Microsoft alerted all its users to stay vigilant with regard to PonyFinal ransomware attacks. Since the ransomware attacks are active
Microsoft Warns Of PonyFinal Ransomware Attacks Active In The Wild on Latest Hacking News.
Microsoft alerted all its users to stay vigilant with regard to PonyFinal ransomware attacks. Since the ransomware attacks are active
Microsoft Warns Of PonyFinal Ransomware Attacks Active In The Wild on Latest Hacking News.
While many people love to use video editing apps, little do they realize that not all of these apps are
VivaVideo And Other Apps With Over 157 Million Installs Spy On Users on Latest Hacking News.
Last year, Android devices suffered cyber attacks after attackers exploited the StrandHogg vulnerability to steal banking data. Now, after a
StrandHogg 2.0 Vulnerability Targets Android Devices To Steal Data on Latest Hacking News.
Heads up Apple users! A researcher found a vulnerability that allowed for an attacker to hack accounts simply via email.
Researcher Discovers Critical Vulnerability and Was Awarded $100,000 on Latest Hacking News.
Hello friends, In my last post I’ve discussed the common problem Python Programmers face i.e. unexpected EOF while parsing and in today’s post, I’ll be discussing EOL while scanning string literal.
But do you exactly know what is this error all about and how we can remove it from our python code?
So, what exactly an EOL is?
EOL stands for End Of Line. This means we have now come to the end of our line and the error related to this is shown below with example code.
def printName():
return "This is a test basestring
printName()
Now, after running this piece of code, I get an error something similar to this.
File "main.py", line 2 return "This is a test basestring SyntaxError: EOL while scanning string literal ...Program finished with exit code 1 Press ENTER to exit the console
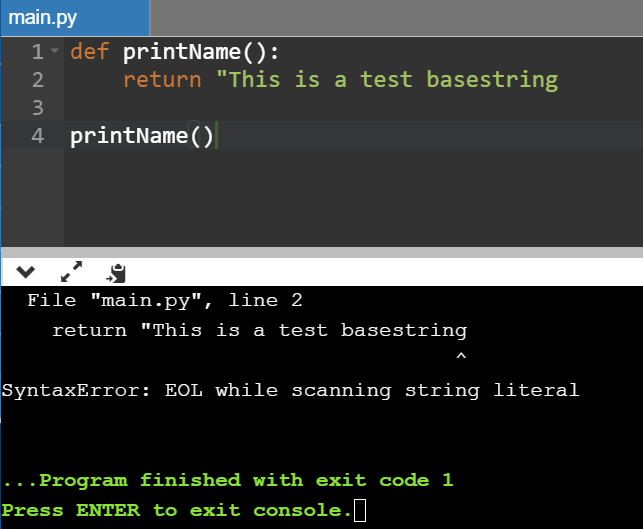
Now the above code contains one error and the error is that the return in the printName( ) function in the above code is not closed properly. We can see that it doesn’t have the closing quote ".
Now, when we tried to run this code, it showed us SyntaxError: EOL while scanning string literal.
Now the problem is our return keyword has some syntax error. This lead to the SyntaxError: EOL while scanning string literal. To overcome this type of error in our python file, we need to ensure that we have not left any part of our string unclosed or not in proper syntax. I hope this is clear to you.
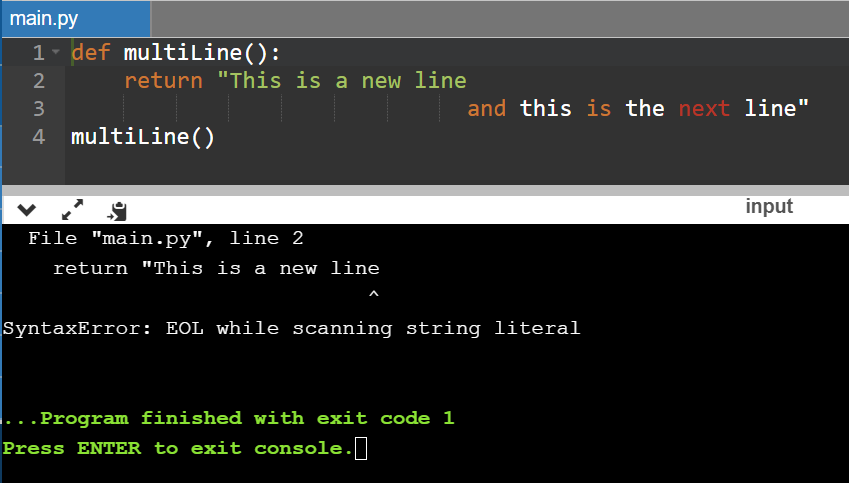
Sometimes we try to print our string to multiple lines also and in that case what happens is that, let’s see this with an example:
def multiLine():
return "This is a new line
and this is the next line"
multiLine()
Now, when we will try to run this code, it will give us the same error which we got above,
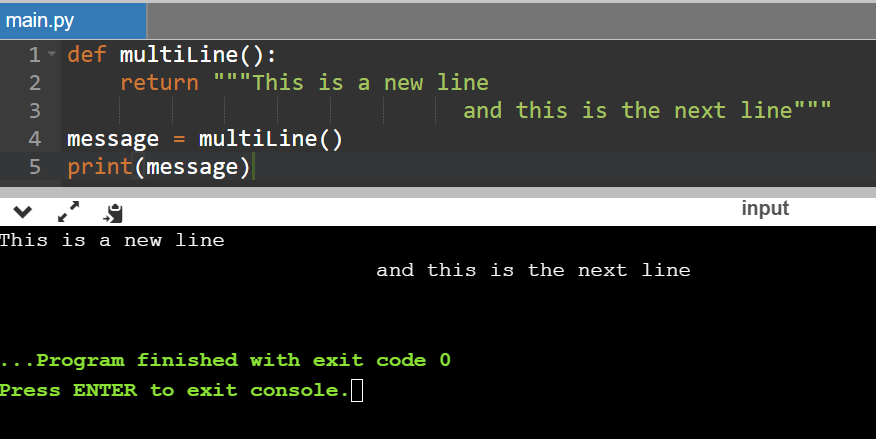
To overcome this type of error while using the string spreading into multiple line, we can use the ''' or """. We can wrap our code into the triple quote. Both quotes single and double quote will work fine.
