Translate
Monday, 30 November 2020
Indian National Gets 20-Year Jail in United States for Running Scam Call Centers
4 Tips to Improve Your Application Security
The purpose of application security is simple – making apps secure to use. Different applications are created for various purposes
4 Tips to Improve Your Application Security on Latest Hacking News.
How To Deal With Insider Threat In The Age Of Covid-19?
Insider threats, considered too rare to be a real threat, have been steadily on the rise for a few years
How To Deal With Insider Threat In The Age Of Covid-19? on Latest Hacking News.
Quick Guide — How to Troubleshoot Active Directory Account Lockouts
Sunday, 29 November 2020
How to Protect Your Dispatch Software From Online Threats
Computer-aided dispatch systems (CAD) are most commonly used in law enforcement, emergency medical services, as well as for other public
How to Protect Your Dispatch Software From Online Threats on Latest Hacking News.
How to Download High Quality Music to Your PC
The days of CDs and tapes are long gone. We live in an age where one can find everything that
How to Download High Quality Music to Your PC on Latest Hacking News.
Gaming Tech 101: What Every Beginner Gamer Needs
Having the right gaming equipment can help to transform your gaming experience and allow you to achieve the best results.
Gaming Tech 101: What Every Beginner Gamer Needs on Latest Hacking News.
Advantech Suffered Conti Ransomware Attack – Hackers Demand 750 BTC Ransom
The IoT giant Advantech has become the latest victim of a severe cyber attack. Reportedly, Advantech has fallen prey to
Advantech Suffered Conti Ransomware Attack – Hackers Demand 750 BTC Ransom on Latest Hacking News.
DoppelPaymer Ransomware Hits Masterchef, Big Brother Producer
Another day, another ransomware attack has surfaced online. This time, it’s the French corporate giant Endemol Shine Group. Reportedly, the
DoppelPaymer Ransomware Hits Masterchef, Big Brother Producer on Latest Hacking News.
Critical Vulnerability In Basecamp Could Allow Remote Code Execution Attacks
Basecamp has recently disclosed a critical vulnerability that could allow remote code execution attacks. Fortunately, Basecamp has already deployed a
Critical Vulnerability In Basecamp Could Allow Remote Code Execution Attacks on Latest Hacking News.
Saturday, 28 November 2020
Drupal Release Emergency Fixes For Critical Code Execution Flaws
Drupal, the fourth popular most popular CMS behind the websites today, has released emergency fixes for some critical flaws. Exploiting
Drupal Release Emergency Fixes For Critical Code Execution Flaws on Latest Hacking News.
Week in security with Tony Anscombe
Is your smart doorbell putting you at risk of cyberattacks? – Spotify accounts hijacked en masse – Staying safe from SIM swapping
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
Europol and partners thwart massive credit card fraud scheme
The operation was carried out against fraudsters trying to monetize stolen credit card data on the internet’s seedy underbelly
The post Europol and partners thwart massive credit card fraud scheme appeared first on WeLiveSecurity
Friday, 27 November 2020
Xbox Subdomain Vulnerability Exposed Users’ Email Addresses
A researcher discovered a serious vulnerability in an Xbox subdomain that exposed email addresses behind Xbox accounts. It only required
Xbox Subdomain Vulnerability Exposed Users’ Email Addresses on Latest Hacking News.
Home Depot 2014 Data Breach Update: $17.5 Million Multistate Settlement Reached
Home Depot has recently agreed to a multistate settlement over a 2014 data breach. The Georgia-based firm suffered a major
Home Depot 2014 Data Breach Update: $17.5 Million Multistate Settlement Reached on Latest Hacking News.
Google Removed Two Baidu Android Apps Collecting Users’ Sensitive Data From Play Store – One Restored Recently
While the appearance of malicious apps on the Android Play Store is nothing new, seeing a dubious app from a
Google Removed Two Baidu Android Apps Collecting Users’ Sensitive Data From Play Store – One Restored Recently on Latest Hacking News.
5 Ways Big Companies Are Spying on You Online
Every email, photo, or post you send/publish, every webpage you visit, and every link you click, leave a trail. The
5 Ways Big Companies Are Spying on You Online on Latest Hacking News.
6 Aspects to Consider While Choosing a Substitute for Dark Sky API for Weather
Dark Sky was one of the most popular Application Programming Interface (API) related to weather services available on the play
6 Aspects to Consider While Choosing a Substitute for Dark Sky API for Weather on Latest Hacking News.
Why are self-driving cars not offered to us at level 5 by deep learning?
With the advancement of innovations in technology, the automotive industry has started to develop AI (Artificial intelligence) based vehicles. Have
Why are self-driving cars not offered to us at level 5 by deep learning? on Latest Hacking News.
5 Common Reasons Why People Downgrade Software
A software downgrade is a process of moving from a more recent software version to an older one. Not many
5 Common Reasons Why People Downgrade Software on Latest Hacking News.
Push Notification Marketing – How to Make Your Strategy Fly?
Looking for an extra marketing strategy that will let your business reach top high positions? Then it is time for
Push Notification Marketing – How to Make Your Strategy Fly? on Latest Hacking News.
