In the second blogpost of the two-part series we'll suggest handy tips to help enhance the security of your mobile devices
The post 20 tips for 2020: Be smarter with your smartphone appeared first on WeLiveSecurity
In the second blogpost of the two-part series we'll suggest handy tips to help enhance the security of your mobile devices
The post 20 tips for 2020: Be smarter with your smartphone appeared first on WeLiveSecurity
In this tutorial, I will tell you about how you can get URL parameters with javascript.
Passing URL parameters is a nice way to move from one page to another. As we know URL is string in which there are certain variables present which are used to move forward to the new page. You can get it by checking in URL string the text written after question mark shows the variable name, value pair follow separated by an ampersand.
The disadvantage of using this method is that it is visible to the user and anyone can manipulate it by manual editing. There are some other secure ways that we can do this is by using post method, session cookies, or database to store the variables.
Basically, for this, we have to understand how it is passed.
There are various ways buy which we can fetch the parameters from url, lets have a look on them one by one.
First way is by using searchParams javascript method. This method is used to get value of particular variable.
var link = "http://www.steadyadvice.net/t.html?stack=hello&pop=data&link=hello";
var extractParameter= new URL(link);
var final = extractParameter.searchParams.get("link");
console.log(final);
You can get the current link by using window.location.href, just replace link variable string with this method.
Another way is by using split method.
var urlLink = 'http://www.steadyadvice.net/t.html?stack=hello&pop=data&link=hello';
var query_paramter = urlLink.split("?")[1];
console.log(query_paramter);
The third way is by using the regular expression.
function getUrlVars( name, link ) {
if (!link) link = location.href;
name = name.replace(/[\[]/,"\\\[").replace(/[\]]/,"\\\]");
var regexS = "[\\?&]"+name+"=([^&#]*)";
var regex = new RegExp( regexS );
var results = regex.exec( url );
return results == null ? 'Empty' : results[1];
}
console.log(getUrlVars('text', 'steadyadvice.net/?a=11&txt=world'));
In this method, I also handled that if at some instance parameter is missing then it returns undefined which is a bad coding practice. So to correct this we first check that particular parameter is present or not. If not present then send some default value.
So there are some characters that can not pass through URL like suppose we write a space in the link and press enter key then space will be replaced by %20code. So it is also important to encode and decode the URL parameters. There are the following functions you can use to do this. In these functions, you have to pass URL string.
To decode use decodeURI(urlValue) and to encode use encodeURI(urlValue).
Comment down below if you know any other way to fetch url parameters in javascript.
The post JavaScript Get URL Parameters appeared first on The Crazy Programmer.
Ransomware attacks continue to cripple different businesses, one more victim has now become apparent. Recently, a telemarketing firm The Heritage
The Heritage Company Went Down After Ransomware Attack on Latest Hacking News.
In this first instalment of the two-article series we will be looking at cybersecurity habits to avoid when using your computing devices
The post 20 tips for 2020: Mistakes to avoid appeared first on WeLiveSecurity
One of the largest public accounting firms in the United States, Moss Adams, has suffered a data breach. The firm
US Accounting Firm Moss Adams Discloses Data Breach on Latest Hacking News.
Popular American radio network Entercom has recently disclosed a cyber attack. While it didn’t cause severe damages, it marks the
Entercom Radio Suffered Outage After Cyber Attack on Latest Hacking News.
The popular chat app in the Middle East is currently in hot waters. According to recent investigations, the app has
Popular Messaging App In UAE ‘ToTok’ Deemed To Be a Government Spy Tool on Latest Hacking News.
Twitter for Android app had another bug that exposed users’ phone numbers. By exploiting the vulnerability, a researcher succeeded in matching
Twitter For Android App Bug Allowed Matching 17 Million Twitter Accounts With Phone Numbers on Latest Hacking News.
NVIDIA have recently fixed a serious vulnerability in GeForce Experience (GFE). Exploiting the flaw could have allowed an attacker to
NVIDIA Release A Fix For Serious GeForce Experience Vulnerability on Latest Hacking News.
Google’s decision to truncate website URLs by hiding the ‘www’ in its Chrome browser troubled many users. Being the most
Create Custom Extension To Bring Back ‘www’ in Google Chrome Browser on Latest Hacking News.
A researcher has discovered a critical vulnerability in Citrix products that risked thousands of businesses around the world. Exploiting the
Critical Vulnerability In Citrix Could Affect Numerous Enterprises on Latest Hacking News.
Twitter has disclosed a vulnerability that potentially threatened Android users. As revealed, the Twitter for Android app had a flaw
Twitter For Android App Flaw Could Have Allowed Hijacking of Accounts on Latest Hacking News.
Cybercriminals seemed to have stepped up on a malicious campaign in the previous week. Reportedly, three different e-commerce stores in
Three Different US Stores Report POS Malware Attacks In The Same Week on Latest Hacking News.
According to 77% of the IT professionals recently surveyed by Entrust Datacard, if left unchecked, shadow IT will be a
5 Ways to Minimize Your Company’s Exposure to the Dangers of Shadow IT on Latest Hacking News.
As a vital mobile tool, Android phone usually stores a mass of files of our work and life, such as
How to Backup and Restore Android with Coolmuster Android Assistant [Can’t Miss] on Latest Hacking News.
Did you know that a hacker tries to steal someone’s information every 39 seconds? Browsing the internet can be a
How to Safeguard Your Information While Surfing Online on Latest Hacking News.
Every device that we own that connects us with the digital world has a system within it that helps connect
Integrate Linux Software with Your IOS Devices on Latest Hacking News.
Continuing with their policies to ensure user privacy, Mozilla removed the Avast and AVG browser extensions from their listings. The
Mozilla Restored Avast, AVG Browser Extensions To Add-Ons Store After Original Ban on Latest Hacking News.
Facebook has once again made it to the news owing to a security issue. However, this time, Facebook isn’t directly
267 Million Facebook Users’ Data Exposed Online Via Unsecured Database on Latest Hacking News.
It’s not a stretch to surmise that the incident was enabled by poor security settings
The post Prison surveillance footage posted on YouTube appeared first on WeLiveSecurity
An operating system is the heart of any computer without which it cannot withstand. It provides all the resources to software, manages the hardware, and implements all standard services for computer programs. In this article, we are going to discuss the advantages and disadvantages of an operating system. So let’s get started with the basics.
An operating system is a software that controls all the working of computer architecture, including hardware, peripheral devices, and all other components. It takes input from the user, processes the data, and generates output for the same. Besides, it also acts as an interface between the hardware of the system and the user. Moreover, an operating system is designed to perform various tasks such as processing information, arithmetic calculations, task scheduling, memory allocation, and deallocation, etc.
Also Read: Difference between DOS and Windows Operating System

There are different types of operating systems that have been transformed over time. As each operating system has its benefits and downsides, that’s the reason new operating systems have been developing. Now let’s look at the following advantages and disadvantages of an operating system.