Here you can see that our code is working fine and we are good to go.
Well, this was all about the EOL and the error related to it. If you stuck into any kind of error, don’t forget to google it and try to debug it on your own. This will teach you how to debug on your own as someone might have faced a similar problem earlier.
If you still don’t find any solution for your problem, you can ask your doubt in the comment’s section below and we’ll get back to you .
.
Thanks for your visit and if you are new here, consider subscribing to our newsletter. See you in my next post. Bye!
The post Solve SyntaxError: EOL while scanning string literal in Python appeared first on The Crazy Programmer.
New ESET research into Turla's malicious toolkit – GDPR turns two – Critical flaw in Android devices
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
And most people don’t change their password even after hearing about a breach, a survey finds
The post People know reusing passwords is risky – then do it anyway appeared first on WeLiveSecurity
Left unpatched, the vulnerability could expose almost all Android users to the risk of having their personal data intercepted by attackers
The post Critical Android flaw lets attackers hijack almost any app, steal data appeared first on WeLiveSecurity

Working remotely is on the rise, and will continue to do so long after COVID-19 runs its course. If you’re thinking about ditching the office but aren’t sure how, learning one (or more!) of the following skillsets will increase your chances of landing a remote job.
Software development is the most in-demand remote job in the world. And with a median salary of $66,000/year, you can probably afford a decent home office setup in which to operate.
Software development might be the job for you if you like solving problems, building things, and continuous learning. Even the best developers have to jump on GitHub or Stack Overflow from time to time to crowdsource a solution. In fact, development practically necessitates collaboration, making the development community extremely tight and incredibly helpful.
So what skills does a remote software developer need in 2020? Well, a lot of them. Google “software development skills” and you’ll find list upon list of subjects like programming languages, algorithms, databases, and encryption. But good news (and, as you’ll find, a running theme in this article): you don’t have to learn everything.
Instead, choose a software development concentration. For example, going from software development to Java development immediately cuts your required skill set in half. And you don’t have to stop there. Refining your concentration to mobile Java development, or even mobile game Java development, turns a near Herculean task into something much more reasonable.
Digital marketing is another wildly in-demand skill set. Digital marketers are responsible for services like social media campaign planning, content coordination, SEO, and PPC ads. Remote digital marketing jobs average a median salary of $50,500/year, and nearly every industry is hiring.
Continue reading 4 Most High-Demand Skillsets for Remote Jobs on SitePoint.
Samsung has announced a new step toward ensuring secure devices. Reportedly, Samsung has developed a new SE chip security solution
Samsung Introduces New SE Chip With 6+ Certification Secure Device on Latest Hacking News.
A hack-and-extort campaign takes aim at poorly secured databases replete with customer information that can be exploited for further attacks
The post Crooks threaten to leak customer data stolen from e‑commerce sites appeared first on WeLiveSecurity
Turla has updated its ComRAT backdoor and now uses the Gmail web interface for Command and Control
The post From Agent.BTZ to ComRAT v4: A ten‑year journey appeared first on WeLiveSecurity
While the tech giants were busy managing vulnerabilities in Bluetooth and WiFi chips, researchers have found another serious issue. Reportedly,
Spectra Attack Target Separation Between Wireless Communication Chips For Coordinated Attacks on Latest Hacking News.
Nowadays, more and more people are becoming increasingly familiar with the importance of online privacy. As a result, more people
NordVPN Just Released NordLynx VPN Protocol And It’s Really Fast! on Latest Hacking News.
As long as there have been locks, there have been lockpicks to break into them. Steve Jobs and Woz used
The History of Hacking from Phreaking to Cryptocurrencies on Latest Hacking News.
In December of 2017, the FCC voted to repeal net neutrality. What this means is that the internet is now
5 Reasons to Use a VPN in a Net Neutrality-Free World on Latest Hacking News.
If your company is not keeping pace with technological changes or your IT team is too small to cope with
Everything You Need to Know About Managed IT Services on Latest Hacking News.
Taking another step towards users’ privacy with ease, Signal has now announced a new feature. As revealed, Signal has introduced
Signal Hints About Ditching Phone Numbers As User ID As It Introduces Signal PINs on Latest Hacking News.
If you own or are going to own a latest Mac computer, this article can give you useful information that
The Pros and Cons of T2 Chip and A Great Breakthrough in T2 Chip Data Recovery on Latest Hacking News.
Here’s some good news for all iPhone users (and bad news for Apple perhaps). A new jailbreak Unc0ver is out
New Unc0ver iOS Jailbreak Works For All Latest iOS Versions Due To Zero-Day Bug on Latest Hacking News.
Has the landmark law helped build a culture of privacy in organizations and have consumers become more wary of sharing their personal data?
The post Two years later, has GDPR fulfilled its promise? appeared first on WeLiveSecurity
Hello readers, welcome back to a yet another post of The Crazy Programmer. Today I’ll be discussing one of the common error programmers make when they start with programming and that is IndexError. Now before talking about this error, let’s try to see what an Index is and why this error occurs.