6 Security Tips for Ecommerce Websites
Ecommerce has been on a steady growth for years now and there are currently between 12 and 24 million eCommerce
6 Security Tips for Ecommerce Websites on Latest Hacking News.
Vulnerability In cPanel Two-factor Authentication Could Allow Brute-force Attacks
Popular web hosting control platform cPanel had a major security bug. Specifically, the vulnerability affected the cPanel two-factor authentication feature
Vulnerability In cPanel Two-factor Authentication Could Allow Brute-force Attacks on Latest Hacking News.
FBI warns of threat actors spoofing Bureau domains, email accounts
The U.S. law enforcement agency shares a sampling of more than 90 spoofed FBI-related domains registered recently
The post FBI warns of threat actors spoofing Bureau domains, email accounts appeared first on WeLiveSecurity
SIM swap scam: What it is and how to protect yourself
Here’s what to know about attacks where a fraudster has your number, literally and otherwise
The post SIM swap scam: What it is and how to protect yourself appeared first on WeLiveSecurity
Digitally Signed Bandook Malware Once Again Targets Multiple Sectors
Wednesday, 25 November 2020
Become a White Hat Hacker — Get 10 Top-Rated Courses at 97% OFF
Interpol Arrests 3 Nigerian BEC Scammers For Targeting Over 500,000 Entities
Researcher Hacked Tesla Model X Demonstrating Keyless Entry System Vulnerability
A serious vulnerability existed in the Tesla Model X key fob that could allow anyone to break into the car.
Researcher Hacked Tesla Model X Demonstrating Keyless Entry System Vulnerability on Latest Hacking News.
GitHub Patched A Vulnerability Months After Google’s Report
Google spotted and reported a high-severity flaw affecting GitHub around three months ago. However, GitHub patched the vulnerability only recently.
GitHub Patched A Vulnerability Months After Google’s Report on Latest Hacking News.
Up to 350,000 Spotify accounts hacked in credential stuffing attacks
This won't be music to your ears – researchers spot an unsecured database replete with records used for an account hijacking spree
The post Up to 350,000 Spotify accounts hacked in credential stuffing attacks appeared first on WeLiveSecurity
Tuesday, 24 November 2020
2-Factor Authentication Bypass Flaw Reported in cPanel and WHM Software
Baidu's Android Apps Caught Collecting and Leaking Sensitive User Data
Stantinko Botnet Now Targeting Linux Servers to Hide Behind Proxies
Bug in Twitter Fleets Where Posts Remain Visible
Twitter has recently launched the “Fleets” feature similar to WhatsApp status or Facebook stories. However, it may not work the
Bug in Twitter Fleets Where Posts Remain Visible on Latest Hacking News.
High-Severity XSS Flaw In TikTok Could Allow Account Takeover
TikTok has recently addressed a serious security vulnerability in its platform. Specifically, a cross site scripting flaw (XSS) affected the
High-Severity XSS Flaw In TikTok Could Allow Account Takeover on Latest Hacking News.
Security flaws in smart doorbells may open the door to hackers
The peace of mind that comes with connected home security gadgets may be false – your smart doorbell may make an inviting target for unwanted visitors
The post Security flaws in smart doorbells may open the door to hackers appeared first on WeLiveSecurity
Monday, 23 November 2020
Critical Unpatched VMware Flaw Affects Multiple Corporates Products
LidarPhone Attack Transforms Smart Vacuum Cleaners Into Spying Tools
Another study has suggested how unsmart it would be to use smart devices without adequate cybersecurity measures. Researchers have devised
LidarPhone Attack Transforms Smart Vacuum Cleaners Into Spying Tools on Latest Hacking News.
Google To Add End-to-End Encryption To Android Messages App
As more instant messaging apps surface online with end-to-end encryption, Google has also realized its importance. Hence, Google is planning
Google To Add End-to-End Encryption To Android Messages App on Latest Hacking News.
How to Sign a PDF Online?
Electronic signatures make it simpler for members of record administration, workers of human resources, and executives in a number of
How to Sign a PDF Online? on Latest Hacking News.
Football Club Manchester United Confirms Cyber Attack
Amidst all the businesses suffering cybersecurity incidents, a football club has now joined the trail. Reportedly, Manchester United has disclosed
Football Club Manchester United Confirms Cyber Attack on Latest Hacking News.
Facebook Messenger Bug Could Allow Spying On Users Via Audio
Facebook has recently fixed a serious bug in their Messenger app that could allow spying on other users. Specifically, exploiting
Facebook Messenger Bug Could Allow Spying On Users Via Audio on Latest Hacking News.
Imminent Threat for US Hospitals and Clinics, RYUK Ransomware Alert (AA20-302A)
By Brian Tant On October 29, 2020 a confidential source said that an RYUK attack against US-based hospitals and clinics
Imminent Threat for US Hospitals and Clinics, RYUK Ransomware Alert (AA20-302A) on Latest Hacking News.
A Step-by-Step Guide to Help You Manage Your Employees
Running a company or an organization is not easy. That is why getting any tool that can ease your job
A Step-by-Step Guide to Help You Manage Your Employees on Latest Hacking News.
How Can Someone Can Hack Your Phone Without Touching It?
Is it really possible? Can someone hack my phone without touching it? Yes, a hacker can spy on a phone
How Can Someone Can Hack Your Phone Without Touching It? on Latest Hacking News.
