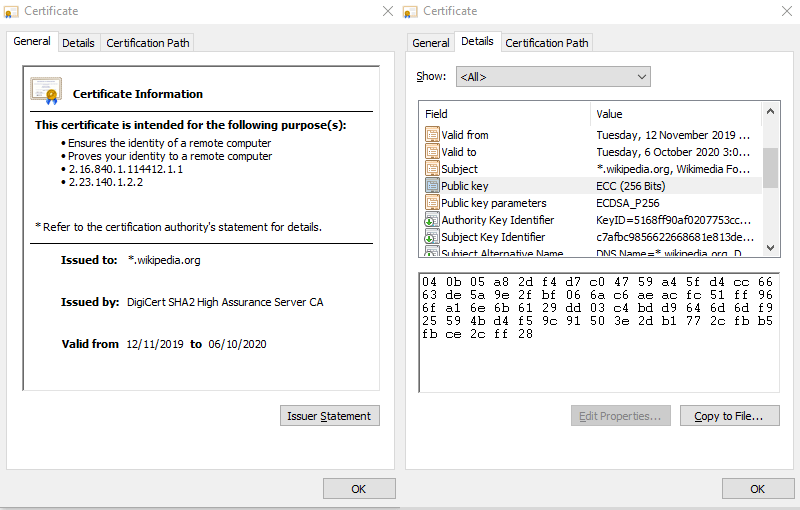
As you can see, the above certificate has been signed (see thumbnail section). A digital signature is simply an encrypted hash of a file. Let's first explain what a hash is. Say you have a 100-word document, and you run it through a hashing program. You'll get the following hash:
46798b5cfca45c46a84b7419f8b74735
If you change anything in the document, even if it's adding single full stop, a completely new hash will be generated when you run the hashing function again:
bc527343c7ffc103111f3a694b004e2f
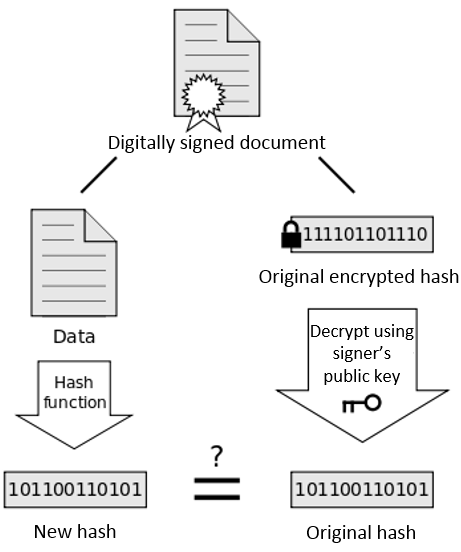
A mismatch in the hash between the hash sent and the one generated means that the file has been altered. This is the first line of defense for ensuring that an SSL certificate hasn’t been altered. However, we need to verify that sent hash was created by the issuer of the certificate. This is done by encrypting the hash using the issuer's private key. When we perform a local hash of the certificate, then decrypt the certificate's signature to obtain the sent hash, we can compare the two. If there’s a match, it means:
Now, you may be wondering where we get the issuer's public key and why we should trust it. Well, the issuer's public key already comes pre-installed inside our operating systems and browsers. An issuer is a trusted certificate authority (CA) that signs certificates in compliance with the official CA/Browser Forum guidelines and NIST recommendations. For example, here’s a list of trusted issuers/CAs that you’ll find on Microsoft's Operating System. Even smartphones and tablets have a similar list pre-installed on the OS and browser.
According to a survey conducted by W3Techs on May 2018, the following issuers account for about 90% of valid certificates signed globally:
Now that you have an understanding of encryption and SSL technology, it's best to go over how you can safely sign in to your bank's portal using HTTPS without the hacker next door reading your traffic.
This means both form data going from the laptop, and HTML data coming from the server, will be encrypted using a cipher key that the hacker won't have access to. All that will be seen in the captured traffic logs will be garbled letters and numbers. Your information has now been protected and kept private from prying eyes.
Now that you understand how SSL in general works, let's move on to the next section an look at the different types of SSL certificates we can use.
The post What SSL Is, and Which Certificate Type is Right for You appeared first on SitePoint.