An index is a location of an item in an Array or a List and in most of the programming language, it starts from 0. So when we count the elements in a list, we’ll count them from 1 but when we’ll try to access the elements of the list, we’ll start our index from 0. Let us understand this with an example. Please don’t skip the comments.
color = ['red', 'green', 'blue', 'black', 'white'] # index 0 1 2 3 4 # here we can see that we have 5 colors in our color list # but when we'll try to print these items from our list # we can't get color[1] as red # this is because we may find red to be the first element # but technically it is not at index 1 # to print red, we need to use 0 as the index and similarly # for other colors, we have to use the index accordingly print(color[0]) # 0 for red print(color[1]) # 1 for green print(color[2]) # 2 for blue print(color[3]) # 3 for black print(color[4]) # 4 for white
So we can say that green is the 2nd element of the color list but we cannot say that it is at index ‘2’. Similarly white is at 5th position but it is not at 5th index. If we’ll try to access white and if we’ll use print(color[5]) to access white, then it is going to give us an error i.e. IndexError: list index out of range.
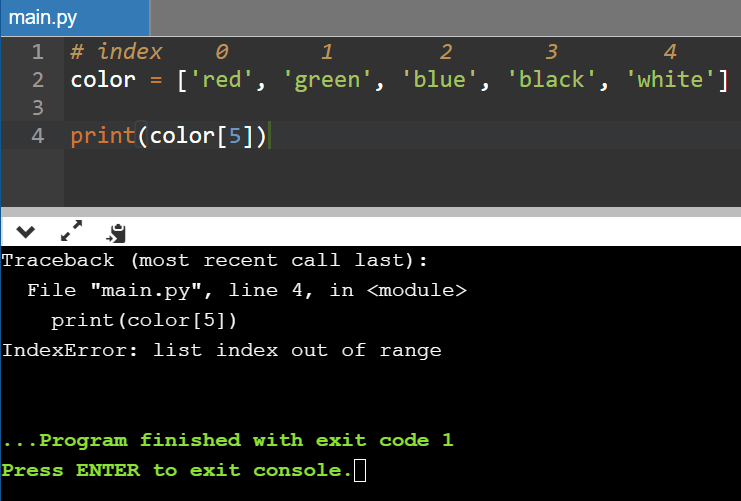
Here we all can see that I’m trying to print the value of a list at an index ‘5’ but here in the array, we don’t have any element at that index.
Now the interpreter will try to parse this code and it will not find any value at 4th index and ultimately it will fail to print the value.
So now I think it is clear why IndexError occurs and how you can avoid them. Still, if you stuck into any kind of error, don’t forget to google it and try to debug it on your own. This will teach you how to debug your code as someone might have faced a similar problem earlier.
If you still don’t find any solution for your problem, you can ask your doubt in the comment’s section below and we’ll get back to you .
.
This was all for today. Thanks for your visit and if you are new here, consider subscribing to our newsletter. See you in my next post. Bye!
The post Solve IndexError: list index out of range in Python appeared first on The Crazy Programmer.
ESET research into Winnti Group's new backdoor – A dangerous Android app under the microscope – The BIAS Bluetooth bug
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
ESET researchers detect a new way of misusing Accessibility Service, the Achilles’ heel of Android security
The post Insidious Android malware gives up all malicious features but one to gain stealth appeared first on WeLiveSecurity
Here’s how encryption can help keep your data safe from prying eyes – even if your device is stolen or your cloud account is hacked
The post How encryption can help protect your sensitive data appeared first on WeLiveSecurity
New features include DNS over HTTPS, a Safety Check section and simpler cookie management
The post Chrome 83 arrives with enhanced security and privacy controls appeared first on WeLiveSecurity
The notorious APT group continues to play the video game industry with yet another backdoor
The post No “Game over” for the Winnti Group appeared first on WeLiveSecurity
Heads up Android users! Here is another threat targeting your devices. New malware WolfRAT has surfaced online that targets messenger
WolfRAT Malware Targets Messengers Apps On Android Devices on Latest Hacking News.
Spyse is a relatively new service in cybersecurity, but their innovative approaches have gained the attention of many pentesters and cybersecurity specialists.
The service itself is a cybersecurity search engine which can be used for gathering mass technical data from the internet. The special thing about Spyse, is that they have one of the largest databases of its kind: hosting all the technical internet data that specialists might need for finding vulnerabilities, gathering competitor data, or just overall reconnaissance.
