The popular video platform Vimeo is now in hot water for breaching users’ privacy. Vimeo faces a class-action lawsuit for
Vimeo Faces Class-Action Lawsuit Over Unconsented Storage Of Users’ Biometric Data on Latest Hacking News.
The popular video platform Vimeo is now in hot water for breaching users’ privacy. Vimeo faces a class-action lawsuit for
Vimeo Faces Class-Action Lawsuit Over Unconsented Storage Of Users’ Biometric Data on Latest Hacking News.
Once again, Google’s Play Store has made it into the news following the existence of apps that overcharge users for
Researchers Highlight “Fleeceware” Android Apps That Aim to Overcharge Users on Latest Hacking News.
Using third-party keyboards on your iPhone is something of a normality for many iOS users. However, it could be troublesome
Apple Patched An iOS 13.1 Bug That Granted ‘Full Access’ To Third-Party Keyboards on Latest Hacking News.
The online food delivery service DoorDash has recently confessed to a data breach targeting millions. As revealed, the company suffered
DoorDash Confirmed Data Breach Affecting 4.9 Million Customers on Latest Hacking News.
In this article, we will learn about tree and some of the common types of trees in data structure.
Tree in computer science is like a tree in the real world, the only difference is that in computer science it is visualized as upside-down with root on the top and branches originating from the root to the leaves of the tree. Tree Data Structure is used for various real-world applications as it can show relation among various nodes using the parent-child hierarchy. Due to this it is also known as hierarchical data structure. It is widely used to simplify and fasten searching and sorting operations. It is considered to be one of the most powerful and advanced data structures.
Tree is a non-linear data structure. A tree can be represented using various primitive or user defined data types. To implement tree, we can make use of arrays, linked lists, classes or other types of data structures. It is a collection of nodes that are related with each other. To show the relation, nodes are connected with edges.
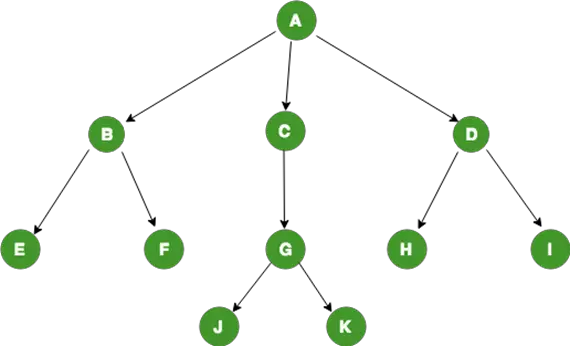
Fig 1: General Tree structure (Source)
Relations in a Tree:
Properties of Tree:
A tree is called a general tree when there is no constraint imposed on the hierarchy of the tree. In General Tree, each node can have infinite number of children. This tree is the super-set of all other types of trees. The tree shown in Fig 1 is a General Tree.
Binary tree is the type of tree in which each parent can have at most two children. The children are referred to as left child or right child. This is one of the most commonly used trees. When certain constraints and properties are imposed on Binary tree it results in a number of other widely used trees like BST (Binary Search Tree), AVL tree, RBT tree etc. We will see all these types in details as we move ahead.
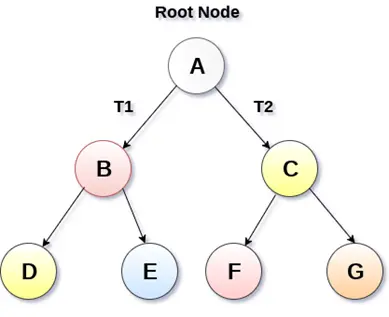
Fig 2: Binary Tree (Source)
Binary Search Tree (BST) is an extension of Binary tree with some added constraints. In BST, the value of the left child of a node must be smaller than or equal to the value of its parent and the value of the right child is always larger than or equal to the value of its parent. This property of Binary Search Tree makes it suitable for searching operations as at each node we can decide accurately whether the value will be in left subtree or right subtree. Therefore, it is called a Search Tree.
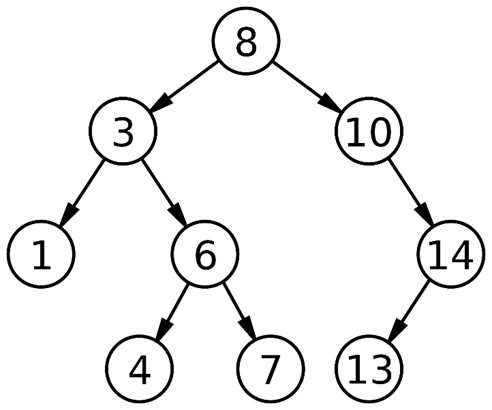
Fig 3: Binary Search Tree (Source)
AVL tree is a self-balancing binary search tree. The name AVL is given on the name of its inventors Adelson-Velshi and Landis. This was the first dynamically balancing tree. In AVL tree, each node is assigned a balancing factor based on which it is calculated whether the tree is balanced or not. In AVL tree, the heights of children of a node differ by at most 1. The valid balancing factor in AVL tree are 1, 0 and -1. When a new node is added to the AVL tree and tree becomes unbalanced then rotation is done to make sure that the tree remains balanced. The common operations like lookup, insertion and deletion takes O(log n) time in AVL tree. It is widely used for Lookup operations.