Computing Source
An operating system acts as an interface between the user and the hardware. It allows users to input data, process it, and access the output. Besides, through the operating system, users can communicate with computers to perform various functions such as arithmetic calculations and other significant tasks.
User-Friendly Interface
Windows operating system, when it came into existence, also introduces Graphical User Interface (GUI), which made using computers much more natural than earlier Command Line Interface. Moreover, users can quickly understand, interacts, and communicate with computer machines.
Resource Sharing
Operating systems allow the sharing of data and useful information with other users via Printers, Modems, Players, and Fax Machines. Besides, a single user can share the same data with multiple users at the corresponding time via mails. Also, various apps, images, and media files can be transferred from PC to other devices with the help of an operating system.
No Coding Lines
With the invention of GUI, operating systems allow accessing hardware without writing programs. Unlike, earlier users don’t have to write code of lines to access the hardware functionality of a computer system.
Safeguard of Data
There’s a lot of user data stored on the computer, and that can only be accessed with the help of an OS. Besides, storing and accessing the data, another important task of an OS is to safely and securely manage the data. For example, Windows Defender in Microsoft Windows detects malicious and harmful files and removes them. Also, it secures your data by storing them with a bit to bit encryption.
Software Update
An operating system is a software which needs to update regularly to control high fleeting features that are continually increasing. With other apps and software hitting updates to improve their functionality, OS must improve their benchmarks and handle all the working of a computer. An OS can easily be updated without any complexity.
Multitasking
An operating system can handle several tasks simultaneously. It allows users to carry out different tasks at the same point in time.
Other Advantages
Expensive
When compared to the open-source platforms like Linux, some operating systems are costly. While users can use a free OS but generally they are a bit difficult to run than others. Moreover, operating systems such as Microsoft Windows with GUI functionality and other in-built features carry a costly price tag.
System Failure
If the central operating system fails, it will affect the whole system, and the computer will not work. Moreover, an OS is the heart of a computer system without which it cannot function. If the central system crashes, the whole communication will be halted, and there will be no further processing of data.
Highly Complex
Operating systems are highly complex, and the language which used to establish these OS are not clear and well defined. Besides, if there’s an issue with OS users cannot directly understand, and it cannot be resolved quickly.
Virus Threats
Threats to the operating systems are higher as they are open to such virus attacks. Many users download malicious software packages on their system which halts the functioning of OS and slow it down.
Fragmentation
Fragmentation in the computer is a state when storage memory breaks into pieces. Internal fragmentation occurs when the method of process is larger than the memory size. External fragmentation occurs when the method or process eliminates.
So, these are the following advantages and disadvantages of the operating system. If you have any other queries or related doubt, then please let us know in the comment box below.
The post Advantages and Disadvantages of Operating System appeared first on The Crazy Programmer.
Disposing of old tech isn’t a one-click solution; there are multiple things you have to consider before moving on to greener pastures
The post How to get rid of your old devices safely appeared first on WeLiveSecurity
Strong apps can do a lot for businesses of all kinds. If a business has a rock-solid app accessible to its customers, then it may achieve a lot. If it has an app that’s difficult to navigate and utilize, then it may flounder and fade. It doesn’t matter if you’re an app developer or if you’re simply an entrepreneur who is in charge of a driven business. You should take the time to learn all that you can about the wonders of mobile-first design.
This kind of design can make building custom apps streamlined and simple. If you want to be in the loop with regard to all of the latest mobile app trends, then you need to grasp mobile-first design well. It has accomplished a lot for professionals who are part of the custom app development sector.
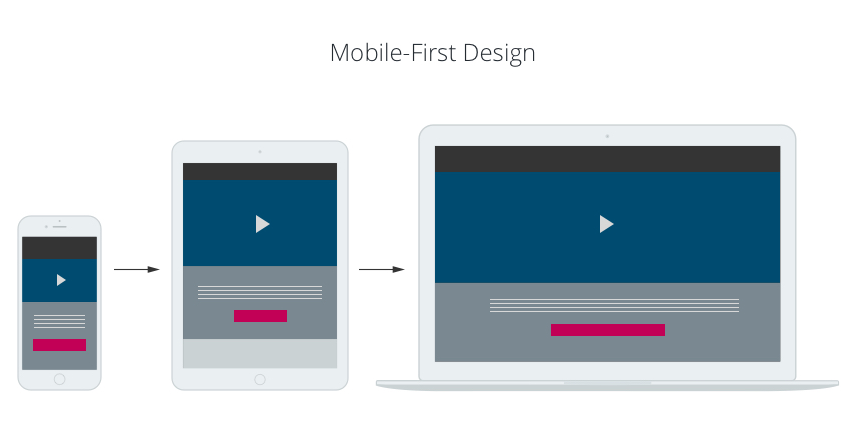
Mobile-first design, in short, revolves around concepts such as responsive web design. Professionals who participate in this approach initiate design elements with mobile users on their brains. Mobile users generally have higher numbers of boundaries in place. After professionals concentrate on mobile users, they grow things by zeroing in on the desktop computer or tablet crowd. “Mobile first” design is exactly what it seems to be.
Businesses can get a lot out of relying on mobile-first strategies. That’s due to the reality that people generally rely on their mobile devices more than anything else. If an individual is surfing the Internet, there’s a strong chance that she’s using her mobile device. There’s also a strong chance that she’s nowhere near a desktop computer of any sort. Proof of this is out there, too. At the beginning of 2012, consumers purchased more smartphones than they did PCs or “personal computers.” This impressive rise in popularity confirms one thing for developers and company owners alike. It confirms that people need to stress the undeniable power of the mobile realm. Mobile-first is a product design concept that’s becoming more and more relevant by the day.
People who depend on mobile-first design techniques can take advantage of responsive website responsive website. This design approach essentially guarantees that sites are going to be 100 percent responsive. That’s how it basically guarantees that consumers are going to be able to get to it via all kinds of devices. Examples include everything from cellphones to desktop computers. If you don’t want to leave anyone out in the establishment of your app or anything else, then it can help you considerably to take the mobile-first approach no matter what.
Mobile-first design is fascinating due to the fact that it streamlines details in a big way. That’s how it gives the members of the general public details that are simple to process within their minds. If you don’t want to overwhelm all of the members of your target audience, then taking the mobile-first design path may be right up your alley.
“User Experience” or simply “UX” is anything and everything in the current digital marketing world. It doesn’t matter if you’re designing an app, an extensive website or anything else similar. You need to put a lot of time and energy into the user experience.
If you want the people who take the time to visit your site or utilize your app to have superb experiences, then the mobile-first design can aid you. It can be a total headache to visit a site that’s terrific via standard computers only to realize that it’s a mobile nightmare. If you attempt to assess a site or a map via your cellphone or anything else, then you should review how simple things are. If things seem bewildering or unreasonable, then that may be a design pitfall. Thankfully, mobile-first design often eliminates that pitfall for people.
Outstanding conversion rates mean so much in the modern marketing world. If you want to get your hands on conversion rates that are better than ever, then you better think about mobile-first design. Conversion rates via mobile are a lot more impressive than the ones that are associated with their basic desktop counterparts are. Well-known search engines like Google handle their rankings via certain criteria. Google assesses websites by evaluating how simple they are for people who depend on mobile devices.