Make the Most of Social Gaming in This Pandemic with Trivia Board Games
The COVID19 pandemic has driven us indoors and is forcing us to stay within the confines of our homes. Hanging
Make the Most of Social Gaming in This Pandemic with Trivia Board Games on Latest Hacking News.
7 Ways to Improve Your Web Application Security Against Cybercrime in 2020
Security is one of the crucial elements of web application development. However, businesses often do not pay as much attention
7 Ways to Improve Your Web Application Security Against Cybercrime in 2020 on Latest Hacking News.
Windows 10X – What Should You Know About It?
Microsoft is the leading name in the PC game. When it comes to tabs and detachables, however, they don’t match
Windows 10X – What Should You Know About It? on Latest Hacking News.
Why Data Recovery Services Are Still In Demand Nowadays
Data recovery has a long history with computers, ever since the invention of mechanical computers. Even though data recovery companies
Why Data Recovery Services Are Still In Demand Nowadays on Latest Hacking News.
The Link Between Text Messaging and Effective Hacking
The name might be cute but don’t let it fool you. Smishing is a hacking attack that has mastered the
The Link Between Text Messaging and Effective Hacking on Latest Hacking News.
Android App GO SMS Pro Exposed Users’ Private Messages Publicly
One more Android app risked the security and privacy of users. This time, it the GO SMS Pro, a messaging
Android App GO SMS Pro Exposed Users’ Private Messages Publicly on Latest Hacking News.
VoltPillager Attack Can Manipulate Intel CPUs’ Secure SGX Enclaves
Recently, researchers presented their study about the PLATYPUS attack that could steal data from the Intel CPUs. Now, another team
VoltPillager Attack Can Manipulate Intel CPUs’ Secure SGX Enclaves on Latest Hacking News.
Cisco Webex Vulnerabilities Could Expose Meetings To Ghost Users
Cisco has recently addressed serious vulnerabilities affecting its Webex video conferencing app. Exploiting the bugs could allow unsolicited users to
Cisco Webex Vulnerabilities Could Expose Meetings To Ghost Users on Latest Hacking News.
Why Replace Traditional Web Application Firewall (WAF) With New Age WAF?
Saturday, 21 November 2020
Liquid Cryptocurrency Exchange Suffered A Security Breach
Another day, another cryptocurrency cyber-attack has surfaced online. This time, the Liquid cryptocurrency exchange has fallen prey to a security
Liquid Cryptocurrency Exchange Suffered A Security Breach on Latest Hacking News.
Capcom Ransomware Attack Update: Vendors Confirmed Compromise Of Data
Earlier this month, the Japanese gaming firm Capcom suffered a cybersecurity incident reports hinted towards a ransomware attack. After two
Capcom Ransomware Attack Update: Vendors Confirmed Compromise Of Data on Latest Hacking News.
Week in security with Tony Anscombe
Lazarus takes aim at South Korea via an unusual supply-chain attack – The harsh reality of poor passwords – Bumble bitten by bugs
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
5 takeaways from the 2020 (ISC)2 Cybersecurity Workforce Study
From the impact of the pandemic on cybersecurity careers to workers’ job satisfaction, the report offers a number of interesting findings
The post 5 takeaways from the 2020 (ISC)<sup>2</sup> Cybersecurity Workforce Study appeared first on WeLiveSecurity
Friday, 20 November 2020
Web Hosting Provider Managed.com Suffered REvil Ransomware Attack
As ransomware attacks are on a rise, we see a continuous increase in the victim list. The recent ransomware attack
Web Hosting Provider Managed.com Suffered REvil Ransomware Attack on Latest Hacking News.
New Jupyter Malware Is A Blend of Infostealer And Backdoor
As new threats keep emerging, researchers have found new malware in the wild. Identified as Jupyter, the malware isn’t only
New Jupyter Malware Is A Blend of Infostealer And Backdoor on Latest Hacking News.
10 Cross Platforms for App Development
Time is money. Developers value their time, so they tend to seek the quickest and the most reliable way of
10 Cross Platforms for App Development on Latest Hacking News.
The worst passwords of 2020: Is it time to change yours?
They’re supremely easy to remember, as well as easy to crack. Here’s how to improve your password security.
The post The worst passwords of 2020: Is it time to change yours? appeared first on WeLiveSecurity
Facebook Messenger Bug Lets Hackers Listen to You Before You Pick Up the Call
Thursday, 19 November 2020
WARNING: Unpatched Bug in GO SMS Pro App Exposes Millions of Media Messages
Google Released Chrome 87 With Performance Updates; Disables FTP
After back-to-back security patches, Google has now released Chrome 87. While this browser also includes bug fixes, it introduces some
Google Released Chrome 87 With Performance Updates; Disables FTP on Latest Hacking News.
Evolution of Emotet: From Banking Trojan to Malware Distributor
Bumble bugs could have exposed personal data of all users
The information at risk of theft due to API flaws included people’s pictures, locations, dating preferences and Facebook data
The post Bumble bugs could have exposed personal data of all users appeared first on WeLiveSecurity
Researchers Warn of Critical Flaws Affecting Industrial Automation Systems
Wednesday, 18 November 2020
Mozilla Has Released Firefox 83 With FreeType Zero-day Fix and HTTPS-Only
Mozilla has rolled out the latest version of their popular web browser Firefox. Marked Firefox 83, the browser comes with
Mozilla Has Released Firefox 83 With FreeType Zero-day Fix and HTTPS-Only on Latest Hacking News.