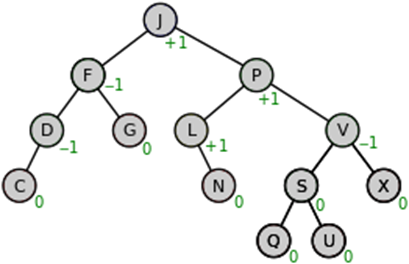
Fig 4: Source
Red-Black is another type of self-balancing tree. The name Red-Black is given to it because each node in a Red-Black tree is either painted Red or Black according to the properties of the Red- Black Tree. This make sure that the tree remains balanced. Although the Red-Black tree is not a perfectly balanced tree but its properties ensure that the searching operation takes only O(log n) time. Whenever a new node is added to the Red-Black Tree, the nodes are rotated and painted again if needed to maintain the properties of the Red-Black Tree .

Fig 5: Red-Black Tree (Source)
In an N-ary tree, the maximum number of children that a node can have is limited to N. A binary tree is 2-ary tree as each node in binary tree has at most 2 children. Trie data structure is one of the most commonly used implementation of N-ary tree. A full N-ary tree is a tree in which children of a node is either 0 or N. A complete N-ary tree is the tree in which all the leaf nodes are at the same level.
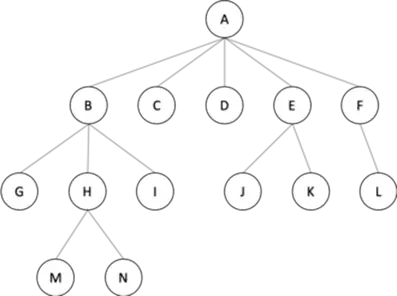
Fig 6: N-ary tree (5-ary)
I hope you got the idea about some of the common types of trees in data structure. If you have any queries then feel free to ask in the comment section.
The post Types of Trees in Data Structure appeared first on The Crazy Programmer.

Svelte is a new JavaScript UI library that's similar in many ways to modern UI libraries like React. One important difference is that it doesn't use the concept of a virtual DOM.
In this tutorial, we'll be introducing Svelte by building a news application inspired by the Daily Planet, a fictional newspaper from the Superman world.
Svelte makes use of a new approach to building users interfaces. Instead of doing the necessary work in the browser, Svelte shifts that work to a compile-time phase that happens on the development machine when you're building your app.
In a nutshell, this is how Svelte works (as stated in the official blog):
Svelte runs at build time, converting your components into highly efficient imperative code that surgically updates the DOM. As a result, you're able to write ambitious applications with excellent performance characteristics.
Svelte is faster than the most powerful frameworks (React, Vue and Angular) because it doesn't use a virtual DOM and surgically updates only the parts that change.
We'll be learning about the basic concepts like Svelte components and how to fetch and iterate over arrays of data. We'll also learn how to initialize a Svelte project, run a local development server and build the final bundle.
You need to have a few prerequisites, so you can follow this tutorial comfortably, such as:
Node.js can be easily installed from the official website or you can also use NVM for easily installing and managing multiple versions of Node in your system.
We'll be using a JSON API as a source of the news for our app, so you need to get an API key by simply creating an account for free and taking note of your API key.
Now, let's start building our Daily Planet news application by using the degit tool for generating Svelte projects.
You can either install degit globally on your system or use the npx tool to execute it from npm. Open a new terminal and run the following command:
npx degit sveltejs/template dailyplanetnews
Next, navigate inside your project's folder and run the development server using the following commands:
cd dailyplanetnews
npm run dev
Your dev server will be listening from the http://localhost:5000 address. If you do any changes, they'll be rebuilt and live-reloaded into your running app.
Open the main.js file of your project, and you should find the following code:
import App from './App.svelte';
const app = new App({
target: document.body,
props: {
name: 'world'
}
});
export default app;
This is where the Svelte app is bootstrapped by creating and exporting an instance of the root component, conventionally called App. The component takes an object with a target and props attributes.
The target contains the DOM element where the component will be mounted, and props contains the properties that we want to pass to the App component. In this case, it's just a name with the world value.
Open the App.svelte file, and you should find the following code:
<script>
export let name;
</script>
<style>
h1 {
color: purple;
}
</style>
<h1>Hello {name}!</h1>
This is the root component of our application. All the other components will be children of App.
Components in Svelte use the .svelte extension for source files, which contain all the JavaScript, styles and markup for a component.
The export let name; syntax creates a component prop called name. We use variable interpolation—{...}—to display the value passed via the name prop.
You can simply use plain old JavaScript, CSS, and HTML that you are familiar with to create Svelte components. Svelte also adds some template syntax to HTML for variable interpolation and looping through lists of data, etc.
Since this is a small app, we can simply implement the required functionality in the App component.
In the <script> tag, import the onMount() method from "svelte" and define the API_KEY, articles, and URL variables which will hold the news API key, the fetched news articles and the endpoint that provides data:
<script>
export let name;
import { onMount } from "svelte";
const API_KEY = "<YOUR_API_KEY_HERE>";
const URL = `https://newsapi.org/v2/everything?q=comics&sortBy=publishedAt&apiKey=${API_KEY}`;
let articles = [];
</script>
onMount is a lifecycle method. Here’s what the official tutorial says about that:
Every component has a lifecycle that starts when it is created and ends when it is destroyed. There are a handful of functions that allow you to run code at key moments during that lifecycle. The one you'll use most frequently is
onMount, which runs after the component is first rendered to the DOM.