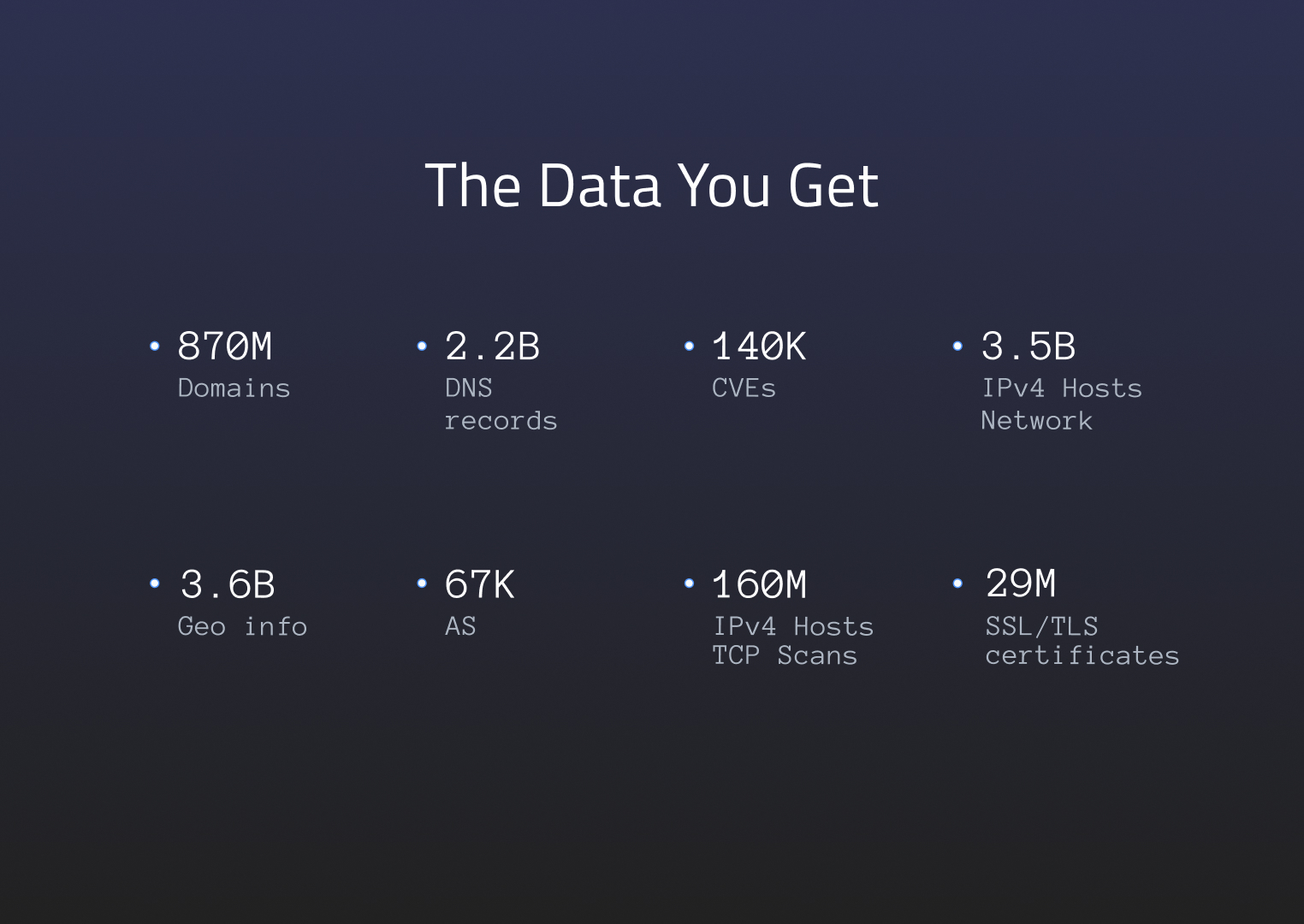
Read on to learn how they collect, store, and provide the data.
Spyse engine performs regular data scans all over the world. This is done thanks to a global server distribution system, which not only lets them bypass area scanning restrictions and ISP blocking, but enables them to harvest much more data from their sources than you would normally get.
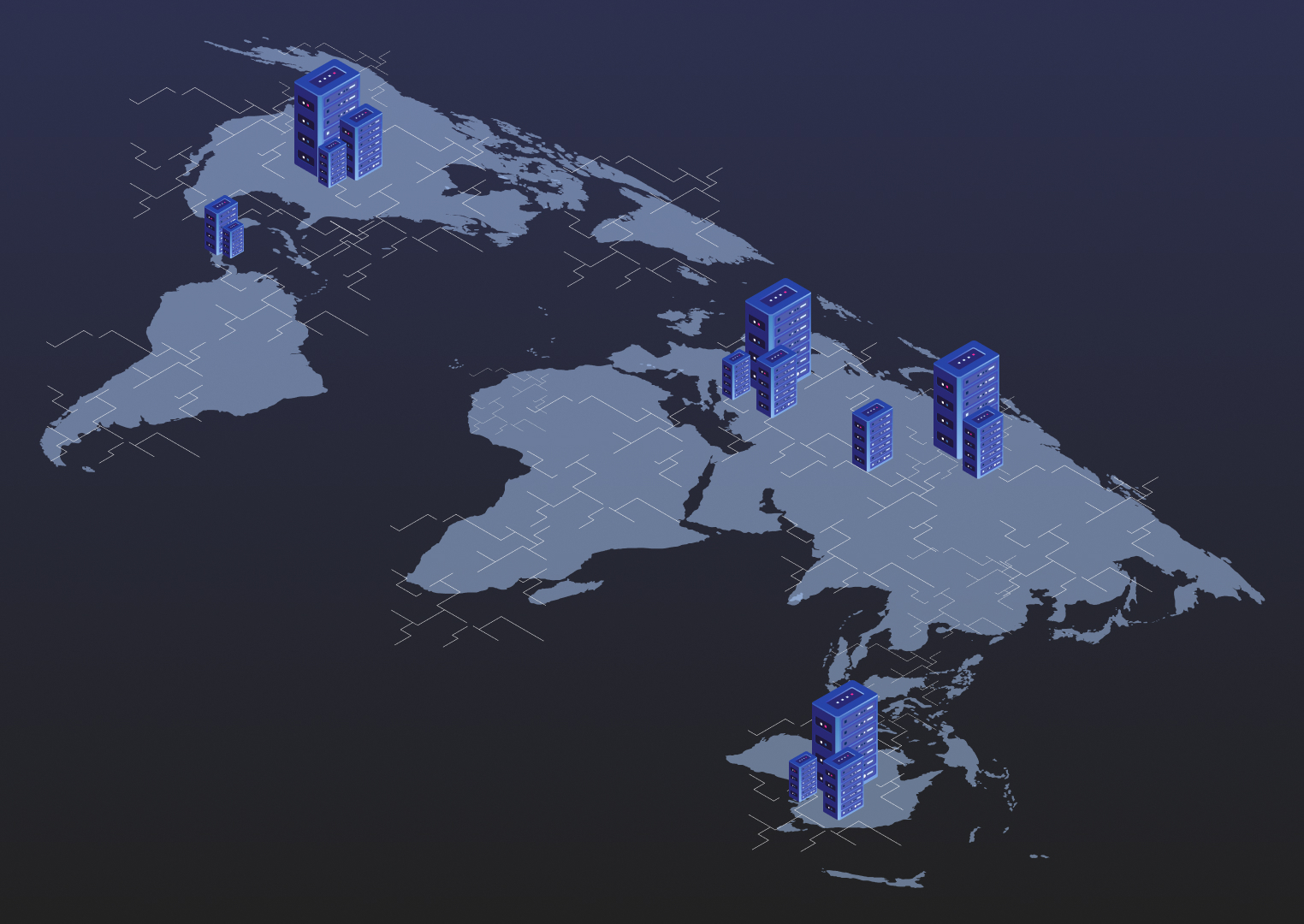
Their scanning infrastructure is composed of ten self-developed scanners. Each of these scanners focuses on collecting specific types of information. After the data is gathered, it gets processed by sorting algorithms and stored into the Spyse database.