The German City of Potsdam has become the latest victim of a cyber attack. Following the attack, the city services
City Of Potsdam Went Offline After Suffering A Cyber Attack on Latest Hacking News.
The illusion of security in IT is as fragile as a spiders-web; especially for a company that is built upon
5 Reasons Every Company Requires A Network Audit for Security Reasons on Latest Hacking News.

This article was created in partnership with Print Peppermint. Thank you for supporting the partners who make SitePoint possible.
Everyone has a business card—is yours any different? Designing the ideal card for your business is a project that deserves real time and thought. For a fresh approach, consider Print Peppermint. Their in-house design services ensure your business cards will be absolutely custom and unique, and their high-end special finishes add a touch of class.
They’re not the new kids on the block. Over the last seven years, they’ve produced thousands of innovative print projects, and have attracted the business of industry-leading creative companies such as Vice, Google, Geico, Wendy’s. They’ve even printed circular die-cut business cards for Grammarly—one of our office-favorite web apps! They can hand-craft something unique for you, too.
You could get started with their Free Online Design Tool. It’s an easy-to-use online app that will help you design your own business cards, posters, flyers, invitations, and greeting cards from a blank canvas.
But you’ll get the best results if you leave the design work to the experts, and hire one of their in-house graphic designers. Give them as much input as you can—sketches, ideas, links to anything that inspires you—and they’ll bring it to life in a fresh, unique way. They can even design a logo for your business. Every single order is hand-proofed, no matter how large or small.
But what you put on your business card is just the start. Give some serious thought to the card itself.
First, the paper you print on can make a very tactile impression. Choose from a meticulously-curated family of thick and premium papers, including 100% Cotton, Soft-Touch, Triplex Layered, Clear-Frosted Plastic, Onyx Black Suede, Recycled Kraft, and many more.
Second, choose from a wide range of special finishes. They stand out and make a strong statement about your business. These include foil stamping, die-cutting, embossing, letterpress, edge painting, and more.
The ideal combination of design, paper, and finish creates a strong impression. Here are a few examples of what you can achieve.
A “letterpress finish” can be engaging, and debossing makes an impression, literally. Here’s blind debossing on thick, cotton paper.
By using clear plastic, your business cards will be as durable as credit cards. Frosted PVC makes a statement to your customers that you have high standards and care about quality.
Metallic foil stamped business cards have a premium look. Choose from 15 colors—here’s one in copper. You can even make photos metallic.
Raised foil feels more dramatic, similar to embossing. Here’s how it looks in gold on premium suede, soft-touch paper.
If you find rectangles boring, you can have your business cards die cut to absolutely any custom shape. Imagine the possibilities!
And even the edges of your cards can be custom painted.
The right business card ensures the perfect introduction to your business, so take your time deciding on a design. Possibly the best way to get inspiration is to order their $10 Sample Pack. You’ll be able to touch, smell and explore over twenty premium products and papers, and as a bonus you’ll get $25 off your order. That sounds like a good deal to me.
Another excellent source of inspiration is the company’s design blog. It’s filled with articles on topics like Graphic Design and Photography, but you’ll want to start in the Business Card Inspiration section. If you get stuck designing your own card, it can be really helpful to look at what other people have come up with. The blog contains over 200 articles that explore recently-completed business card projects.
How do you feel about your current business card now? If you’re ready for something new, all Print Peppermint products are supported with a 100% money-back quality guarantee. They offer amazing group-order discounts for businesses and organizations with multiple employees.
Armed with the right business card, all you need now is to perfect how to hand out your business card with style!
The post Leave an Impression with Print Peppermint’s Fresh Designs & Premium Paper appeared first on SitePoint.
In the past weeks, Mozilla has banned 197 Firefox add-ons for malicious activity. Not only have they removed the add-ons
Mozilla Bans 197 Malicious Firefox Add-Ons Amidst Crackdown on Latest Hacking News.
The league and scores of teams were caught off-guard by the re-emergence of an infamous hacking group
The post Hackers blitz social media accounts of 15 NFL teams appeared first on WeLiveSecurity
Have you had a Google Privacy Checkup lately? If not, when better than international Data Privacy Day to audit the privacy of your Google account?