Mobile-first design is an approach that legitimately motivates people to zero in on transparency. That’s because this design does away with any and all pointless elements that relate to User Interface (UI) aesthetics and appearances. If you get rid of any and all possible interferences, then you’ll without a doubt get on the path to a User Experience that’s superior in caliber. This can achieve a lot for businesses that are committed to soaring.
It isn’t at all unusual for businesses to lose sight of the things that genuinely matter and offer value. They in many cases cannot see the “forest for the trees.” If you want to introduce an app that’s sure to be a hit, then you need to stress the power of unrivaled content. Mobile-first design is all about intriguing content, nothing more and nothing less. Mobile-first design empowers entrepreneurs and developers who are trying to provide target audience members with content that’s crucial. Mobile-first design gives developers no choice but to provide people with favorable and rare content.
It’s fine if you don’t know how to take a mobile-first approach all by yourself. If you’re trying to get the assistance that relates to building custom apps, there are many others who know exactly how you feel. These people go the extra mile to learn all that they can about the newest mobile app trends. They put a lot of thought into custom app development practices that are particularly effective and contemporary. Why exactly is the mobile-first design strategy so indispensable for individuals who want to develop their apps well? It’s indispensable due to the fact that it can lead to the emergence of many thrilling opportunities and pathways.
Mobile-first design isn’t anything that’s rare or elusive at all nowadays. If you want to reap the rewards of this app design concept, then you need to study up on all of the finest digital marketing companies that are around you. Professionals make it easy to master mobile-first design. That’s largely because there are so many people these days who are essentially mobile experience gurus.
It’s not at all difficult to come across contemporary companies that manage mobile-first design. If you’re eager to put together an app that makes mobile users everywhere a number one priority, then you need to look into the mobile-first design division. You should learn all about companies that offer mobile-first design guidance.
The post Mobile-First Design: Why It’s The Only Way to Develop Your App appeared first on The Crazy Programmer.
What are some of the key things you should do with your shiny new device as soon as you unbox it?
The post How to secure your digital Christmas presents appeared first on WeLiveSecurity
The extensively marketed Ring smart devices are once again in hot water. Recently, numerous reports have surfaced online highlighting several
Hackers Continue to Dump Weak Ring Doorbell Credentials Online on Latest Hacking News.
Researchers have uncovered a new malware campaign which they dub the “Hornets Nest”. What makes this attack notable is the
Researchers Uncovered Malware That Drops Six Variants in One Hit on Latest Hacking News.
Google has announced updates to its existing Patch Reward Program. Beginning in 2020, Google will provide upfront financial support to
Google Jazzes Up Its Patch Reward Program With Upfront Financial Support on Latest Hacking News.
Another cyberattack on the healthcare sector has put the privacy of millions of users at risk. Recently, a Canadian healthcare
LifeLabs Disclosed Data Breach Impacting 15 Million Customers on Latest Hacking News.
Not much time has passed since Google launched its Chrome browser version 79 with improved privacy and security features. However,
Update For Google Chrome 79 On Android Removed Due To Bug That Caused Data Loss on Latest Hacking News.
ESET's free BlueKeep vulnerability checker – Dangerous PayPal-themed scam – This year's worst passwords
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
Undoubtedly, Silicon Valley has always been top-notch in leading the cutting-edge tech startups with escalating growth rates. There’s no denying about Silicon Valley as the prime spot for access to talented professionals, driving innovations, and efficient working culture. The Southern Bay area of California is the Hubspot for large companies, including Google, Apple, Microsoft, and Facebook.
Despite the rule of such gigantic organizations and high operational costs of the Bay area, it offers excellent opportunities for tech startups with unique technological solutions. Many tech startups have made their name and raised a large amount of revenue in Silicon Valley.
Tech startups in the field of software development, web development, and mobile app development is increasing day by day. Entrepreneurs and tech-savvy individuals who are passionate about technology, who possess creative interpersonal skills, and who think out of the box are generally found in this place.
While, on the other hand, many startups outside the location try to get their footprints in the Silicon Valley region as the success rate here is impeccable. The population of the area is expanding rapidly, with a high increase in the standard cost of living. Further, making this place highly expensive both in terms of living and development costs and thus entailing more and more dev work outsourced.
However, for the past few months, there’s a downfall in the percentage of total California funding; still, the Bay area is leading the tech startups with a high success rate.
Check the latest news by Crunchbase:
“Of course, less is relative. A Crunchbase News tally of reported funding rounds for startups in the core Silicon Valley counties of Santa Clara and San Mateo finds that companies there have pulled in more than $15.4 billion so far this year. That’s a huge sum and is roughly on pace with 2018 funding levels.”
![]()
Now, if you’re clear with the Bay area’s startup venture success rate, let’s have a look at the best Silicon Valley startups.
Here we present you to the list of 5 best Silicon Valley startups that have significant growth potential and are expected to rise ahead shortly.

Ripe.io is the blockchain of food that uses the Internet of Things (IoT) and Blockchain technology in the food supply chain. This tool helps in building trust and confidence by providing access to transparent and reliable information on the origin, journey, and quality of food. This Silicon Valley startup is on a mission for transforming the food supply chain into digital working that brings transparency, security, and better food for everyone.
The software provides services including tracking and visibility of supply chain, aggregation and sharing of secure data, trust verification, and brand quality; IoT integration; sensors; and scalable blockchain. Further, they provide solutions for each participant in the food supply chain. The software also lets users track and trace the food from either the dashboard with real-time data insights or through a mobile app.
ImpactVision is a tool that helps users to determine food quality through Hyperspectral technology with Machine Learning and imaging technology. The tool provides real-time and non-invasive information about the food quality that reduces the risk as well as prevent waste. Further, ImpactVision increase revenue by delivering superior product quality, reducing food loss through optimized sorting and distribution, and prevent product recalls due to foreign object contamination.
The software enables the food industry firms to shift from manual processing of visual inspections and firmness tests to an automated system for quality control — moreover, increasing customer satisfaction, brand loyalty, and product consistency.