Next, let's use the fetch API to fetch data from the news endpoint and store the articles in the articles variable when the component is mounted in the DOM:
<script>
// [...]
onMount(async function() {
const response = await fetch(URL);
const json = await response.json();
articles = json["articles"];
});
</script>
Since the fetch() method returns a JavaScript Promise, we can use the async/await syntax to make the code look synchronous and eliminate callbacks.
The post How to Build a News App with Svelte appeared first on SitePoint.
ESET researchers break down a revamped set of tools that the Sednit group has added to its Zebrocy malware family
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
Almost 60% of second-hand hard drives hold leftover data from previous owners, a study shows
The post Are you sure you wiped your hard drive properly? appeared first on WeLiveSecurity
Cybercriminals have recently been targeting U.S. Veterans. As discovered by researchers, the hackers tend to entice U.S Veterans with a
Hackers Target U.S Veterans With Malicious Employment Website on Latest Hacking News.
Heads up Instagram users! Here is another scam preying on your accounts. As discovered by researchers, a new Instagram phishing
New Instagram Phishing Attack Tricks Users With Fake Copyright Infringement Alerts on Latest Hacking News.
We already have witnessed the innovativeness of criminal hackers in exploiting various services to bait users. From regular email phishing
Scammers Exploit Google Alerts To Trick Users on Latest Hacking News.
Rosh HaAyin, ISRAEL — Cybersecurity firm odix recently secured a €2 million grant from the European Commission (EC) to bring
European Commission Awards Odix €2M to Deliver their proven ransomware protection technology to SMEs on Latest Hacking News.
SOX — the Sarbanes–Oxley Act — is public legislation in the US that helps “to protect investors by improving the
How does SOX Compliance Benefit your Organization? on Latest Hacking News.
Today we are going to learn about Apriori Algorithm. Before we start with that we need to know a little bit about Data Mining.
What is Data Mining ?
Data Mining is a non-trivial process of identifying valid, novel, potentially useful and ultimately understandable patterns in data.
Apriori Algorithm is concerned with Data Mining and it helps us to predict information based on previous data.
In many e-commerce websites we see a recently bought together feature or the suggestion feature after purchasing or searching for a particular item, these suggestions are based on previous purchase of that item and Apriori Algorithm can be used to make such suggestions.
Before we start with Apriori we need to understand a few simple terms :
Association Mining: It is finding different association in our data.
For E.g. If you are buying butter then there is a great chance that you will buy bread too so there is an association between bread and butter here.
Support: It specifies how many of the total transactions contain these items.
Support(A->B) denotes how many transactions have all items from AUB
Therefore
Therefore 10% support will mean that 10% of all the transactions contain all the items in AUB.
Confidence: For a transaction A->B Confidence is the number of time B is occuring when A has occurred.
Note that Confidence of A->B will be different than confidence of B->A.
Confidence(A->B) = P(AUB)/P(A).
Support_Count(A): The number of transactions in which A appears.
An itemset having number of items greater than support count is said to be frequent itemset.
Apriori algorithm is used to find frequent itemset in a database of different transactions with some minimal support count. Apriori algorithm prior knowledge to do the same, therefore the name Apriori. It states that
All subsets of a frequent itemset must be frequent.
If an itemset is infrequent, all its supersets will be infrequent.
Let’s go through an example :
| Transaction ID | Items |
| 1 | I1 I3 I4 |
| 2 | I2 I3 I5 |
| 3 | I1 I2 I3 I5 |
| 4 | I2 I5 |
We will first find Candidate set (denoted by Ci) which is the count of that item in Transactions.
C1:
| Items | Support Count |
| I1 | 2 |
| I2 | 3 |
| I3 | 3 |
| I4 | 1 |
| I5 | 3 |
The items whose support count is greater than or equal to a particular min support count are included in L set
Let’s say support count for above problem be 2
L1:
| Items | Support Count |
| I1 | 2 |
| I2 | 3 |
| I3 | 3 |
| I5 | 3 |
Next is the joining step we will combine the different element in L1 in order to form C2 which is candidate of size 2 then again we will go through the database and find the count of transactions having all the items. We will continue this process till we find a L set having no elements.
C2:
| Items | Support Count |
| I1,I2 | 1 |
| I1,I3 | 2 |
| I1,I5 | 1 |
| I2,I3 | 2 |
| I2,I5 | 3 |
| I3,I5 | 2 |
We will remove sets which have count less than min support count and form L2
L2:
| Items | Support Count |
| I1,I3 | 2 |
| I2,I3 | 2 |
| I2,I5 | 3 |
| I3,I5 | 2 |
Now we will join L2 to form C3
Note that we cannot combine {I1,I3} and {I2,I5} because then the set will contain 4 elements. The rule here is the there should be only one element in both set which are distinct all other elements should be the same.