The post How to take charge of your Google privacy settings appeared first on WeLiveSecurity
The Japanese electronics giant Mitsubishi Electric disclosed a hack last week. It now turns out that the attackers exploited a
Hackers Exploited Trend Micro Antivirus Zero-day In Mitsubishi Electric Hack on Latest Hacking News.

Almost all web applications require server-based data storage, and MySQL continues to be the most-used database solution. This article discusses various options for using MySQL on your local system during development.
MySQL is a free, open-source relational database. MariaDB is a fork of the database created in 2010 following concerns about the Oracle acquisition of MySQL. (It's is functionally identical, so most of the concepts described in this article also apply to MariaDB.)
While NoSQL databases have surged in recent years, relational data is generally more practical for the majority of applications. That said, MySQL also supports NoSQL-like data structures such as JSON fields so you can enjoy the benefits of both worlds.
The following sections examine three primary ways to use MySQL in your local development environment:
MySQL services are offered by AWS, Azure, Google Cloud, Oracle, and many other specialist hosting services. Even low-cost shared hosts offer MySQL with remote HTTPS or tunneled SSH connections. You can therefore use a MySQL database remotely in local development. The benefits:
The downsides:
A cloud-based option may be practical for those with minimal database requirements or large teams working on the same complex datasets.
Docker is a platform which allows you to build, share, and run applications in containers. Think of a container as an isolated virtual machine with its own operating system, libraries, and the application files. (In reality, containers are lightweight processes which share resources on the host.)
A Docker image is a snapshot of a file system which can be run as a container. The Docker Hub provides a wide range of images for popular applications, and databases including MySQL and MariaDB. The benefits:
Docker is beyond the scope of this article, but key points to note:
Instructions for installing the latest version of Docker on Linux are available on Docker Docs. You can also use official repositories, although these are likely to have older editions. For example, on Ubuntu:
sudo apt-get update
sudo apt-get remove docker docker-engine docker.io
sudo apt install docker.io
sudo systemctl start docker
sudo systemctl enable docker
Installation will vary on other editions of Linux, so search the Web for appropriate instructions.
Docker CE Desktop for macOS Sierra 10.12 and above and Docker CE Desktop for Windows 10 Professional are available as installable packages. You must register at Docker Hub and sign in to download.
Docker on Windows 10 uses the Hyper-V virtualization platform, which you can enable from the Turn Windows features on or off panel accessed from Programs and Features in the the Control Panel. Docker can also use the Windows Subsystem for Linux 2 (WSL2 — currently in beta).
To ensure Docker can access the Windows file system, choose Settings from the Docker tray icon menu, navigate to the Shared Drives pane, and check which drives the server is permitted to use.

Check Docker has successfully installed by entering docker version at your command prompt. Optionally, try docker run hello-world to verify Docker can pull images and start containers as expected.
To make it easier for Docker containers to communicate, create a bridged network named dbnet or whatever name you prefer (this step can be skipped if you just want to access MySQL from the host device):
docker network create --driver bridge dbnet
Now create a data folder on your system where MySQL tables will be stored — such as mkdir data.
The most recent MySQL 8 server can now be launched with:
docker run -d --rm --name mysql --net dbnet -p 3306:3306 -e MYSQL_ROOT_PASSWORD=mysecret -v $PWD/data:/var/lib/mysql mysql:8
Arguments used:
-d runs the container as a background service.--rm removes the container when it stops running.--name mysql assigns a name of mysql to the container for easier management.-p 3306:3306 forwards the container port to the host. If you wanted to use port 3307 on the host, you would specify -p 3307:3306.-e defines an environment variable, in this case the default MySQL root user password is set to mysecret.-v mounts a volume so the /var/lib/mysql MySQL data folder in the container will be stored at the current folder's data subfolder on the host.$PWD is the current folder, but this only works on macOS and Linux. Windows users must specify the whole path using forward slash notation — such as /c/mysql/data.
The first time you run this command, MySQL will take several minutes to start as the Docker image is downloaded and the MySQL container is configured. Subsequent restarts will be instantaneous, presuming you don’t delete or change the original image. You can check progress at any time using:
docker logs mysql
Once started, open a bash shell on the MySQL container using:
docker exec -it mysql bash
Then connect to the MySQL server as the root user:
mysql -u root -pmysecret
-p is followed by the password set in Docker's -e argument shown above. Don’t add a space!