The database has all the data users would need for reconnaissance stored and instantly available. Not only that, but searching for data lets users see interlinked, or connected results. This makes for more browsing opportunities like gaining extra information on targets, seeing more vectors of attack, even visualizing tech-data relationships between different companies.
The database itself stores over 7 billion documents of hot data on 50 high-functioning and most reliable servers. This data contains everything: DNS records, SSL/TLS certificate data, domains and subdomains of various organizations, IP data, and much more. The biggest perk is the fact that you can access all of it instantly, without having to wait for scans.
Spyse can be accessed through a web interface and an API.
The web interface looks like a familiar search engine perked for cybersecurity. Search results return in tables which can then be filtered to get a more convenient look. All found results can then be downloaded and accessed offline.
Alternatively, users can use this search engine via flexible API or integrate it with their tools and services. API has a documentation on Swagger, which makes it a pleasure to work with. It’s flexible, and can be used with many methods which are outlined on the API documentation.
There are two handy features that alleviate the utility of this cybersecurity search engine.
The Advanced Search is a live filter which helps sort big chunks of data as you’re browsing through the database. Users can apply up to 5 search parameters per query to extract very specific data that can’t be received with a simple search. For example: searching for ports users can obtain all open ports with specific CVEs, define products, applications, OS, and more in relation to some company.
To get quick information about open ports users may use Spyse’s port scanner that provides instant data without waiting for long scans.
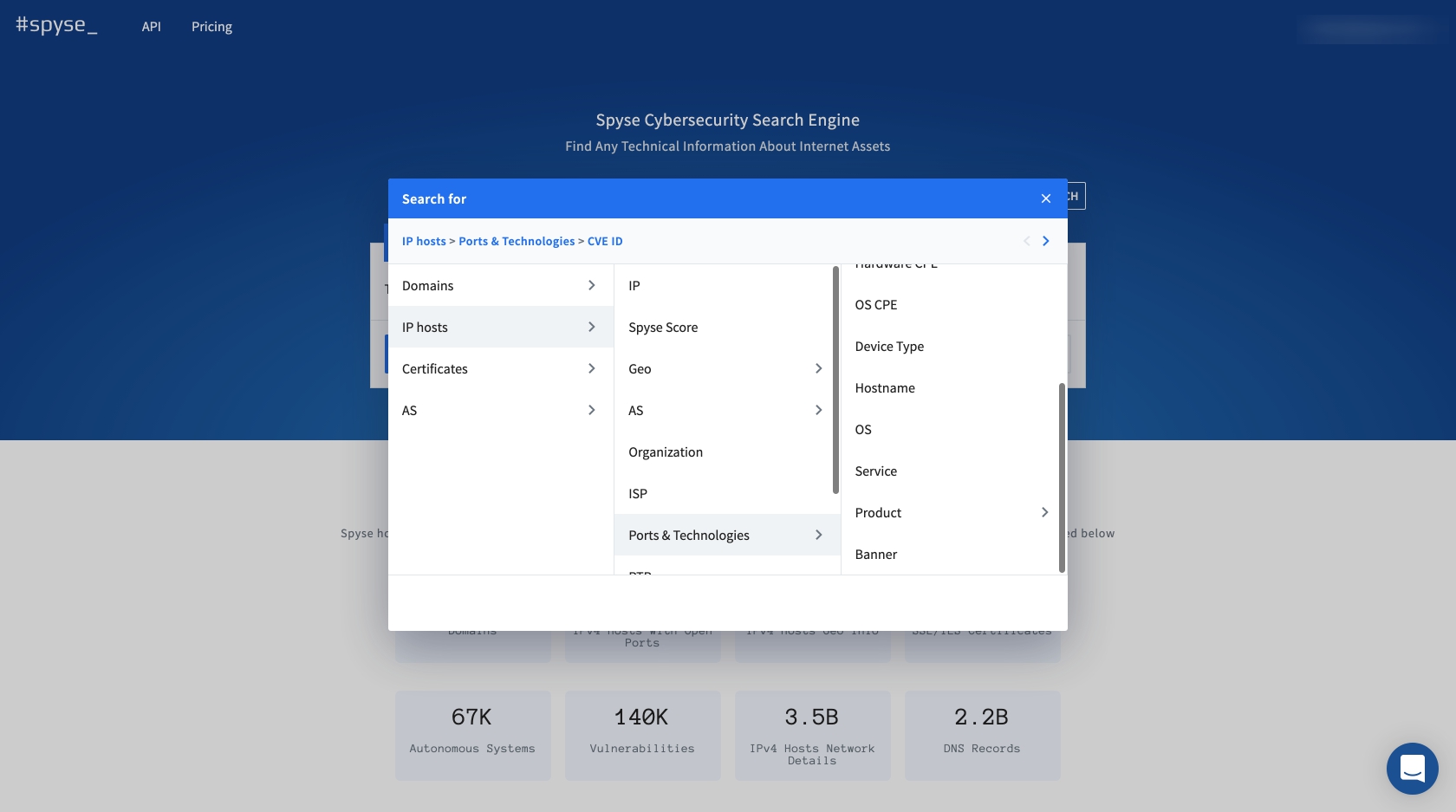
Spyse Scoring is another powerful feature which analyzes targets for vulnerabilities. It compares all information found by spyse scanners, and shows the level of security based on the rating of 0-100. Each found vulnerability is presented with expanded details that explains its severity, vector, dates and other info.