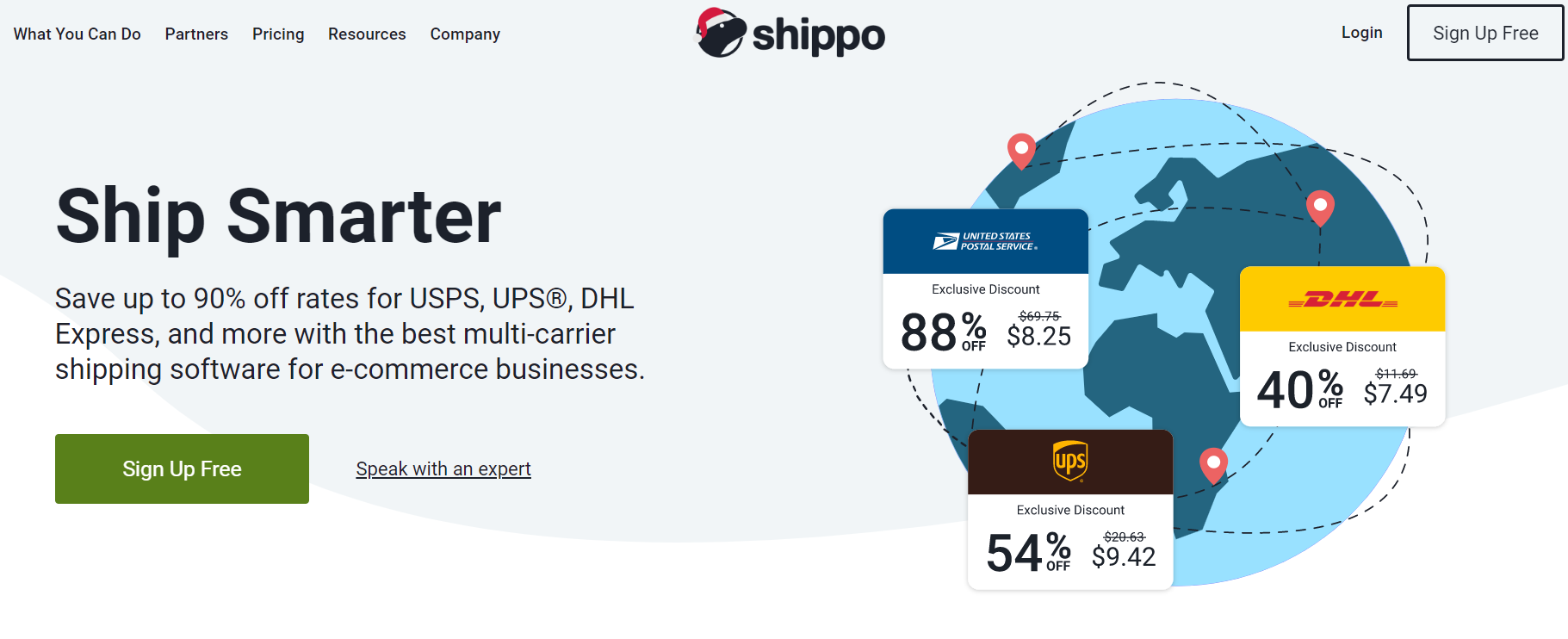
Shippo is the new and smarter way for shipping that allows merchants to save time and money with cloud-based shipping software. The tool is an automated system that lets users connect their store, create discounted shipping labels, streamline returns, track shipments, and notify customers. This easy to use and intuitive software allows users to automatically sync all their sales channels and manage all orders in one place.
Besides, this Silicon Valley startup is supporting large companies like Shopify, WooCommerce, Magento, Weebly, eBay, Fedex, and many more. Additionally, the multi-carrier shipping software provides 90 percent potential savings on shipping labels. The platform has 77 percent avg YoY growth for shippo brands and is trusted by more than 35,000 brands.
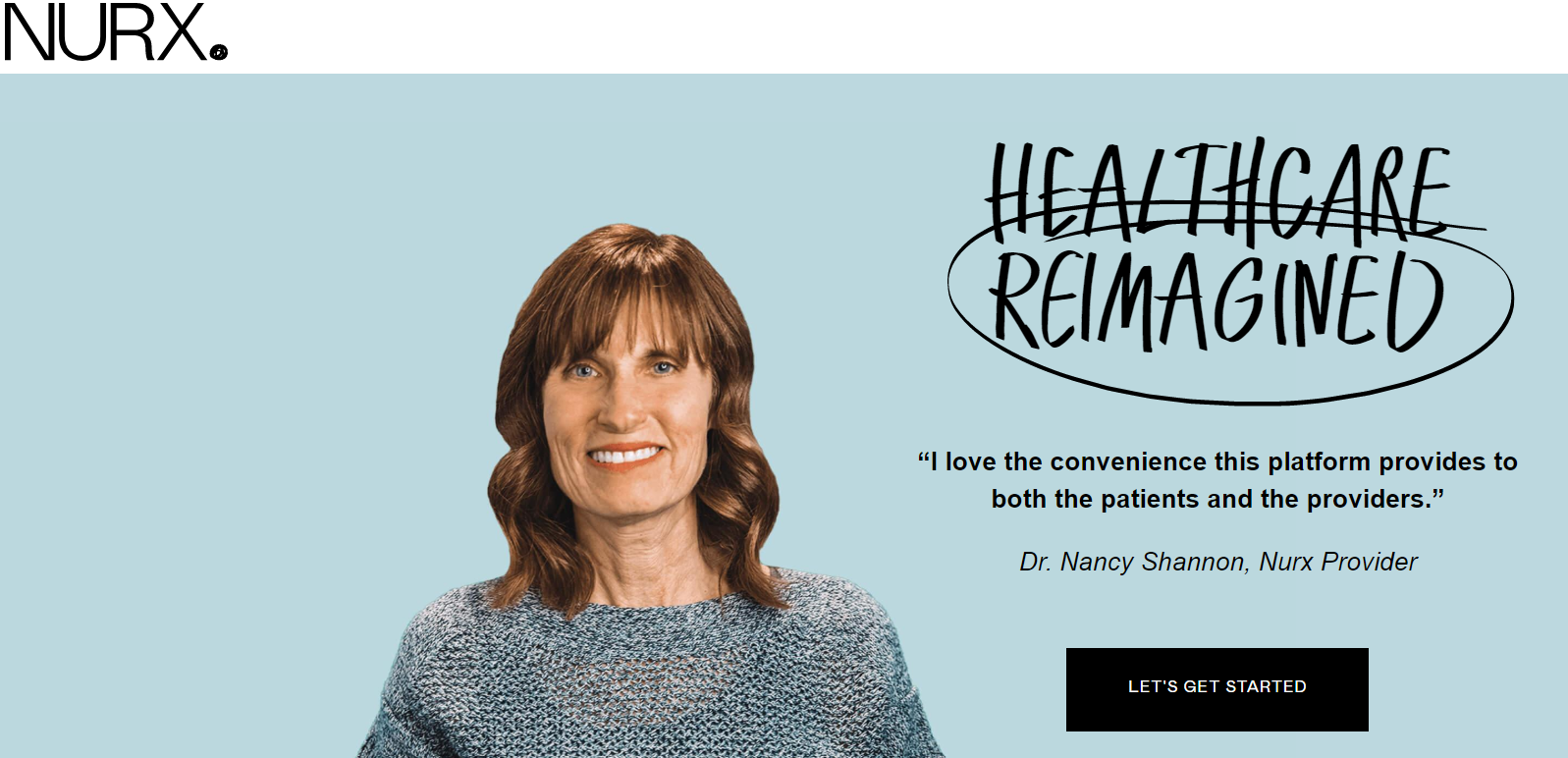
Nurx is one of the fastest-growing startups in Silicon Valley that provides easy access for women to birth control. The platform also provides a dedicated easy to use digital application that helps in improving women’s access to birth control. Nurx has an aim to accommodate easy and affordable healthcare by catering to real doctors and real care to its users. Further, patients can directly get their prescriptions and home testing kits on their doorstep through the digital application.