Brosix – Keep Your Employees Connected With This Secure Messaging App
Today, the market is full of various instant messaging apps for personal communications. However, finding a good chat platform for
Brosix – Keep Your Employees Connected With This Secure Messaging App on Latest Hacking News.
Use This Ultimate Template to Plan and Monitor Your Cybersecurity Budgets
Apple Lets Some of its Big Sur macOS Apps Bypass Firewall and VPNs
Tuesday, 17 November 2020
A Look into the TLDs of the Most Abused Newly Registered Domains
While the generic top-level domain (gTLD) that a company uses is not a telltale sign of maliciousness, some TLDs are
A Look into the TLDs of the Most Abused Newly Registered Domains on Latest Hacking News.
How To Keep Your Cryptocurrency Safe And Secure
Everybody’s heard how the blockchain is far more secure than the cloud. And it is. But, people end up with
How To Keep Your Cryptocurrency Safe And Secure on Latest Hacking News.
Top 10 Internet Safety Rules to Live By
The Best Ways to Stay Safe While Browsing Online Fraudsters are indiscriminate in whom they target: everyone is fair game.
Top 10 Internet Safety Rules to Live By on Latest Hacking News.
TicketMaster Slapped With $1.65 Million Fine Over 2018 Data Breach
The event giant Ticketmaster is now facing the aftermath of a cybersecurity incident that happened two years ago. The UK
TicketMaster Slapped With $1.65 Million Fine Over 2018 Data Breach on Latest Hacking News.
Lazarus supply‑chain attack in South Korea
ESET researchers uncover a novel Lazarus supply-chain attack leveraging WIZVERA VeraPort software
The post Lazarus supply‑chain attack in South Korea appeared first on WeLiveSecurity
Chinese APT Hackers Target Southeast Asian Government Institutions
Monday, 16 November 2020
Researcher Discloses Critical RCE Flaws In Cisco Security Manager
ShinyHunters Target Numerous Firms In A Recent Wave Of Data Breaches
A new wave of data breaches emerges as reports about millions of data being stolen from different firms surface online.
ShinyHunters Target Numerous Firms In A Recent Wave Of Data Breaches on Latest Hacking News.
Tackling Data Regulations As A Business for Employees
When the General Data Protection Regulation (GDPR) took effect in May 2018, it emphasized the importance of data security. The
Tackling Data Regulations As A Business for Employees on Latest Hacking News.
Bitcoin Exchanger – Overview, Importance, and More!
Many people are engaged in using bitcoin as it allows them to trade across the borders and also helps them
Bitcoin Exchanger – Overview, Importance, and More! on Latest Hacking News.
Trojanized Security Software Hits South Korea Users in Supply-Chain Attack
Saturday, 14 November 2020
Akropolis Cryptocurrency Lending Service Lost $2 Million to Hackers In A Cyber Attack
Despite being around for years, securing cryptocurrency assets continues to be a challenge. Hence, joining the list of cryptocurrency attack
Akropolis Cryptocurrency Lending Service Lost $2 Million to Hackers In A Cyber Attack on Latest Hacking News.
Week in security with Tony Anscombe
ESET research uncovers a backdoor targeting POS systems – Why you shouldn't share your Netflix password – Data of millions of hotel guests exposed
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
Cybersecurity careers: Which one is right for you?
Looking for vulnerabilities, securing systems or dismantling them, these are all viable career paths in the cybersecurity industry. Could one of them be right for you?
The post Cybersecurity careers: Which one is right for you? appeared first on WeLiveSecurity
Friday, 13 November 2020
PLATYPUS Attack: Novel Power Side-channel Attack Threatening Intel Devices
Intel CPUs running on various devices can leak data with power consumption fluctuations. Researchers have devised the PLATYPUS attack that
PLATYPUS Attack: Novel Power Side-channel Attack Threatening Intel Devices on Latest Hacking News.
Google Address Two More Chrome Zero-Day Vulnerabilities
Continuing the trail of urgent fixes, Google has now disclosed two more zero-day vulnerabilities in Chrome. Since the patches are
Google Address Two More Chrome Zero-Day Vulnerabilities on Latest Hacking News.
Google patches two new zero‑day flaws in Chrome
The last three weeks have seen a bumper crop of patches for zero-day bugs across software from Google, Apple and Microsoft
The post Google patches two new zero‑day flaws in Chrome appeared first on WeLiveSecurity
Hungry for data, ModPipe backdoor hits POS software used in hospitality sector
Backdoor authors show deep knowledge of the targeted POS software, decrypting database passwords from Windows registry values
The post Hungry for data, ModPipe backdoor hits POS software used in hospitality sector appeared first on WeLiveSecurity
Live Webinar: Reducing Complexity by Increasing Consolidation for SMEs
Thursday, 12 November 2020
SAD DNS — New Flaws Re-Enable DNS Cache Poisoning Attacks
Create React App: Get React Projects Ready Fast

Starting a new React project isn’t that simple. Instead of diving straight into code and bringing your application to life, you have to spend time configuring the right build tools to set up a local development environment, unit testing, and a production build. Luckily, help is at hand in the form of Create React App.