C3:
| Items | Support Count |
| I1,I2,I3 | 1 |
| I1,I3,I5 | 1 |
| I2,I3,I5 | 2 |
L3:
| Item | Support Count |
| I2,I3,I5 | 2 |
Now we cannot form C4 therefore the algorithm will terminate here.
Now we have to calculate the strong association rules. The rules having a minimum confidence are said to be strong association rules.
Suppose for this example the minimum confidence be 75%.
There can be three candidates for strong association rules.
I2^I3->I5 = support(I2^I3)/support(I5) = ⅔ = 66.66%
I3^I5->I2 = support(I3^I5)/support(I2) = ⅔ = 66.66%
I2^I5->I3 = support(I2^I5)/support(I3) = 3/3 = 100%
So in this example the strong association rule is
I2^I5->I3.
So from the above example we can draw conclusion that if someone is buying I2 and I5 then he/she is most likely to buy I3 too. This is used to make suggestions while we are purchasing online.
The Algorithm to calculate the frequent itemset is as below:
Ck : Candidate Set of size k
Lk : Frequent set of size k
min_sup : Minimum support count
T : Database
For all transactions t in T :
do
Go through the items in t
If item already present in set C1 then increase count
else insert item in C1 with count 1
end
For all items I in C
do
If count of I > min_sup
L1 ← Item in C1
end
for(k=1 ; Lk!=ɸ ; k++)
do
Ck+1 ← Candidates generated from Lk
for all transactions t in T
do
if Ck+1 a subset of t
increase count of Ck+1
end
For all items I in C
do
If count of I > min_sup
Lk+1 ← Item in Ck
end
end
Comment down below if you have any queries related to Apriori Algorithm.
The post Apriori Algorithm appeared first on The Crazy Programmer.
With ever-increasing usage of mobile apps, geolocation and tracking functionality can be found in a majority of apps. Real-time geolocation tracking plays an important role in many on-demand services, such as these:
In this guide, we’re going use React Native to create a real-time location tracking apps. We’ll build two React Native apps. One will act as a tracking app (called “Tracking app”) and the other will be the one that’s tracked (“Trackee app”).
Here’s what the final output for this tutorial will look like:
[video width="640" height="480" mp4="https://dab1nmslvvntp.cloudfront.net/wp-content/uploads/2019/09/1569381508tracking.mp4"][/video]
This tutorial requires a basic knowledge of React Native. To set up your development machine, follow the official guide here.
Apart from React Native, we’ll also be using PubNub, a third-party service that provides real-time data transfer and updates. We’ll use this service to update the user coordinates in real time.
Register for a free PubNub account here.
Since we’ll be using Google Maps on Android, we’ll also need a Google Maps API key, which you can obtain on the Google Maps Get API key page.
To make sure we’re on the same page, these are the versions used in this tutorial:
If you want to have a look at the source code of our Tracker and Trackee apps right away, here are their GitHub links:
Let’s start with the Trackee app first.
To create a new project using react-native-cli, type this in the terminal:
$ react-native init trackeeApp
$ cd trackeeApp
Now let’s get to the fun part — the coding.
Since we’ll be using Maps in our app, we’ll need a library for this. We’ll use react-native-maps.
Install react-native-maps by following the installation instructions here.
Apart from maps, we’ll also install the PubNub React SDK to transfer our data in real time:
$ yarn add pubnub-react
After that, you can now run the app:
$ react-native run-ios
$ react-native run-android
You should see something like this on your simulator/emulator:
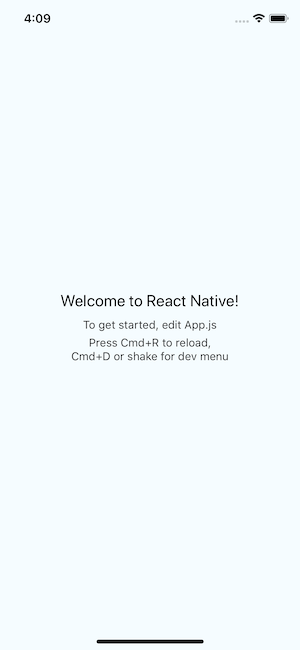
The post Real-time Location Tracking with React Native and PubNub appeared first on SitePoint.
There is no word on which threat actor is abusing the severe vulnerability for attacks
The post Microsoft rushes out patch for Internet Explorer zero‑day appeared first on WeLiveSecurity
Although, the existence of malicious applications on the Android Play Store isn’t anything new. Researchers have now discovered how these
Malicious Android Apps Reach Play Store As They Evade Google Play Protect on Latest Hacking News.
Microsoft has urgently patched two security vulnerabilities, one of which is an actively exploited zero-day. Urgently Patched Microsoft Zero-Day Microsoft
Microsoft Urgently Patched Two Vulnerabilities Including A Zero-Day on Latest Hacking News.
A serious security bug has been discovered in Forcepoint VPN Client for Windows. According to researchers, the bug, upon an
Bug In Forcepoint VPN Client Could Trigger Privilege Escalation Attacks on Latest Hacking News.
The existence of malicious apps on the Android Play Store is now becoming the new normal. Though, not desirable. Still,
Google Removed Numerous Android Apps Delivering Adware From The Play Store on Latest Hacking News.