Currently, the service is available in 15 different states of the USA, and sooner the expansion is expected. Moreover, Nurx provides free birth control for users with health insurance. For users without health insurance, medication costs start at $15 per month. Apart from birth control, Nurx also provide different healthcare services such as STI Testing, Emergency Contraception, HIV Prep, and HPV Screening
Gladly provides radically personal customer service and enables businesses to create a personalized customer experience. Watch out this video above how Gladly enhances customers and helps in building long-lasting relationships. The software helps every sector from marketing and finance to retail and travel, making highly personalized customer experience and connections with customers. The tool helps in targeting customers by providing all the relevant information quickly and efficiently.
The software supports many large companies, including Porsche, Joann, Sonder, BlackBird, Tumi, Hyatt, and many others. Moreover, Glady empowers agents to communicate with customers across channels, making them feel more secure with public information.
So, these are some of the best Silicon Valley startups that are expected to be the future scope. Yet, there are a lot of innovations and improvements still to explore. The idea behind these startups and the dedication of human resources have made these startups successful in growing and leveraging their potential. As we already know, Silicon Valley is the prime spot that enhances startups with out of the box ideas and creativity. If you have any such plan, you know where to start from, and nothing beats Silicon Valley in this respect.
The post The 5 Best Silicon Valley Startups of 2019 appeared first on The Crazy Programmer.
An ongoing phishing scam uncovered by ESET researchers seeks to wreak havoc on your money and digital life in one fell swoop
The post Ambitious scam wants far more than just PayPal logins appeared first on WeLiveSecurity
Malware and legal requirements force academics and students to join a near-endless line in order to pick up their passwords
The post 38,000 people forced to pick up email passwords in person appeared first on WeLiveSecurity

This article on how to remove a background in Photoshop remains one of our most popular posts and was updated in 2019 for Adobe Photoshop 2020.
Photoshop offers many different techniques for removing a background from an image. For simple backgrounds, using the standard magic wand tool to select and delete the background may well be more than adequate. For more complicated backgrounds, you might use the Background Eraser tool.
The Background Eraser tool samples the color at the center of the brush and then deletes pixels of a similar color as you "paint". The tool isn’t too difficult to get the hang of. Let me show you how it works.
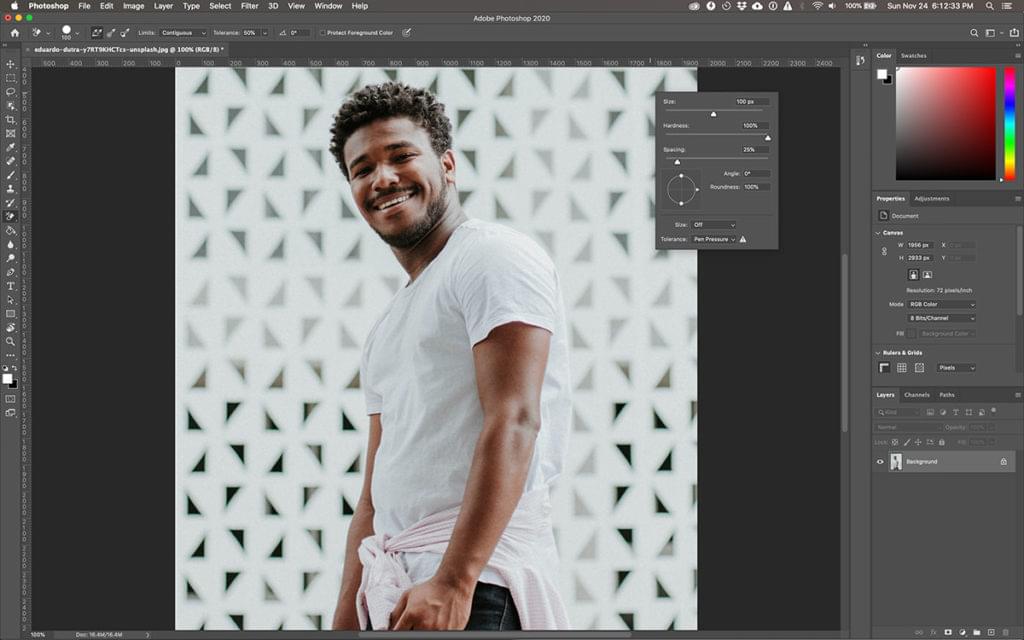
Start by grabbing an image that you want to remove the background from. I'll be using the image below, as it features areas that range from easy removal through to more challenging spots. I snagged this one for free from Unsplash.

Now let's open it in Photoshop.
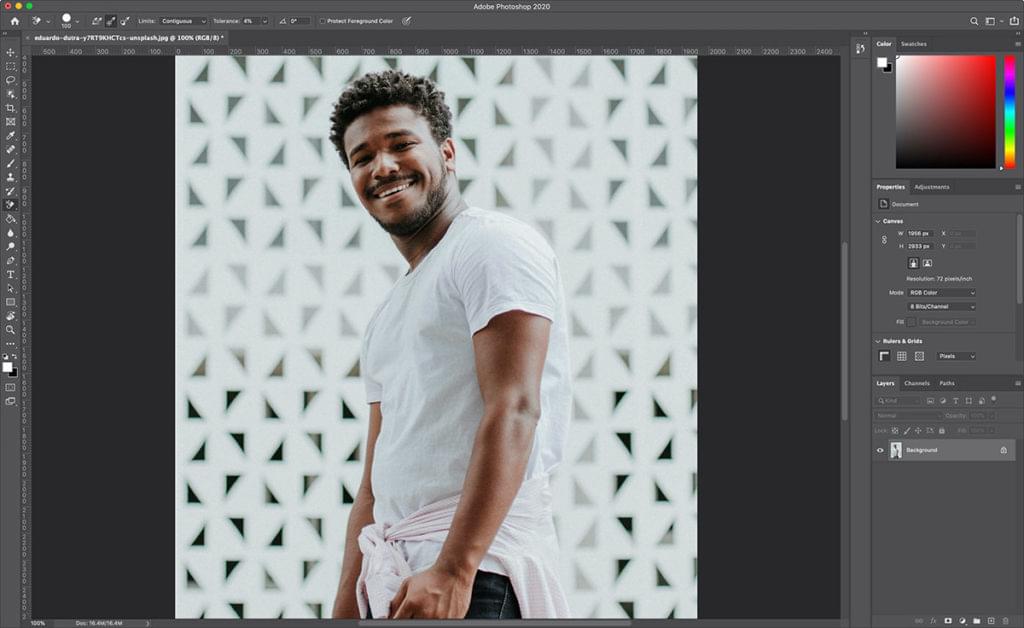
Select the Background Eraser tool from the Photoshop toolbox. It may be hidden beneath the Eraser tool. If it is, simply click and hold the Eraser tool to reveal it. Alternatively, you can press Shift + E to cycle through all the eraser tools to get to the Background Eraser. If you had the default Eraser tool selected, press Shift + E twice to select the Background Eraser Tool.