Any MySQL commands can now be used — such as show databases;, create database new; and so on.
Any MySQL client application can connect to the server on port 3306 of the host machine.
If you don't have a MySQL client installed, Adminer is a lightweight PHP database management tool which can also be run as a Docker container!
docker run -d --rm --name adminer --net dbnet -p 8080:8080 adminer
Once started, open http://localhost:8080 in your browser and enter mysql as the server name, root as the username, and mysecret as the password:
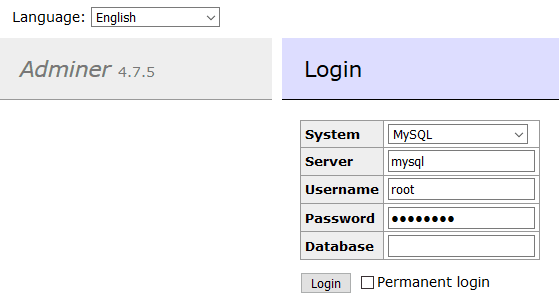
Databases, users, tables, and associated settings can now be added, edited, or removed.
The post How to Install MySQL appeared first on SitePoint.
Hacking specialists and penetration testers are the new norms of the modern era. With many companies now being based online
5 of the Most Popular Penetration Testing Tools Found in Kali Linux on Latest Hacking News.
Cybercriminals are putting a new twist on an old trick
The post Job hunting? Beware hiring scams using spoofed company websites appeared first on WeLiveSecurity

This sponsored article was created by our content partner, BAW Media. Thank you for supporting the partners who make SitePoint possible.
The start of a new year is always an exciting time. Everyone makes pledges to be better, to feel better, to do better. But like many New Years’ resolutions that quickly get tossed aside or forgotten, fad-like web design trends have a tendency to follow a similar path.
That’s because it’s easy to get wrapped up in what’s cool now instead of focusing on what we can do to make a website grow stronger with each passing day.
Have a look at BeTheme and its 500+ pre-built websites. These clean and classic designs have real staying power.
That’s because they’re centered around strong design principles. Not flashy color palettes, hip font choices, or technology your users aren’t ready for or don’t need. And that’s the key, right?
You’re building websites for the end user — not for yourself.
Spending your time using web design trends that will come and go is making barely any impact on your visitors. You can take advantage of these tried, tested, and long-lasting web design trends …
One of the awesome advantages of the Web moving towards a more mobile-first experience is that websites viewed on desktop have become simpler and easier to navigate, too.
With more consumers flocking to the Web on their smartphones, website menus have had to shrink in size. Not only in terms of the space they comprise, but also in the number of links.
In 2020 and onwards, websites will have only the most essential of pages in the primary menu. Secondary links will be relegated to areas like the footer and sidebar. Consequently, this will help to clean up on-page designs. They won’t be so littered with call-to-action buttons pointing to internal pages.
The BeRepair pre-built site is a beautiful example of this. With its navigation tucked away under a hamburger menu icon:
When opened, the pop-out menu follows the trend of less-is-more. It has a short and simple-to-navigate list of links surrounded by a bunch of white space:
Non-traditional navigations can also benefit from this form of minimalism. BeGarden demonstrates this with its left-aligned menu:
Users are overloaded with content, offers, and other distractions every time they hit the Internet. Do you really want your website to be one more thing that causes them stress and, in turn, indecisiveness?
When you design with white space, it gets you out of the habit of trying to put as much information and as many options into a single section or page as possible. Instead, it encourages you to do more with less.
Concise messaging + Wide, open spaces = Good for your conversion rate.
Take, for instance, this brief but powerful video banner at the bottom of BeWine:
You can find other ways to let strong yet simple imagery tell your brand’s story, as the BeWeddingPlanner site does:
The post 5 Web Design Trends for 2020 with Real Staying Power appeared first on SitePoint.
Researchers have discovered six different critical MDhex vulnerabilities, in medical devices. These vulnerabilities, upon exploitation, could allow an adversary to
MDhex Vulnerabilities Discovered In GE Healthcare Medical Devices on Latest Hacking News.