But it significantly improves when used in combination with the Advanced Search, allowing search by CVE IDs and the vulnerability score combining it with other search parameters for fascinating results.
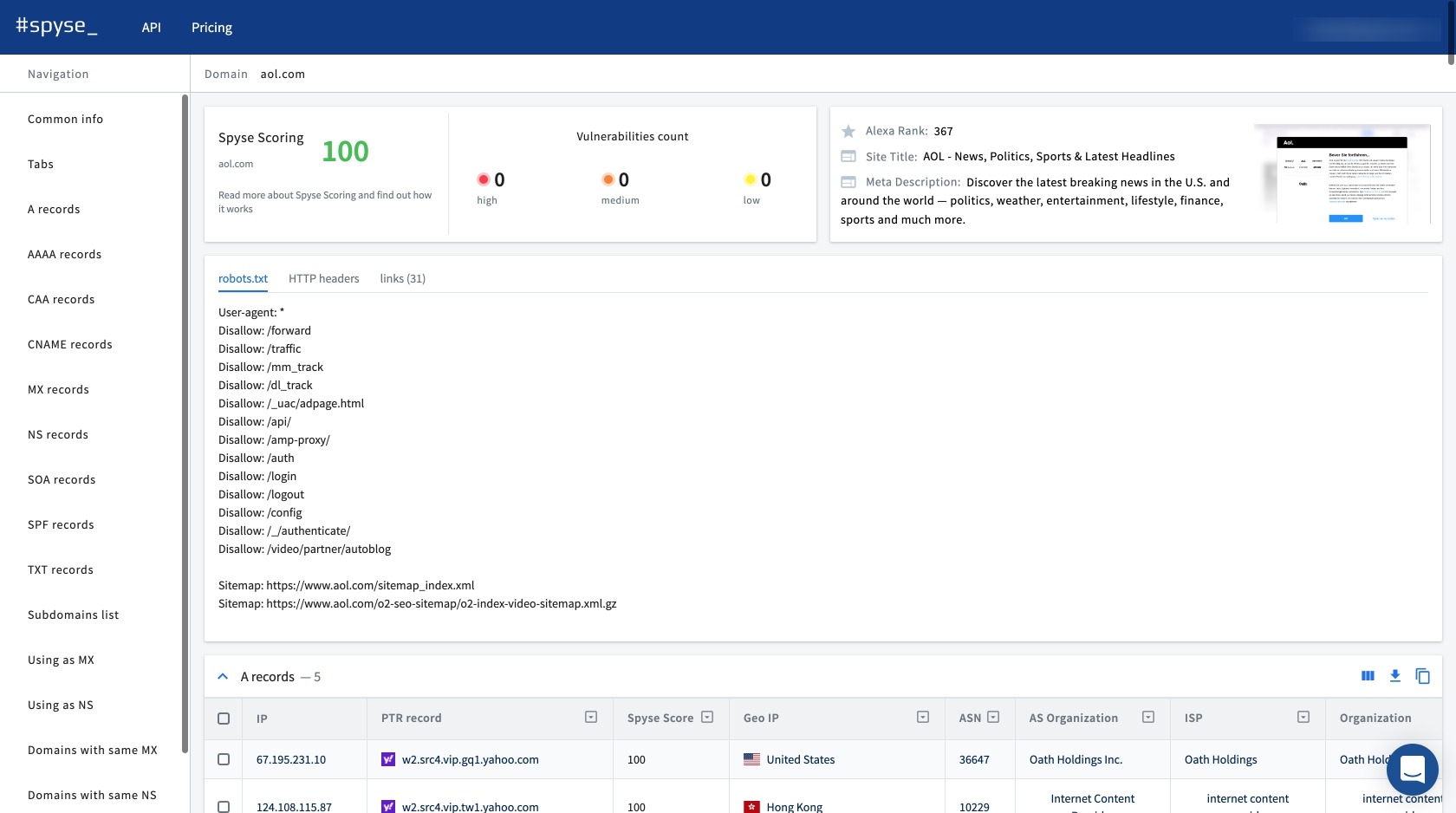
Using this search engine pentesters and bug bounty hunters will always remain invisible while seeking vulnerabilities, save money and time for their own scanning infrastructure and avoid the rate limits. It can also be used when other methods are rendered unavailable by contract or bug bounty agreement.
Overall, Spyse significantly improves the quality of specialists’ work and provides some new experience solving the daily routine tasks.