On the tool options bar at the top of the screen, select a round, hard brush. The most appropriate brush size will vary depending on the image you're working on. Use the square bracket key ([ or ]) for quickly scaling your brush size.
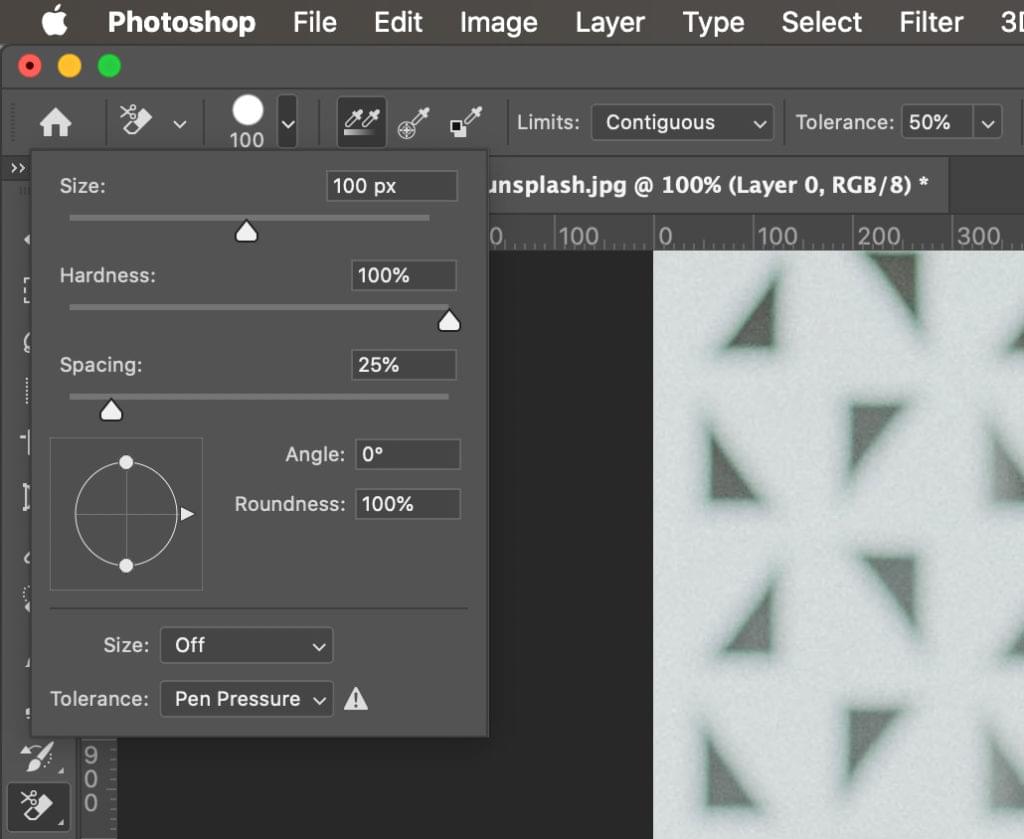
Alternatively, you can right-click your mouse anywhere on the artboard to change the size and hardness of your brush too.
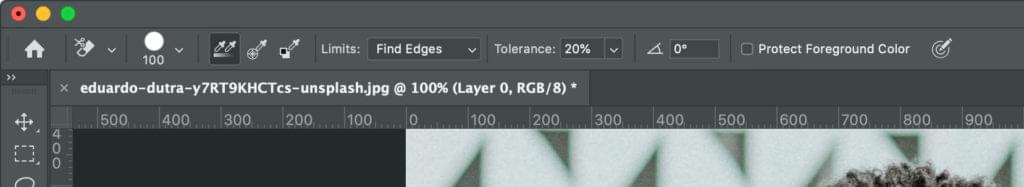
Next, on the tool options bar, make sure Sampling is set to Continuous (it’s the first of the three icons), the Limits to Find Edges* and the *Tolerance has a range of 20-25%.
Note: a lower tolerance means the eraser will pick up on fewer color variations. While a higher tolerance expands the range of colors your eraser will select.
Bring your brush over your background and begin to erase. You should see a brush-sized circle with small crosshairs in the center. The crosshairs show the "hotspot" and delete that color wherever it appears inside the brush area. It also performs smart color extraction at the edges of any foreground objects to remove “color halos” that might otherwise be visible if the foreground object is overlaid onto another background.
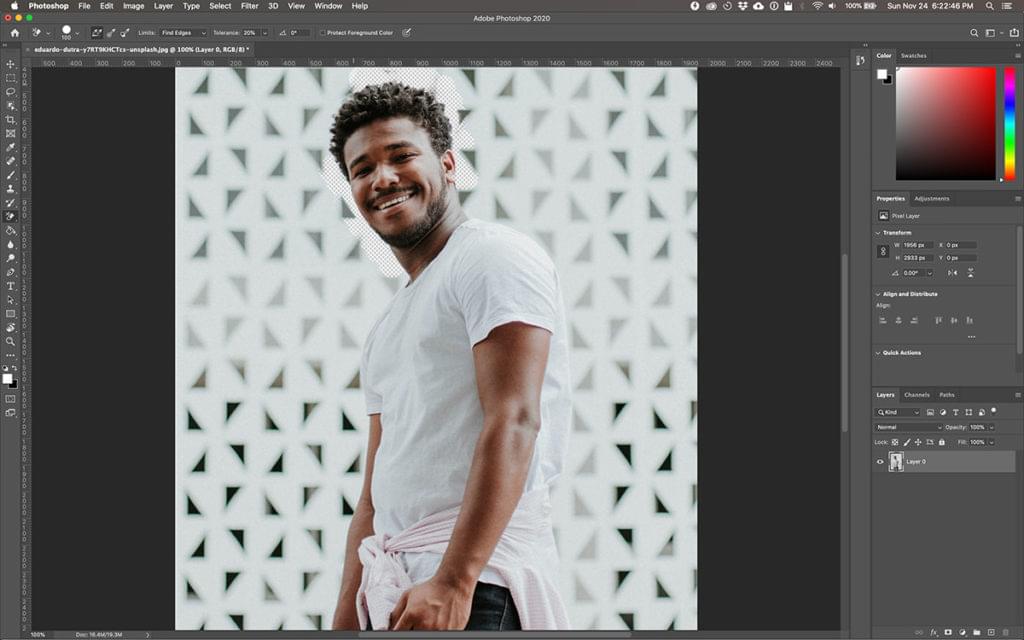
When erasing, zoom up your work area and try to keep the crosshairs from overlapping on the edge of your foreground. It's likely that you’ll need to reduce the size of the brush in some places to ensure that you don't accidentally erase part of your foreground subject.
The post How to Quickly and Easily Remove a Background in Photoshop appeared first on SitePoint.