Cisco have recently fixed numerous security bugs in multiple products. These also include a critical security fix in Cisco Firepower
Cisco Patched Critical Bug In Firepower Management Center on Latest Hacking News.
LastPass has recently troubled users when it locked out people from accessing their accounts due to a bug. Once again,
Another LastPass Outage After Chrome Extension Mistakenly Left Chrome Store on Latest Hacking News.
Zero-day in Internet Explorer – Microsoft cloud leaked big – Dating apps accused of sharing user data with advertisers
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
Safari’s anti-tracking feature could apparently give access to users’ browsing habits
The post Google: Flaws in Apple’s privacy tool could enable tracking appeared first on WeLiveSecurity
Databases containing 14 years’ worth of customer support logs were publicly accessible with no password protection
The post Microsoft exposed 250 million customer support records appeared first on WeLiveSecurity
While security breaches are common, the latest report relates to the tech giant Microsoft. Reportedly, Microsoft has disclosed a security
Microsoft Disclose a Security Breach Affecting One of Their Own Customer Support Databases on Latest Hacking News.
After years of usage, your iPhone works slowly. So, you’ve decided to sell it out and upgrade to an new
UkeySoft FoneEraser Review: 100% Erase All iOS Data before Selling Your iPhone/iPad/iPod on Latest Hacking News.
It seems that every iOS user needs an iPhone unlocking software. If you try to enter the wrong unlock password
UkeySoft Unlocker Review: Best Tool to Unlock Apple ID & Screen Lock on Latest Hacking News.
Whether you’re aware of it or not, you’re surely using artificial intelligence (AI) on a daily basis. That’s because it powers-up a lot of the most commonly used products today. From Google and Spotify to Siri and Facebook, all of them use Machine Learning (ML), one of AI’s subsets.
ML allows those sites to serve better and more personalized content, automate processes, and constantly optimize its workings, among other things. It does so through sophisticated algorithms called models. These are mathematical expressions that stand in as a representation of data in a particular context.
As such, models are essential to analyze the information and get insights out of it. Maybe you’re trying to start a career as a data scientist or want to outsource development of an ML-based application. Whatever your motivation, you’ve come to the right place to learn the basics of the most popular machine learning models.
Depending on the approach you want to take to process the data, you’ll use one of the 2 main categories of machine learning: supervised and unsupervised machine learning.
Supervised machine learning techniques use known inputs and outputs to identify patterns and understand how the results came to be. It uses training sessions and data sets to comprehend the underlying mechanism of the information. Thus, whenever you introduce a new input that wasn’t part of the training data set, you can get a probable outcome calculated with the identified pattern.
ML developers and software outsourcing companies that focus on AI use supervised machine learning in fields as diverse as chemistry, manufacturing, and marketing.
Unsupervised machine learning, on their part, is a more exploratory approach to data analysis. Instead of understanding data relationships from training examples, it uses unlabeled data to detect potential patterns you didn’t previously know. It does so by grouping similar inputs together based on their traits.
A lot of engineers use this approach in different industries. It’s especially useful for research, though you can use it to get insights from your sales department, your product pricing, or your logistics.
The possibilities you can find in both approaches are endless, as you can use them in any way you can imagine. Of course, before you launch yourself to do that, you have to know some of the basic models you have available.

This method is a part of the supervised machine learning category. Its basic goal is to explain or predict a class value. In other words, this model defines the probability of something happening according to one or more inputs.
For example, you can use classification in an email client to filter spam. In this scenario, you have 2 possible outcomes: an email is spam or it isn’t. Depending on the inputs, the model could predict that based on how you trained it. In fact, you’re doing just that whenever you flag a message as spam in your email account – you’re training the model to understand the basic traits of spam and enhance its protection.
In short, classification is a method that predicts a class label depending on the training set and its values (which defines the class labels in the first place). This technique encompasses several models, including logistic regression, decision trees, random forests, multilayer perceptrons, and gradient-boosted trees, among others.
Clustering includes several methods that are part of the unsupervised machine learning category. As such, you can use it on unlabeled data sets to group values according to one or more specific traits or characteristics. The result? The algorithms form groups (called clusters) of similar values.
For that to happen, you need to define a similarity measure, which is simply a metric that looks at one or more features. Once you have this measure, you can apply it to the data set to have clusters. For instance, you could have a lot of music albums that you could categorize by genre, by decade, or by country. Each of these similarity measures would offer different clusters and insights, so it’ll be up to you to define which one works best.