Abusing Microsofts login page is becoming increasingly popular among scammers. We have recently heard of numerous phishing scams exploiting Microsoft
This Microsoft Phishing Campaign Is Easy To Fend Off As Attackers Steal Credentials Via Email on Latest Hacking News.
Following Google, the other tech giant Microsoft also seems busy making privacy updates in its browser. As revealed recently, Microsoft
Microsoft Edge Will Soon Allow Users to Block ‘Potentially Unwanted Apps’ on Latest Hacking News.
Many companies are ranking cybersecurity as a top 5 priority but their actions do not measure up to the claim, a survey finds
The post Do companies take cybersecurity seriously enough? appeared first on WeLiveSecurity
According to statistics, WordPress accounted for 90% of hacked CMS sites in 2018. WordPress is a favorite for website owners,
Top Reasons Why WordPress Sites Get Hacked on Latest Hacking News.
Ad blocker add-ons can also cause trouble to users. Recently, Google has busted two ad blockers from Chrome for ‘cookie
Google Removed Otherwise Functional Chrome Ad Blockers For Cookie Stuffing on Latest Hacking News.
In this tutorial, I will tell you how to build a basic tic tac toe game using HTML, CSS and JavaScript.
Most of the people know that when we were kids we used to play this game on paper. We played it many times till we win.
Those who don’t know about this game let me give you little overview. In this game there are two players, the player who makes three of their marks in row and column or one of the two diagonals wins the game. When the board fills up and no combination making then the game is in draw state.
There are some rules that we are going to define here is that as we know the primary thing is move, here the player cannot undo that move. By clicking on the box he can make a move as soon as the move is done, the game proceeded to give a chance to another player.
At each move, it will show whose player moves it is either is A or it is B
When the game ends it displays three outcomes:
It also displays the replay button if a tie happens.
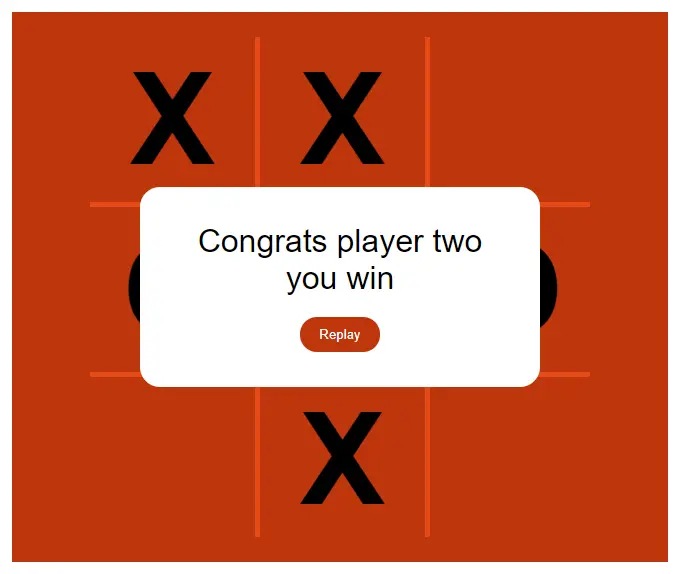
Its programming is not that simple as it looks. In this js program, we track each move for the next players move. This is quite complex when we start coding. I am sharing my simple code so that you can understand the game easily. So basically we create 3 files here or we can do all code in one file which includes all html, css and javascript.
So firstly we make a design or UI part then start work on its functionality. You can create this by using plain javascript.
So we load code on the loading of HTML document.
Before writing code, we also have to check what are the winning conditions.
Player 1 plays when the move is equal to 1, 3, 5, 7 and 9. Player 2 plays when the move is equal to 2, 4, 6 and 8. So, Player 1 plays when move is an odd number. Here we can write the logic this way, if ((count%2)==1), then it is player 1’s turn, otherwise it is player 2’s turn. When any player presses on a blank space, that respective player places either an X or O on the playing board.
In the code firstly we write the winning case scenarios at which numbers he/she can win the game. Then we make a function for each move player is playing, in the function we check that players wins or not by that move. We also make a function if no one wins the game then they can again play that game.
Here is code to make the game.