The post Spyse – Cybersecurity Search Engine for Quick Recon appeared first on The Crazy Programmer.
In the rush to embrace IoT devices, we shouldn’t trade in our privacy and security for the added convenience
The post These things may be cool, but are they safe? appeared first on WeLiveSecurity
Distributed Denial of Service (DDoS) attacks can be seemingly innocuous as they don’t usually involve a breach of data or
How DDoS Attacks Are Evolving In 2020 on Latest Hacking News.
When the world is adamant to limit your internet freedom, one thing still respects your rights – a Smart DNS.
Review Of KeepSolid Smart DNS – A Quick Way To Bypass Georestrictions on Latest Hacking News.
When we talk about a programming language, we can say them as a medium to communicate with the computer. To express ourselves, we as humans talk with each other using any of our native languages but we cannot simply communicate with the computer the same way.
It simply can’t understand our native language. Instead, we need a translator who can translate our language into a computer’s language.
Now, before talking about the translator, I want to talk about the topic of today’s post, i.e. is HTML a programming language?
HTML is a declarative programming language. What does that mean? Well, a declarative programming language is a paradigm that only states what the result should look like and not hot to achieve it. We use basic statements for achieving something we want. Here we use constraints to describe a user interface.
User Interface
This is how we use constraints for creating a UI using HTML.
<!DOCTYPE html>
<html>
<head>
<title>Page Title</title>
</head>
<body>
<h1>This is a Heading</h1>
<p>This is a paragraph.</p>
</body>
</html>
These constraints are going to describe the structure of our UI. Here the h1 is going to be a heading of our UI and the p is going to be the paragraph of our UI. The HTML parser or the HTML engine of the browser is going to render the UI from the above constraints. Here, we haven’t described how to achieve our desired UI.
Whereas in other programming languages, we have to teach a computer how to achieve a particular result. For example, if we want to make a simple calculator, we need to show the computer how to do that.
a = int(input('Enter number'))
b = int(input('Enter number'))
c = a + b
print ('Sum of a and b is: {0}'.format(c))
All these programming logic can’t be implemented using HTML and can only be achieved when we use Javascript, a type of programming language for the web.
So, how to implement the same logic using HTML and JS? Let’s see.
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="content-type" content="text/html; charset=utf-8" />
<title>Add two numbers</title>
</head>
<body>
<input type="number" name="first_num" id="x" placeholder="Enter first number"/>
<br />
<input type="number" name="second_num" id="y" placeholder="Enter second number"/>
<br />
<button id="go">Calculate</button>
<div id="result"></div>
<script>
"use strict";
function add() {
var x = Number(document.getElementById('x').value);
var y = Number(document.getElementById('y').value);
document.getElementById('result').innerHTML = x+y;
return false;
}
document.getElementById('go').addEventListener('click', add);
</script>
</body>
</html>
This states that we can’t implement programming logic in HTML but we can achieve that using Javascript.
Now, I hope you get what I’m trying to say for HTML.
Well, this was all about today’s topic and points related to it. If you stuck into any kind of confusion, don’t forget to google it and try to solve it on your own. This will teach you how to learn on your own as someone might have faced a similar problem earlier.
Still, if you still don’t find any solution for your problem, you can ask your doubt in the comment’s section below and we’ll get back to you . Till then enjoy your code. See you in my next post. Bye
. Till then enjoy your code. See you in my next post. Bye !
!
The post Is HTML a Programming Language? appeared first on The Crazy Programmer.
As many as 30 smartphones, laptops and other devices were tested – and all were found to be vulnerable
The post Bluetooth flaw exposes countless devices to BIAS attacks appeared first on WeLiveSecurity

How do they do it?
“How is [insert developer name] able to attract the promotions and job offers they’re getting? Their work is trash; I’m a much better developer! I work twice as hard, write better code, and produce 2x more work than they do? This is completely unfair.”
You’re right, it is unfair.
This is a serious career problem, assuming that you’ve made an accurate assumption about your skills and performance. Seriously, what gives?
It’s a common mistake made by many employees in general. Here’s a quote from Reddit user Myidiotbox that encapsulates both the attitude of many employees and the response they receive in return.
This is the unspoken attitude lurking beneath for many people.
“I’m working really hard so I deserve X. I did my job well so I want Y.”
Here’s the problem with this attitude.
It takes you further away from the goals you want (such as being treated well, making more money, achieving significance, and so on). This perception is the primary reason so many developers fail to achieve the career goals they aspire to.
Here are the goals (if you can call them that) a healthy employer looks for.
See the problem?
There’s a mismatch here. The vast majority of people are struggling with Dunning-Kruger effect and are prone to overestimate their competence. They believe they’re doing a better job relative to their peers.
But they’re not.
Here’s why this is an issue. This mismatched thinking puts you at odds with your employer. This creates significant problems down the line, too, because it turns employees (you) in to mercenaries over time.
If this sounds harsh, it’s not intended to be.
Here are some simple strategies web developers can use to attract the positions other developers want with minimal effort.
In 2013, Gallup worked with then Nationwide CEO Steve Rasmussen to improve employee engagement. In the course of their relationship, Rasmussen shared a surprising observation.
Employees are either patriots or mercenaries.
Not because they want to be but because they have to be.
Patriots totally identify with their company, and mercenaries are more likely to focus on personal outcomes.
Patriot employees are engaged. They have ownership, they believe in their firm and their firm believes in them. Instead of looking out for themselves, they’re focused on looking out for their firm.
On the other hand, mercenaries are focused on themselves. They tend to rely on serial job-hopping, power hoarding, and social climbing to get what they want. Mercenaries are focused on getting as much value as they can for themselves; they don’t care much about their company.