Clustering algorithms such as noise-based application density-based spatial clustering (DBSCAN), cluster hierarchical clustering, and medium-shift clustering, among others, are some of the options you can choose from. Several sectors and activities use them for things such as market segmentation, social network analysis, and medical imagery.
Regression is another method that’s part of supervised machine learning. With it, you use previous data to predict or explain a real or continuous value (such as prices or salaries). Its simplest form is linear regression which is usually more approximate than more complex forms like polynomial regression or neural networks).
Regression techniques begin with a hypothesis, which is a function based on input values and unknown parameters. When training an algorithm to tackle regression, you have to use a data set that allows the algorithm to refine its approach to the hidden parameters. After you refine the results, you can take the process to a real data set to apply your hypothesis.
An approach like this one is useful for things like estimating the value of a house. By combining different input values (such as square footage, age of the building, energy consumption, etc.), you could predict how much it could cost in the future, after renovations, or with any variation on those inputs whatsoever.
This is another method of supervised machine learning. You should use it to reduce the noise in your data sets, which can get so big that sometimes you might end up processing a lot of useless or redundant data. With dimensionality reduction, you get rid of some of the unwanted information by integrating similar data in larger groups that reduce the amount of detail.
Think of it like this. Imagine you have a market segmentation of a vast majority of 30-year-old women. You could reduce the size of your data set by ignoring the information coming from men from ages that are above or below 30. You’d be losing some data, sure, but the losses would be acceptable enough for the resulting insights.
There are several methods you could use to apply dimensional reduction, including popular ones like principal component analysis and t-stochastic incorporation of the neighbor (t-SNE). These approaches can be linear or non-linear and apply different logic to the reduction. So, you’d better consider the best one according to your data and personal needs.
This approach combines several supervised machine learning predictive models into one to refine the resulting predictions. It’s the whole “the strength of the wolf is the pack” kind of perspective that lies beneath the ensemble method approach.
Using different models can lead you to better results as they combine their strengths to reduce the weaknesses you’d find if you used them separately. Besides, the combination reduces the bias and variance of the learning model, which leads to fewer inaccuracies.
You should know that ensemble methods typically require more computation than a single model, so some people see them as a way to compensate for poor learning algorithms by way of computational processing. However, they excel in specific tasks such as face recognition, malware detection, and land mapping.
Don’t believe for a second that machine learning models end in these 5. There are other powerful models, including deep learning algorithms that are all the rage now. However, learning about the basics might open the door for you to understand the complex world of artificial intelligence in general.
Needless to say, you’ll need a lot of knowledge to create one of these algorithms on your own – let alone building an accurate one. So, in case you are in need of one for your business, you have 2 paths. Either outsource the development of your model or sit down and start learning.
The post 5 Machine Learning Models Every Data Scientist Should Know appeared first on The Crazy Programmer.

Python is arguably the programming language nowadays. We'll explore why that might be the case, what the current trends within the Python community are, and what packages and tools you might want to get acquainted with if you don't want to be left behind.
If you were pondering what programming language you should be investing time and effort in, you can stop searching now. It’s Python.
Alright, that was an oversimplification. Admittedly, you aren't going to jump into a Java project that's been in development for years just to port all that code into Python just because it's “hot”. Programming languages are a means to an end, and you have to carefully consider the cost/benefit of adopting a given technology.
That said, when things are massively moving in a certain direction, that has to mean something. And for some time already, things have been moving towards Python.
Want to level up your Python skills and stand out in a rapidly growing market? Check out SitePoint Premium! You'll find books to get you started (like The Python Apprentice) and develop job-ready skills (like Front-end Testing in Python). Enhance your skills with The Python Master, and access a growing library of over 400 books and courses on web design and development.
Practically every undergraduate IT class today is taught with Python — and not just computer science introduction courses offered by companies or by unversities. Even highly specialized courses on data science, AI, or quantitative finance — that not long ago would have used languages such as R, MATLAB, or C++ — are now also more often than not entirely taught in Python.
The post Trends in Python: What’s Hot in the Hottest Language Today appeared first on SitePoint.