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8"/>
<title>Tic Tac Toe Game</title>
<style>
*{
box-sizing: border-box;
font-family: sans-serif;
}
body{
margin: 0;
padding: 0;
width: 100%;
height: 100vh;
display: flex;
justify-content: center;
align-items: center;
background-color: #BF360C;
}
.container{
width: 500px;
height: 500px;
display: grid;
background-color: #E64A19;
grid-gap: 5px;
grid-template-columns: 33% 33% 33%;
grid-auto-rows: 33% 33% 33%;
}
.card{
position: relative;
background-color: #BF360C;
cursor: pointer;
}
.card::before{
position: absolute;
top: 0; right: 0; bottom: 0; left: 0;
display: flex;
justify-content: center;
align-items: center;
font-weight: bold;
font-size: 8rem;
}
.card.x::before{
content: "X";
}
.card.o::before{
content: "O";
}
.winner{
display: flex;
flex-direction: column;
align-items: center;
justify-content: center;
position: fixed;
width: 400px;
height: 200px;
padding: 20px 40px;
background-color: #fff;
font-size: 2rem;
border-radius: 20px;
text-align: center;
animation: animate .5s linear;
}
@keyframes animate{
from{
opacity: 0;
}
to{
opacity: 1;
}
}
.winner button{
margin-top: 20px;
width: 80px;
height: 35px;
line-height: 35px;
padding: 0;
border: 0;
outline: 0;
border-radius: 20px;
cursor: pointer;
color: #fff;
background-color: #BF360C;
}
</style>
</head>
<body>
<div class="container">
<div class="card" data-index="1"></div>
<div class="card" data-index="2"></div>
<div class="card" data-index="3"></div>
<div class="card" data-index="4"></div>
<div class="card" data-index="5"></div>
<div class="card" data-index="6"></div>
<div class="card" data-index="7"></div>
<div class="card" data-index="8"></div>
<div class="card" data-index="9"></div>
</div>
</body>
<script>
const cards = Array.from(document.querySelectorAll(".card"));
const winner = [[1,2,3],[4,5,6],[7,8,9],[1,5,9],[3,5,7],[1,4,7],[2,5,8],[3,6,9]];
let firstPlayer = [], secondPlayer = [], count = 0;
/*******************************************************/
function check(array){
let finalResult = false;
for(let item of winner){
let res = item.every(val => array.indexOf(val) !== -1);
if(res){
finalResult = true;
break;
}
}
return finalResult;
}
/*******************************************************/
function winnerpleyr(p){
const modal = document.createElement("div");
const player = document.createTextNode(p);
const replay = document.createElement("button");
modal.classList.add("winner");
modal.appendChild(player);
replay.appendChild(document.createTextNode("Replay"));
// replay.setAttribute("onclick","rep();");
replay.onclick = function() { rep() };
modal.appendChild(replay);
document.body.appendChild(modal);
}
/*******************************************************/
function draw(){
if(this.classList == "card"){
count++;
if(count%2 !== 0){
this.classList.add("x");
firstPlayer.push(Number(this.dataset.index));
if(check(firstPlayer)){
winnerpleyr("Congrats player one you win");
return true;
}
} else{
this.classList.add("o");
secondPlayer.push(Number(this.dataset.index));
if(check(secondPlayer)){
winnerpleyr("Congrats player two you win");
return true;
}
}
if(count === 9){
winnerpleyr("Draw");
}
}
}
/*******************************************************/
function rep(){
const w = document.querySelector(".winner");
// cards.forEach(card => card.classList = "card");
firstPlayer = [];
secondPlayer = [];
count = 0;
w.remove();
[].forEach.call(cards, function(el) {
el.classList.remove("x");
el.classList.remove("o");
});
}
/*******************************************************/
cards.forEach(card => card.addEventListener("click", draw));
</script>
</html>
You can play the game given below to test how it works.
Comment down below if you have any queries related to above JavaScript Tic Tac Toe game.
The post JavaScript Tic Tac Toe Game appeared first on The Crazy Programmer.
ESET researchers describe the latest components used in a recent Sednit campaign
The post No summer vacations for Zebrocy appeared first on WeLiveSecurity
The online developer education site Thinkful turns out to be the latest victim of a cyber attack. As confessed by
Online Education Platform Thinkful Resets Passwords Following Security Breach on Latest Hacking News.
Researchers have discovered a security vulnerability in Harbor cloud native registry. As revealed, a critical bug existed in Harbor container
Critical Privilege Escalation Vulnerability Existed In Harbor Registry on Latest Hacking News.
Google Calendar is a wonderful feature by Google with regards to defining events. However, misconfiguring Google Calendar settings can reveal
Misconfiguring Google Calendar Reveals Calendar Events Publicly on Latest Hacking News.
After the Cambridge Analytica fiasco, Facebook started a thorough investigation and scrutiny of all applications. The goal was to single
Facebook Suspends ‘Tens Of Thousands’ Of Apps For Data Hoarding on Latest Hacking News.
In this tutorial we are going to discuss about Python NoneType. Before we start discussion on NoneType let us first see what is an object.
In any programming language preliminary data types are int, float, char etc. and we can create a class by mixing different data types together and the instances of these classes are called as object.
Take this for example:
class student(object):
roll = 5
stu = student()
print(stu.roll)
Here stu is and object of class student.
When stu = student() is executed an object is created but what if we want to create the object stu but does not want to assign any value.
Here we can use None keyword.
None is actually an object of the class NoneType. When we write
stu = None we are actually pointing to an object of the class NoneType which always have a special name None.
We can check the type of the object using type checking in python.
class student(object):
roll = 5
stu = student()
print(type(stu))
stu = None
print(type(stu))
The code above checks the class of stu before and after assigning None. The output is as below:
<class ‘__main__.student’>
<class ‘NoneType’>
At start stu belongs to student class but later it’s class is changed to NoneType.
One important thing to keep in mind is that there can be one and only one None object in your whole python code. Each object which is pointing to None will point to the same object.
stu = None print(id(stu)) teacher = None print(id(teacher))
id() is used to get the unique identifier assigned to objects in Python. As expected the above code will print the same value both of the times.
Output:
9918176
9918176
The value can be different than shown but it will print the same value for both of the statements.
What is the use of None?
None serves the purpose of NULL in other languages in Python.
How can we check if the given object is of type None?