WhatsApp, once again, marginally escaped a serious security threat. As revealed, a WhatsApp vulnerability allowed an attacker to crash the
WhatsApp Vulnerability Allows For an Attacker to Crash The App and Delete Group Chats on Latest Hacking News.
Sending phishing emails remains one of the most common and effective ways for cybercriminals to steal your business’ data and
How Automated Phishing Training Can Empower Your Employees to Protect Your Business on Latest Hacking News.
A serious security bug affected numerous TP-Link routers. The vulnerability in TP-Link Archer routers could allow a potential attacker to
Buffer Overflow Exploit Discovered That Overwrites Admin Password of TP-Link Archer Routers on Latest Hacking News.
The City of New Orleans has emerged as the latest victim ransomware attack. The attack caused the city websites to
The City Of New Orleans Suffered Ryuk Ransomware Attack on Latest Hacking News.
Brute-force attacks and BlueKeep exploits usurp convenience of direct RDP connections; ESET releases a tool to test your Windows machines for vulnerable versions
The post It’s time to disconnect RDP from the internet appeared first on WeLiveSecurity

"Jerry wouldn't let me go to the emergency room."
Jenny010137 recounted her story on Reddit. She had a major health crisis, but Jerry, her boss, wasn't buying it.
Jerry wouldn't let me go to the emergency room after the heavy vaginal bleeding I had been experiencing suddenly got way worse. I went over his head and got permission to go. I called my mom, told her to meet me in the ER. The ER nurse said he'd never seen so much blood. An ER nurse said this. It's determined I need a couple of blood transfusions and will be admitted.
Jenny's mom calls Jerry on her behalf.
My mom calls Jerry, who then proceeds to tell her that it's just stress, and I NEED TO GET BACK TO WORK. At this point, I couldn't even lift my own head up, but sure, I can take a bus across town and go back to work.
Doctors told Jenny they found a large growth that needed a biopsy.
They found a large growth that needed a biopsy. Jerry kept insisting that it couldn't be cancer because I'd be tired and losing weight. I had lost eight pounds in a week and went to bed the minute I got home. I was still recovering from the procedure when Jerry called me to let me know I was fired for taking too much time off. Five days later, I was diagnosed with cancer. Fuck you, Jerry. Fuck you.
Think about that for a second.
Jenny is losing blood rapidly. There's a good chance she's dying. Her boss can't be bothered to verify that she's okay. While she's in the hospital fighting for her life, he fires her for taking "too much time off."
This situation is obviously one to walk away from.
But it's not always so clear cut.
Sometimes you're in a situation where there are both positive and negative aspects of the job. With situations like these, the decision isn't always as obvious as we'd like it to be. Walk away from a promising position prematurely and you may burn bridges and destroy any goodwill you've built up.
What's the best way to know?
If you focus on the signs, you may be right, but too much uncertainty means you may handle things in a way that's less than ideal.
There's a better way.
Focus your attention on the right set of principles and you'll have the framework you need to decide when it's time to quit your job (or not). Let's take a look at these principles.
Art Markman, professor of psychology at the University of Texas at Austin, shared a story relayed to him by a reader.
My mother suddenly passed away on a Friday evening. On the Sunday my boss showed up to my house with groceries and flowers and suggested that I go into the office on Monday for the quarterly meeting. After all, "this was a pivotal time" for the business.
I didn't go in the next day because of my overwhelming grief. I later found out that I was to receive an award on that Monday. Was this a career-limiting move, or is my boss not clear on boundaries?
This boss meant well, but his concern was self-serving and not at all in the best interests of his employee. What's worse, he may not have understood why it was a problem if his employee spoke to him about it later on.
This is why you need boundaries.
Boundaries act as gatekeepers in a variety of professional, emotional, social, physical and situations. Here's why you need boundaries and why they're so important:
How do you set great boundaries?
It's a simple process. First, determine what you do and don't want. Next, figure out what your employer wants or doesn't want.
Sounds simple, right?
Figuring out what you want is really about asking the right question (see above). Figuring out what your employer wants is really about identifying criteria that are documented in some way. That's important, because it gives you the leverage you need to protect yourself (legally) against any inappropriate behavior.
But setting boundaries is risky.
Consider this common idea: Tell your boss No and you could get fired (or worse). If developers are smart, they'll avoid biting the hand that feeds them.
This rationale is trash.
If you set a boundary, it will be tested. Those around you — your manager, co-workers, other developers — will attempt to back you into a corner. You're going to have to find appropriate ways to rise to the challenge and enforce your boundaries.
Why go to the trouble? Because boundaries limit the damage from the other four principles discussed in this article. If you don't have strong boundaries, you'll face the problems discussed here. It doesn't matter if you're employed or you own your own business.
If you have poor boundaries, you won't be able to achieve your goals.
Reddit user YellowRoses had goals until their boss torpedoed those goals.
How do you deal with feeling disrespected by your boss? from r/careerguidance
They were promised a promotion. They negotiated with their boss and earned a verbal agreement regarding their promotion, only for said promotion to be denied with an "Oh, that's not happening now." No explanation or attempts at justifying the rescinded promise.
What if your employer isn't aware of your goals? Still doesn't matter. If you have a specific goal in mind, you're responsible for that goal. Not your co-workers, employer, or family members. Are you pushing for the director's position that's opened up? Prefer to stay in your current role but receive the same pay as managers? It's on you.
This seems obvious, until you realize most people wait to be chosen. They wait for someone to approve of their audition, accept them, recruit them, promote them, extend a helping hand, etc. Which goes nowhere fast.
To be clear, it's generally a good idea to discuss your goals with your employer, provided that you're in a good place to do so. If your employer laughs at you, mocks your goal, or decides they're unwilling to help you meet said goals, it's on you to make it happen.
The post 5 Signs It’s Time to Quit Your Job appeared first on SitePoint.
These passwords may win the popularity contest but lose flat out in security
The post The worst passwords of 2019: Did yours make the list? appeared first on WeLiveSecurity
Lossy and lossless compression are two kinds of data compression techniques. Here in this article, you will get to learn about what is lossy and lossless compression, their differences, and uses.
So, let’s start with the basics.
Data compression is the process of diminishing the storage size of any data or file so that it consumes less space on the disk. It is the technique of modifying, restructuring, encoding and converting the schema or instance of any data to reduce its size.
In simple words, it is converting the file in such a way that its size is reduced to a maximum extent. Data compressions is also known as bit-rate reduction or source coding.
Check the diagram below:
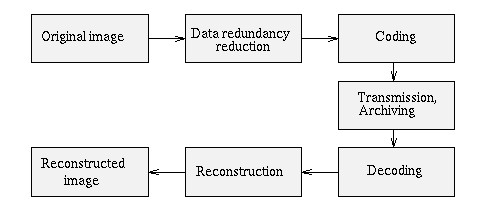
An example of an image that is converted or compressed to reduce its size without losing the ability to reconstruct the image.
Now, the question here is why there is a need for data compression?
There are two primary reasons for the same.
You are getting the point!
Now coming back to the main topic, there are mainly two types of data compression techniques. Let’s discuss them.