Create-React-App is a command-line tool from Facebook that allows you to generate a new React project and use a pre-configured webpack build for development. It has long since become an integral part of the React ecosystem that removes the need to maintain complex build pipelines in your project, letting you focus on the application itself.
How Does Create React App Work?
Create React App is a standalone tool that can be run using either npm or Yarn.
You can generate and run a new project using npm just with a couple of commands:
npx create-react-app new-app
cd new-app
npm start
If you prefer Yarn, you can do it like this:
yarn create react-app new-app
cd new app
yarn start
Create React App will set up the following project structure:
new-app
├── .gitignore
├── node_modules
├── package.json
├── public
│ ├── favicon.ico
│ ├── index.html
│ ├── logo192.png
│ ├── logo512.png
│ ├── manifest.json
│ └── robots.txt
├── README.md
├── src
│ ├── App.css
│ ├── App.js
│ ├── App.test.js
│ ├── index.css
│ ├── index.js
│ ├── logo.svg
│ ├── reportWebVitals.js
│ └── setupTests.js
└── yarn.lock
It will also add a react-scripts package to your project that will contain all of the configuration and build scripts. In other words, your project depends on react-scripts, not on create-react-app itself. Once the installation is complete, you can fire up the dev server and start working on your project.
Basic Features
Local Development Server
The first thing you’ll need is a local development environment. Running npm start will fire up a webpack development server with a watcher that will automatically reload the application once you change something. Starting from v4, Create React App supports React’s fast refresh as an alternative to Hot Module Replacement. Like its predecessor, this allows us to quickly refresh parts of the application after making changes in the codebase, but has some new features as well. Fast Reload will try to reload only the modified part of the application, preserve the state of functional components and hooks, and automatically reload the application after correcting a syntax error.
You can also serve your application over HTTPS, by setting the HTTPS variable to true before running the server.
The application will be generated with many features built in.
ES6 and ES7
The application comes with its own Babel preset — babel-preset-react-app — to support a set of ES6 and ES7 features. Some of the supported features are:
- Async/await
- Object Rest/Spread Properties
- Dynamic import()
- Class Fields and Static Properties
Note that Create React App does not provide any polyfills for runtime features, so if you need any of these, you need to include them yourself.
Asset Import
You can import CSS files, images, or fonts from your JavaScript modules that allow you to bundle files used in your application. Once the application is built, Create React App will copy these files into the build folder. Here’s an example of importing an image:
import image from './image.png';
console.log(image); // image will contain the public URL of the image
You can also use this feature in CSS:
.image {
background-image: url(./image.png);
}
Styling
As mentioned in the previous section, Create React App allows you to add styles by just importing the required CSS files. When building the application, all of the CSS files will be concatenated into a single bundle and added to the build folder.
Create React App also supports CSS modules. By convention, files named as *.module.css are treated as CSS modules. This technique allows us to avoid conflicts of CSS selectors, since Create React App will create unique class selectors in the resulting CSS files.
Alternatively, if you prefer to use CSS preprocessors, you can import Sass .scss files. However, you’ll need to install the node-sass package separately.
Additionally, Create React App provides a way to add CSS Resets by adding @import-normalize; anywhere in your CSS files. Styles also undergo post-processing, which minifies them, adds vendor prefixes using Autoprefixer, and polyfills unsupported features, such as the all property, custom properties, and media query ranges.
Running Unit Tests
Executing npm test will run tests using Jest and start a watcher to re-run them whenever you change something:
PASS src/App.test.js
✓ renders learn react link (19 ms)
Test Suites: 1 passed, 1 total
Tests: 1 passed, 1 total
Snapshots: 0 total
Time: 0.995 s
Ran all test suites.
Watch Usage
› Press f to run only failed tests.
› Press o to only run tests related to changed files.
› Press q to quit watch mode.
› Press p to filter by a filename regex pattern.
› Press t to filter by a test name regex pattern.
› Press Enter to trigger a test run.
Jest is a test runner also developed by Facebook as an alternative to Mocha or Karma. It runs the tests in a Node environment instead of a real browser, but provides some of the browser-specific globals using jsdom.
Jest also comes integrated with your version control system and by default will only run tests on files changed since your last commit. For more on this, refer to “How to Test React Components Using Jest”.
ESLint
During development, your code will also be run through ESLint, a static code analyzer that will help you spot errors during development.
Continue reading Create React App: Get React Projects Ready Fast on SitePoint.
Microsoft November Patch Tuesday Comes With Much-Awaited Zero-Day Fix
Microsoft’s monthly scheduled updates are out for this month. The November Patch Tuesday is specifically important since Microsoft has fixed
Microsoft November Patch Tuesday Comes With Much-Awaited Zero-Day Fix on Latest Hacking News.
Uncovered: APT 'Hackers For Hire' Target Financial, Entertainment Firms
New ModPipe Point of Sale (POS) Malware Targeting Restaurants, Hotels
MISSIONS — The Next Level of Interactive Developer Security Training
Microsoft Patch Tuesday fixes 17 critical flaws, Windows zero‑day
The second Tuesday of the month brings another fresh batch of fixes for security vulnerabilities in various Microsoft products
The post Microsoft Patch Tuesday fixes 17 critical flaws, Windows zero‑day appeared first on WeLiveSecurity
Why you should keep your Netflix password to yourself
Sharing is caring – except when it isn’t. Here’s why you shouldn’t share your password for online media services with other people.