The best way to check if the object is of type None is to use the is keyword.
class student(object):
roll = 5
stu = student()
print(stu is None) # Prints False
stu = None
print(stu is None) # Prints True.
== should not be used for checking the type of the object with None as PEP 8 explicitly states that “comparisons to singletons like None should always be done with is or is not, never the equality operators.”
Comment down below if you have any queries related to python nonetype.
The post Python NoneType appeared first on The Crazy Programmer.
A nationwide data leak is believed to affect almost all citizens of Ecuador, putting them at risk of identity theft
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
Phishing attacks do not always involve emails or web links. Sometimes, the attackers also leverage the SMS facility to trick
Police Warn Of Scammers Targeting Venmo Users Via Malicious SMS on Latest Hacking News.
The UK’s cybersecurity agency also outlines precautions that academia should take to mitigate risks
The post Universities warned to brace for cyberattacks appeared first on WeLiveSecurity
In the murky realm of hacking and jacking, cybercriminals are now using a primitive method for attacking users. Reportedly, researchers
Simjacker is Being Actively Exploited in The Wild To Steal Location Data on Latest Hacking News.

So, this morning you woke up with the idea to develop a way to store and label interesting articles you've read. After playing with the idea, you figure a Telegram chatbot is the most convenient solution for this problem.
In this guide, we'll walk you through everything you need to know to build your first Telegram chatbot using JavaScript and Node.js.
To get started, we have to register our new bot with the so-called Botfather to receive our API access token.
The first step towards our very own Telegram bot is registering the bot with the BotFather. The BotFather is a bot itself that makes your life much easier. It helps you with registering bots, changing the bot description, adding commands, and providing you with the API token for your bot.
The API token is the most important step, as this allows you to run the code that can perform tasks for the bot.
The BotFather can be found on Telegram by searching for 'BotFather'. Click on the official BotFather, indicated with the white checkmark icon in the blue circle.
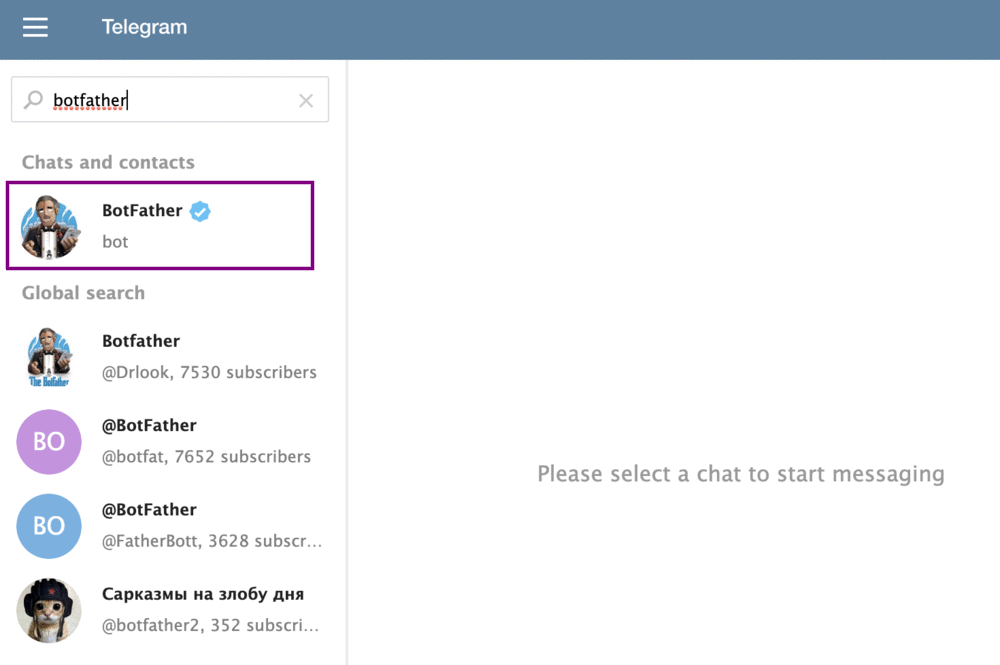
Now we've found BotFather, let’s talk to him! You can start the conversation by typing /newbot. BotFather will ask you to choose a name for your both. This name can be anything and doesn’t have to be unique. To keep things simple, I named my bot ArticleBot.
Next, you will be prompted to input a username for the bot. The username must be unique and end in bot. Therefore, I chose michiel_article_bot, as that username was not yet taken. This will also be the username you use for looking up the bot in Telegram's search field.
FatherBot will return a success message with your token to access the Telegram HTTP API. Make sure to store this token safely, and certainly don't share it with anyone else.
We can further modify the bot by adding a description or setting the commands we wish the bot to know. You can message the bot with the text /setcommands. It will show you how to input the commands with the format command1 - Description.
The post How to Build Your First Telegram Chatbot with Node.js appeared first on SitePoint.
In almost all tested units, the researchers achieved their goal of obtaining remote root-level access
The post Remote access flaws found in popular routers, NAS devices appeared first on WeLiveSecurity
BoomER is a Command-line interface python open-source framework fully developed in Python 3.X for post-exploitation of targets with the objective
BoomER | An Open Source Post-Exploitation Tool To Exploit Local Vulnerabilities on Latest Hacking News.