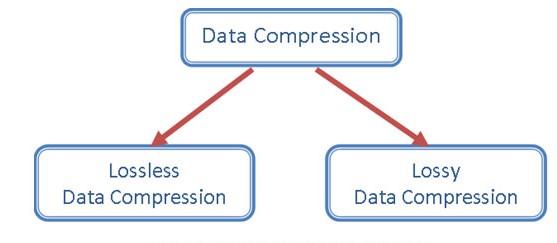
Lossy compression is a technique that involves the elimination of a specific amount of data. It helps in reducing the file size to a great extent without any noticeable thing. Also, once the file is compressed, it cannot be restored back to its original form as the data from the file is significantly reduced. This technique is much more useful when the quality of the file is not essential. Additionally, it helps to save much space on the disk to store the data.
Lossy compression is not useful when the quality of the file is essential. Besides, if there’s any further analysis to be processed on the record, this method is not ideal. This method is generally used for audio and video compression, where there is a significant amount of data loss, and even users cannot recognize it.
Example of lossy compression: JPEG image

“Compressed image (left) shows blocking artifacts compared to the original image (right) as a result of the JPEG compression scheme used.”
Lossless compression is a technique that involves only a certain amount of elimination of data. This technique also helps in reducing the file size, but not to the greater extent as that of lossy compression. Instead, in this method, if the file is compressed, it can be restored back to its original form. Further, the quality of the data is not compromised; hence, the reduction in size is not much.
Lossless compression is not useful when you want reduced size for extra storage. Also, if there is any further analysis to be performed on the file, lossless compression is not beneficial. It is useful for maintaing the originality of files by eliminating only unwanted data. This technique is commonly used for text files, sensitive documents, and confidential information.
Example of lossless compression: PNG image
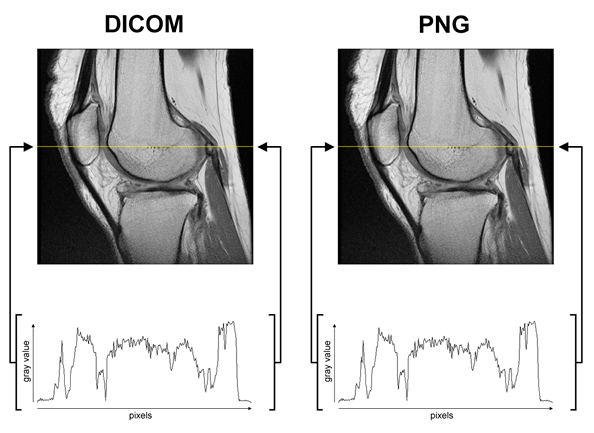
“The original image (left) is identical to the compressed image (right). It is represented by the identical graphs at the bottom that show the grey values for the pixels in each column is the same between the two images.”
| Basis | Lossy Compression | Lossless Compression |
| Definition | Lossy compression is a technique that involves the elimination of a specific amount of data. It helps in reducing the file size to a great extent without any noticeable thing | Lossless compression is a technique that involves only a certain amount of elimination of data. This technique also helps in reducing the file size, but not to the greater extent |
| Compression Ratio | High | Low |
| File Quality | Low | High |
| Elimination of Data | Even the necessary data is also removed which isn’t noticeable | Only some specific amount of unwanted data is removed |
| Restoration | Cannot restore its original form | Can restore its original form |
| Loss of Information | This technique involves some loss of information | This technique doesn’t include any loss of information |
| Data Accommodation | More data accommodation | Less data accommodation |
| Distortion | Files are distorted | No distortion |
| Data holding capacity | More | Less |
| Algorithms Used | Transform coding, DCT, DWT, fractal compression, RSSMS | RLW, LZW, Arithmetic encoding, Huffman encoding, Shannon Fano coding |
| File Types | JPEG, GIF, MP3, MP4, MKV, OGG, etc. | RAW, BMP, PNG, WAV, FLAC, ALAC, etc. |
Although both are the types of data compression, each can be useful under different situations. Like, lossy compression helps in reducing the file size, which means it is helpful to those who have vast amounts of data stored on the database. So, this technique is useful in storing the data with a much-diminished size. Also, for webpages files of such lower size is beneficial for faster loading.
Further, this process doesn’t allow any after analysis of the data once the compression is completed. Also, the file cannot be restructured in its original form as it involves the loss of data.
Unlike lossy compression, lossless compression doesn’t involve any loss of data. Neither the quality of data is compromised, nor the size of data is excessively reduced. It keeps the original format so it can be restored, and further operation can be performed. This method is helpful for those who need to access the data back again without compromising its quality.
Both lossy compression and lossless compression helps in the compression of data in their unique way. While lossy compression is useful to store data by compromising the data, lossless compression doesn’t. Lossless compression technique is beneficial for maintaing the originality of data, and lossy compression, on the other hand, doesn’t. Both the methods are helpful in database management, to identify and compress files accordingly.
If there’s any other query regarding data compression or both the techniques of data compression, then let us know in the comment box below.
The post Difference between Lossy and Lossless Compression appeared first on The Crazy Programmer.
The CEO of a new start-up business might wonder if website security is really important and necessary enough to bother
If I’m the CEO of a start-up, why should I bother with Website Security? on Latest Hacking News.
Like every other thing connected to the internet, power plants are also vulnerable to cyber attacks. Recently, researchers caught numerous
Multiple RCE Vulnerabilities Found In Siemens Power Generation Plants on Latest Hacking News.
VISA has recently issued a cybersecurity alert for the residents of North America. VISA has noticed a wave of POS
VISA Alerts North America Regarding POS Malware Attacks On Gas Pumps on Latest Hacking News.
Apple has rolled out iOS 13.3 this week. With this iOS update, Apple has fixed numerous security bugs including AirDoS
Apple Patched AirDos Vulnerability With iOS 13.3 Along With Other Security Fixes on Latest Hacking News.
Google has been working for quite some time to provide improved security features to Chrome users. Earlier, they launched better
Google Chrome 79 Is Out With Password Protection And Anti-Phishing Measures on Latest Hacking News.
If yous is like most ecommerce businesses today, you’ve probably used modern technology like automation, cross-platform integration and artificial intelligence
How to Protect Your Business Against Cyberattacks in the Age of Digital Transformation on Latest Hacking News.
Every device that we own that connects us with the digital world has a system within it that helps connect
Integrate Linux Software with Your IOS Devices on Latest Hacking News.
This Tuesday, Microsoft has rolled out a final scheduled updates for the year 2019. With the December Patch Tuesday bundle,
Microsoft December Patch Tuesday Addressed Zero-Day Under Active Exploit on Latest Hacking News.
ESET's Cybersecurity Trends 2020 report is out – New Chrome feature boosts account security – Hundreds of thousands of birth certificate applications leaked online
The post Week in security with Tony Anscombe appeared first on WeLiveSecurity
The second authentication factor might be a minor inconvenience, but it provides a major security boost
The post 2FA: Double down on your security appeared first on WeLiveSecurity