The post Why you should keep your Netflix password to yourself appeared first on WeLiveSecurity
Wednesday, 11 November 2020
Two New Chrome 0-Days Under Active Attacks – Update Your Browser
Black Friday vs Cyber Monday: Best Time to Buy a VPN Service
The time everyone has been waiting for is fast approaching, and the best deals are already knocking your front door,
Black Friday vs Cyber Monday: Best Time to Buy a VPN Service on Latest Hacking News.
How Does Military Communicate on a Battlefield Today
Whether we realize it or not, communication has always played a pivotal role in our everyday life – but in
How Does Military Communicate on a Battlefield Today on Latest Hacking News.
Common Ways to Avoid Hacking Your Personal Data on the Internet
When it comes to the avoidance of giving out all of your personal data online unknowingly, then there are steps
Common Ways to Avoid Hacking Your Personal Data on the Internet on Latest Hacking News.
Over 2800 e-Shops Running Outdated Magento Software Hit by Credit Card Hackers
Build Your 2021 Cybersecurity Plan With This Free PPT Template
Microsoft Releases Windows Security Updates For Critical Flaws
Data on millions of hotel guests exposed in cloud storage leak
The cache of data sitting wide open on a server included full names, national ID numbers and credit card data
The post Data on millions of hotel guests exposed in cloud storage leak appeared first on WeLiveSecurity
Tuesday, 10 November 2020
New Pay2Key Ransomware Emerges As The Latest Threat For Organizations
A new ransomware threat is around to disrupt the business sector. Identified as Pay2Key ransomware, the malware has already targeted
New Pay2Key Ransomware Emerges As The Latest Threat For Organizations on Latest Hacking News.
Welcart e-Commerce Plugin Bug Exposed WordPress Sites To Code Injection Attacks
A major and widely popular WordPress plugin potentially exposed sites to cyber attacks. Specifically, the vulnerability existed in the Welcart
Welcart e-Commerce Plugin Bug Exposed WordPress Sites To Code Injection Attacks on Latest Hacking News.
Brazil Court System Went Down Following Cyber Attack
After targeting various sectors, ransomware gangs have now turned to the court systems. Recently, Brazil Superior Court of Justice systems
Brazil Court System Went Down Following Cyber Attack on Latest Hacking News.
Monday, 9 November 2020
Watch Out! New Android Banking Trojan Steals From 112 Financial Apps
Getting Started with React Native

With the ever-increasing popularity of smartphones, developers are looking into solutions for building mobile applications. For developers with a web background, frameworks such as Cordova and Ionic, React Native, NativeScript, and Flutter allow us to create mobile apps with languages we’re already familiar with: HTML, XML, CSS, and JavaScript.
In this guide, we’ll take a closer look at React Native. You’ll learn the absolute basics of getting started with it. Specifically, we’ll cover the following:
- what React Native is
- what Expo is
- how to set up an React Native development environment using Expo
- how to create an app with React Native
Prerequisites
This tutorial assumes that you’re coming from a web development background. The minimum requirement for you to be able to confidently follow this tutorial is to know HTML, CSS, and JavaScript. You should also know how to install software on your operating system and work with the command line. We’ll also be using some ES6 syntax, so it would help if you know basic ES6 syntax as well. Knowledge of React is helpful but not required.
What is React Native?
React Native is a framework for building apps that work on both Android and iOS. It allows you to create real native apps using JavaScript and React. This differs from frameworks like Cordova, where you use HTML to build the UI, which will then just be displayed within the device’s integrated mobile browser (WebView). React Native has built-in components which are compiled to native UI components, while your JavaScript code is executed through a virtual machine. This makes React Native more performant than Cordova.
Another advantage of React Native is its ability to access native device features. There are many plugins which you can use to access native device features, such as the camera and various device sensors. If you’re in need of a platform-specific feature that hasn’t been implemented yet, you can also build your own native modules — although that will require you to have considerable knowledge of the native platform you want to support (Java or Kotlin for Android, and Objective C or Swift for iOS).
If you’re coming here and you’re new to React, you might be wondering what it is. React is a JavaScript library for the Web for building user interfaces. If you’re familiar with MVC, it’s basically the View in MVC. React’s main purpose is to allow developers to build reusable UI components. Examples of these components include buttons, sliders, and cards. React Native took the idea of building reusable UI components and brought it into mobile app development.
What is Expo?
Before coming here, you might have heard of Expo. It’s even mentioned in the official React Native docs, so you might be wondering what it is.
In simple terms, Expo allows you to build React Native apps without the initial headache that comes with setting up your development environment. It only requires you to have Node installed on your machine, and the Expo client app on your device or emulator.
But that’s just how Expo is initially sold. In reality, it’s much more than that. Expo is actually a platform that gives you access to tools, libraries and services for building Android and iOS apps faster with React Native. Expo comes with an SDK which includes most of the APIs you can ask for in a mobile app development platform:
Those are just few of the APIs you get access to out of the box if you start building React Native apps with Expo. Of course, these APIs are available to you as well via native modules if you develop your app using the standard React Native setup.
Plain React Native or Expo?