Researchers have spotted numerous vulnerabilities affecting Systems Applications and Products (SAP) web applications. The flaws for which are all critical
Team Swascan Discovered Critical Vulnerabilities In Numerous SAP Applications on Latest Hacking News.
Storing files in the cloud is more popular than ever. Whether it’s using iCloud for our Photos, OneNote for our MS Word documents, or Dropbox for large files, cloud computing has become an integral part of our professional and personal lives. These days, there’s no shortage of providers, but each has its own particular strengths and weaknesses. So be sure to pay attention to these key details when choosing which service you’re going to trust your data with.

Most of us think cloud servers are invincible. In reality, they can fail just as often if not even more frequently than our own. Cloud servers are under constant stress from high usage rates and often suffer from cyberattacks. And if your data is unavailable, it can create serious problems for you. So before you select a service, ask your provider about what their strategy for server failure is. Do they have redundancy servers? What are their reliability statistics? What can happen in the worst-case scenario?
Most of the major service providers will offer you a free-tier of data. For example, Google Drive offers everybody 15 gigabytes for free. While that might be fine for individual use, businesses need much more space than that. The major providers should be able to accommodate terabytes of storage, but make sure to check the pricing plans. And see if you can also easily upgrade to add capacity if your data storage needs to grow.
The whole purpose of cloud storage is to be able to access your data anywhere or anytime. The download speed will greatly impact your business. This is doubly true if you use cloud storage as a backup option and you need a system restore ASAP. If your provider has cap speeds on either downloads or uploads, it can severely hamper your needs. Ask about official speeds, but be sure to also check reviews to get the complete picture.
Hackers constantly attack cloud storage providers. Most utilize a variety of security tools, but you need to check what their data breach protocol is. Do they have a way to protect your data and maintain your anonymity? What happens if a DDoS attack occurs? Be sure to ask these and other questions and ensure that security is their top concern. You need to consider the physical layers of security as well as software tools like encryption and firewalls.
When it comes to cloud storage providers, the biggest difference is self-hosted cloud storage vs. proprietary companies like Dropbox and Google Drive. Major providers like Google Drive and Dropbox offer easy to use tools and are affordable with business plans starting from $9.99 per month. However, they also maintain data policies some users do not like. For example, they may reserve the right to access your data at any time or use your data for research or advertising purposes.
Self-hosted storage options have grown increasingly in popularity. OwnCloud is one of the services that has emerged over the last few years as a leading self-hosted cloud storage option. It offers a wide array of great features like automatic folder sync and very large file support. Another popular option is NextCloud, which is a feature-rich evolution of OwnCloud. NextCloud offers built-in voice and video chat, an office suite, and much more. Do note, however, that these companies share similar price points as their larger counterparts. The primary difference is built-in data protection policies that ensure user privacy.
Regardless of which cloud service you end up choosing, the most important thing you will need to do is file encryption. Providers like NordLocker encrypt and protect your files with the strongest AES-256 and other leading tech innovations. This means should hackers breach your cloud storage service; your files will still be safe. Not only that, NordLocker makes it simple for you to take advantage of additional features, like secure file sharing and other essential tools for cloud computing.
With so many options, choosing a cloud storage provider can be tricky. When you’re making a decision, make sure to focus on the essentials: speed, security, uptime, and data storage capacity. From here, your biggest decision will be whether to go with a major platform like Google or Dropbox or a self-hosted service. Regardless of what you select, however, you need to ensure you secure your files. And with NordLocker’s easy to use, highly secure software you can encrypt all of your cloud files in no time at all, allowing you to rest easy and know your files are safe.
The post Things You Have to Pay Attention to When Choosing a Cloud Storage Provider appeared first on The Crazy Programmer.
More malware has made it to the news that is aimed toward cryptocurrency. Dubbed as InnfiRAT, the malware resembles usual
InnfiRAT Malware Is All Set To Steal Cryptocurrency Wallet Information on Latest Hacking News.
The humongous collection of extensive personal details about millions of people could be a gold mine for scam artists
The post Nearly all of Ecuador’s citizens caught up in data leak appeared first on WeLiveSecurity
LastPass is a popular password manager that has earned credibility owing to its efficiency. Nonetheless, like any other software, it
LastPass Vulnerability Leaked Login Credentials – Update Now! on Latest Hacking News.
A researcher discovered a vulnerability in Uber API app that could allow an adversary to take over users’ accounts. Exploiting
Critical Vulnerability Discovered In The Uber App That Could Allow Account Takeovers on Latest Hacking News.
It would seem that Facebooks’ Instagram frequently makes it to the news due to its security glitches. Recently, a researcher
Instagram Flaw That Could Have Previously Exposed User Data Now Patched on Latest Hacking News.
After the launch of iOS 12, a researcher discovered back-to-back lock screen bypass flaws in the system exploiting various features.
An iOS 13 Bug Exposes Device Contacts While Exploiting FaceTime Call on Latest Hacking News.
Telegram is one of the most-trusted apps when it comes to private messaging. Therefore, any security or privacy bug arising
A Serious Privacy Bug In Telegram Could Allow Retrieval of Media From Deleted Messages on Latest Hacking News.