It’s no surprise then that they’re disengaged.
If the interests of the firm happen to align with their own interests, they’ll do what’s best for the firm. But they’re not really focused on putting their firm ahead of themselves.
Most of the time they can’t.
Why? Because their employer is a mercenary: these employers are focused on squeezing as much value as they can out of their employees. Then, they’re tossed aside once they’re burned out and used up.
You’ll want to stay a patriot.
This means you continue to buy in to your company’s vision. You continue to believe in your employer or co-workers and you look out for them. The instant you can’t do that, you start looking for another job. Here’s why it’s important to remain a patriot.
The exceptional opportunities, benefits, and rewards go overwhelmingly to people who like, trust, and believe in you. These people can smell your intentions, partially due to the fact that humans communicate chemically.
Additionally, there’s a certain kind of tone, inflection, attention, and posture that’s communicated when we’re actually interested and engaged in something. If you’re like most humans on planet Earth, you know what that looks like. The better you are at remaining invested in your employer and co-workers — helping them solve tough problems, sticking with them through bad times — the easier it is win these coveted positions.
Continue reading Simple Strategies for Winning the Positions Other Developers Want on SitePoint.
Several high-performance computers working on COVID-19 research have been forced offline following a string of attacks
The post European supercomputers hacked to mine cryptocurrency appeared first on WeLiveSecurity
There’s no doubt about it, we’re surrounded by technology and submit to an awful lot of data collection in return
5 Privacy Risks You Might Not Know About on Latest Hacking News.
Some of the top internet service providers offer free public Wi-Fi hotspots throughout the country. I really appreciate these hotspots
How to Choose a VPN for Yourself on Latest Hacking News.
Cyber warfare is not the distant future of international wars – it’s the reality of today. Every digital tool and
Cyber Warfare – Today and Tomorrow on Latest Hacking News.
After WhatsApp and Instagram, Facebook now acquire a new company. As announced, Facebook has acquired the popular GIF-maker platform GIPHY.
Facebook Acquires GIPHY For $400 Million To Integrate It With Instagram on Latest Hacking News.
Continuing the trail of security threats to air-gapped systems, now joins a malware. Dubbed Ramsay, the malware with as much
New Ramsay Malware Can Steal Data From Air-Gapped Networks on Latest Hacking News.
While numerous Android malware kesep emerging online every now and then, this malware stayed under the radar for years. Identified
Mandrake Malware Is Secretly Spying On Android Users For Several Years on Latest Hacking News.
As the world is in a standstill and people are relying more on delivery services, the threat actors are targeting
Pitney Bowes Suffered Second Ransomware Attack Within A Year on Latest Hacking News.
ESET research into malware taking aim at air-gapped networks – Dissecting a backdoor hitting high-profile targets in Asia – WannaCryptor three years later
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
Another vulnerability in the same Windows component was abused by Stuxnet a decade ago
The post Microsoft fixes vulnerability affecting all Windows versions since 1996 appeared first on WeLiveSecurity
Astaroth Trojan that has been around for several years is now back with even more features. This time, Astaroth malware
Astaroth Malware Evolves Further To Abuse YouTube Channel Descriptions on Latest Hacking News.
Continuing the list of plugins risking WordPress websites, now joins Site Kit by Google. This Google WordPress plugin had a
Google WordPress Plugin Bug Allowed Attackers To Access Google Search Console on Latest Hacking News.
How many of us are Python Programmers here? I hope many of us and I hope almost all of us might have come across SyntaxError: unexpected EOF while parsing and we might have tried to look for it somewhere online.
But do you exactly know what is this error all about and how we can remove it from our python code?
So, what exactly an EOF is?
EOF stands for End Of File. This means we have now come to the end of our file and the error related to this is shown below with example code.
Suppose I was writing a program in python and I forget to write it in proper syntax. For example:
num = [1, 2, 3, 4, 5]
# here in for loop, I tried to end the print function in a wrong way
for i in num:
print(i
Now the above code contains one error and the error is that the print function in the above code is not closed properly. We can see that it doesn’t have the closing parenthesis print( .
Now, when we tried to run this code, it showed us SyntaxError: unexpected EOF while parsing
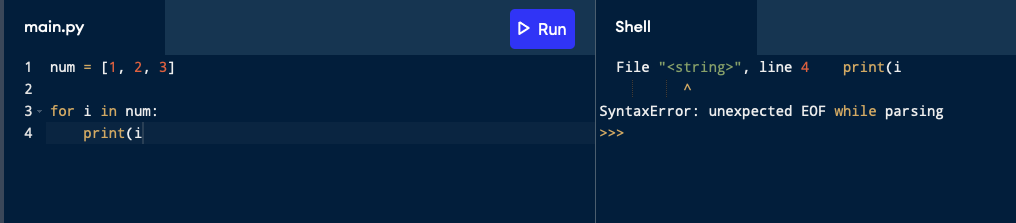
Now the problem is before our print function ends, our file ended. This lead to the SyntaxError: unexpected EOF while parsing. To overcome this type of error in our python file, we need to ensure that we have not left any part of our code unclosed or not in proper syntax. I hope this is clear to you.
Well, this was all about the EOF and the error related to it. If you stuck into any kind of error, don’t forget to google it and try to debug it on your own. This will teach you how to debug on your own as someone might have faced a similar problem earlier.
If you still don’t find any solution for your problem, you can ask your doubt in the comment’s section below and we’ll get back to you .
.
Thanks for your visit and if you are new here, consider subscribing to our newsletter. See you in my next post. Bye!
The post Solve SyntaxError: unexpected EOF while parsing appeared first on The Crazy Programmer.