The real question is which one to pick — plain React Native or Expo? There’s really no right or wrong answer. It all depends on the context and what your needs are. But I guess it’s safe to assume that you’re reading this tutorial because you want to quickly get started with React Native. So I’ll go ahead and recommend that you start out with Expo. It’s fast, simple, and easy to set up. You can dive right into tinkering with React Native code and get a feel of what it has to offer in just a couple of hours.
But as you begin to grasp the different concepts, and as the need for different native features arises, you might find that Expo is kind of limiting. Yes, it has a lot of native features available, but not all the native modules that are available to standard React Native projects are supported.
Note: projects like unimodules are beginning to close the gap between standard React Native projects and Expo projects, as it allows developers to create native modules that work for both React Native and ExpoKit.
Setting Up the React Native Development Environment
To quickly get started with React Native, the recommended method is to set up Expo.
The only prerequisite of setting up Expo is that you need to have Node.js installed in your machine. To do this, you can either head to the official Node download page and grab the relevant binaries for your system, or you can use a version manager, which allows you to install multiple versions of Node and switch between them at will.
Once you have Node.js installed, install the Expo CLI. This is used for creating, serving, packaging, and publishing projects:
npm install -g expo-cli
Next, install Yarn, the preferred package manager for Expo:
npm install -g yarn
That’s really all there is to it! The next step is to download the Expo client App for Android or iOS. Note that this is the only way you can run Expo apps while you’re still in development. When you’re ready to ship the app, you can follow this guide to create standalone binaries for iOS and Android which can be submitted to the Apple App Store and Google Play Store.
What We’ll Be Building
Now that your development environment is set up, we can look at the app we’re going to create — a Pokémon search app. It will allow the user to type the name of a Pokémon into an input box, before fetching the Pokémon’s details from an external API and displaying them to the user.
Here’s what the finished thing will look like:
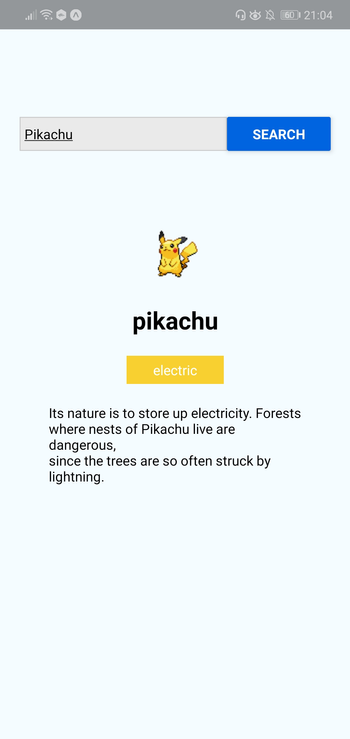
As ever, you can find the source code for this in our GitHub repo.
Bootstrapping the App
On your terminal, execute the following command to create a new React Native project using Expo:
expo init RNPokeSearch
Under Managed Workflow, select blank. By default, this will install the dependencies using Yarn.
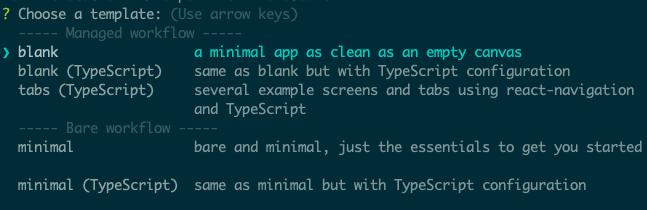
You might be asking what this Managed workflow and Bare workflow is. These are the two types of workflows that Expo supports. With a managed workflow, you only have to deal with JavaScript and Expo manages everything for you. While in Bare workflow, you have full control over the native code. It gives you the same freedom as the React Native CLI, but with the added bonus of Expo’s libraries and services. You can visit this managed vs bare intro page if you want to learn more about workflows in Expo.
Just like in a web environment, you can install libraries to easily implement different kinds of functionality in React Native. Once the project is created, we need to install a couple of dependencies: pokemon and axios. The former is used for verifying if the text entered in the search box is a real Pokémon name, while axios is used to make an HTTP request to the API that we’re using, namely the PokeAPI:
yarn add pokemon axios
React Native Project Directory Structure
Before we proceed to coding, let’s first take a look at the directory structure of a React Native project created with Expo:
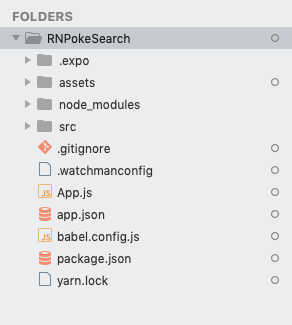
Here’s a breakdown of the most important files and folders that you need to remember:
App.js: the main project file. This is where you’ll start developing your app. Any changes you make to this file will be reflected on the screen.src: acts as the main folder which stores all the source code related to the app itself. Note that this isn’t included in the default project created by Expo CLI. The name of this folder can be anything. Some people useappas well.assets: this is where the app assets such as icons and splash screens are stored.package.json: where the name and versions of the libraries you installed for this project are added.node_modules: where the libraries you installed are stored. Note that this already contains a lot of folders before you installed the two libraries earlier. This is because React Native also has its own dependencies. The same is true for all the other libraries you install.
Don’t mind the rest of the folders and files for now, as we won’t be needing them when just getting started.
Running the App
At this point, you can now run the app by executing the command below. Make sure that you’ve already installed the corresponding Expo client (Android or iOS) for your phone and that it’s connected to the same network as your computer before doing so. If you don’t have an Android or iOS device you can test with, you can use the Android Studio Emulator or the iOS simulator so you can run the app on your machine:
yarn start
Once it’s running, it will display a QR code:
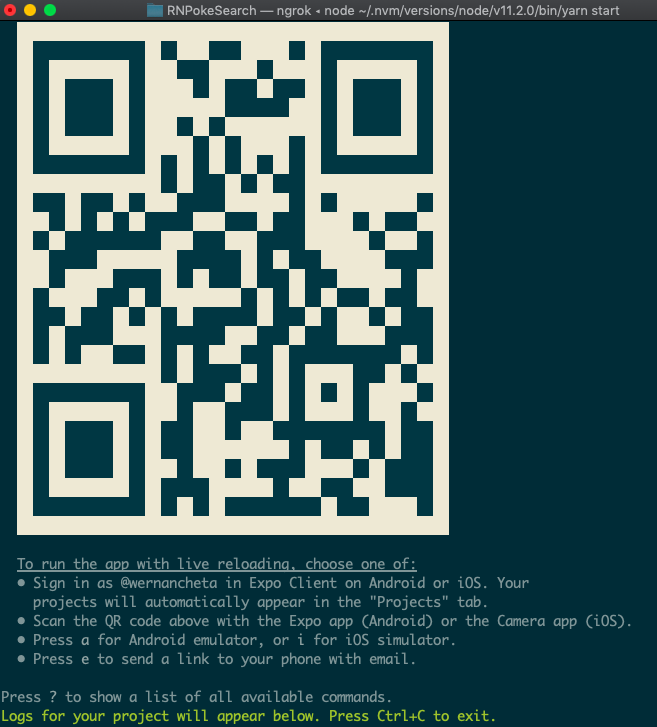
Open your Expo client app, and in the projects tab click on Scan QR Code. This will open the app on your Android or iOS device. If you have an emulator running, you can either press i to run it on the iOS simulator or a to run it on the Android emulator.
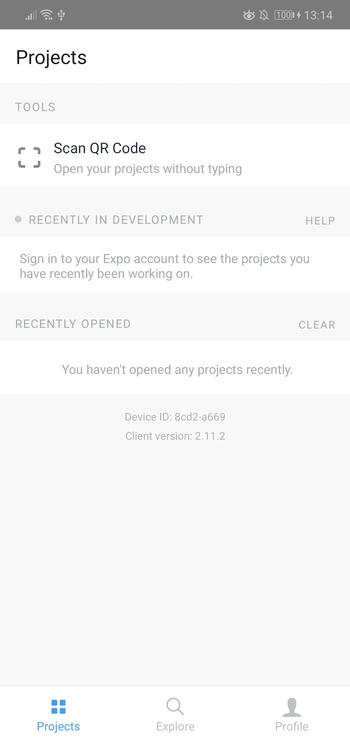
If you’re testing on a real device, shake it so the developer menu will show up.
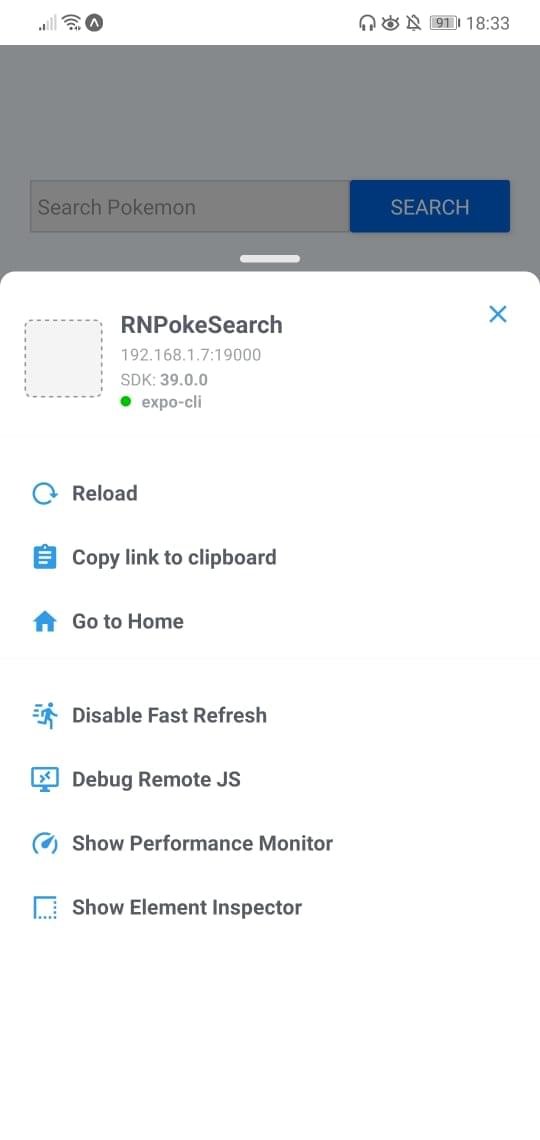
Make sure that Fast Refresh is enabled. This allows you to automatically reload the changes that you make on your components.
Continue reading Getting Started with React Native on SitePoint.